Contents:
A network detection rule/signature provided by NCCgroup concerning CVE-ID CVE-2019-0708, which occurs in RDP implementations down to Windows XP, has just been released.
Our experts have credible intelligence to support that this vulnerability could be exploited in less than a week, potentially producing the same amount of damage as we have seen in the case of self-replicating code like WannaCry and the older Conficker worm.
As per our intelligence, 8.5% of machines are vulnerable to the attacks. Based on this data, we conclude the impact it could have on organizations worldwide would be devastating.
Our Research & Intelligence team, which monitors underground fora and dark market services, has observed several offers for sale of functional exploit code. One of these offers, in particular, comes from a person who had previously sold 0-day vulnerabilities on the dark market.
We are already in possession of the functional exploit code and we can confirm that it works scarily reliable against vulnerable installations/services.
How does the exploit work and how critical is it?
Although Microsoft has stopped offering support for Windows XP and other older versions since 2014, they released a new patch on May 14, 2019.
Here is the list of vulnerable operating systems:
- Windows 2003
- Windows XP
- Windows 7
- Windows Server 2008
- Windows Server 2008 R2
If exploited, a remote code execution bug in RDP would allow hackers to run code on machines using RDP without them having to authenticate. Once an attacker breaks into a computer this way, they have full control over the machine – no login credentials needed!
The simple fact that you are running RDP could mean the gates to your system are wide open.
This vulnerability could allow access to worms, which are pieces of malware that have the capability to replicates themselves across a network.
We’ve noticed this happen in the past with attacks such as WannaCry and NotPetya and most probably, this RDP vulnerability will lead to another similar cyber disaster.
WannaCry was a ransomware worm that spread around the globe in 24 hours, infecting around 300 million computers in 150 countries at an alarming pace. The National Health Service (NHS) in England and Scotland was one of the first companies affected, and other major victims included Telefonica, Renault, and Fed-Ex.
What’s even more concerning is that the NotPetya outbreak followed shortly after, probably fueled by to the it-will-not-happen-to-me mentality and by people not taking matters like these seriously. NotPetya was based on the same EternalBlue exploit, and the activity of giant organizations such as Maersk and Ukraine’s central bank was disrupted.
This proves the lack of regular patching of outdated systems and people not learning their lessons remain fundamental problems.
Here is the security guide you need to follow
Since we’ve already witnessed the rapid pace these types of infections can spread, we would like to offer you some recommendations so you can stay safe.
We recommend that you apply these security measures as quickly as possible since the outbreak could start sooner than anyone would expect.
- Patch as soon as possible
We recommend all of our customers to create a current overview of available RDP services and make sure that they must be securely patched.
At the same time, we recommend a stronger and prioritized focus on all RDP services that are exposed to externally.
What you need to do if for certain reasons you are not able to patch your machines immediately:
- Implement IP restrictions that would prevent global access towards RDP services, no matter whether LAN or WAN.
- Enable Network Level Authentication (NLA). This puts another form of authentication in front of RDP, which makes it more difficult for intruders to log in.
- Turn off RDP. Obviously, this would not be an option if your business cannot run without it.
Be part of the solution, not part of the problem and act quickly.
Here you can also find the network signatures.
[UPDATE May 23, 2019]
A scanner has been released that can detect vulnerable RDP services on one or multiple hosts in a network with available RDP service. The tool can be found on GitHub and it can be used to locate and verify whether an RDP service is vulnerable to the exploit code.
A scanner module has also been released for Metasploit.
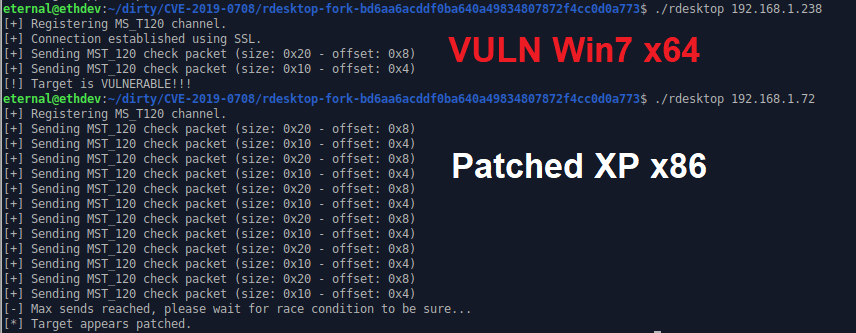
Source: GitHub
How dangerous is it?
The tool does not allow hackers easy access to vulnerable hosts. Altering this PoC to determine the denial-of-service can open the path to accessing machines, but this does require some effort.
However, it seems to be accurate for testing and it is useful for system administrators to identify vulnerable machines.
This is a PoC and should only be used for testing and not against targets without their permission.
*This article features cyber intelligence provided by CSIS Security Group researchers.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










