Contents:
The FBI and CISA revealed in a new joint security advisory that the Cuba ransomware gang raked in over $60 million in ransoms as of August 2022 after breaching more than 100 victims worldwide.
This is a follow-up to another advisory issued one year ago, which warned that the cybercrime group compromised dozens of organizations from U.S. critical infrastructure sectors, making over $40 million since it started targeting U.S. companies.
The number of U.S. entities compromised by Cuba ransomware has doubled following the December 2021 FBI Flash report, which noted that ransomware attacks were on the rise.
FBI has observed Cuban ransomware actors targeting U.S. entities in five critical infrastructure sectors: Financial Services, Government Facilities, Healthcare, Public Health, Critical Manufacturing, and Information Technology.
According to the FBI’s estimations, hackers from Cuba have compromised over 100 entities across the globe. In addition, they’ve collected at least $60 million in ransom payments out of a total of $145 million so far.
The FBI says that since the start of the year, the ransomware gang has been linked to new tactics and techniques. They have been identified with links to RomCom’s Remote Access Trojans (RATs) and Industrial Spy ransomware, as BleepingComputer first reported in May.
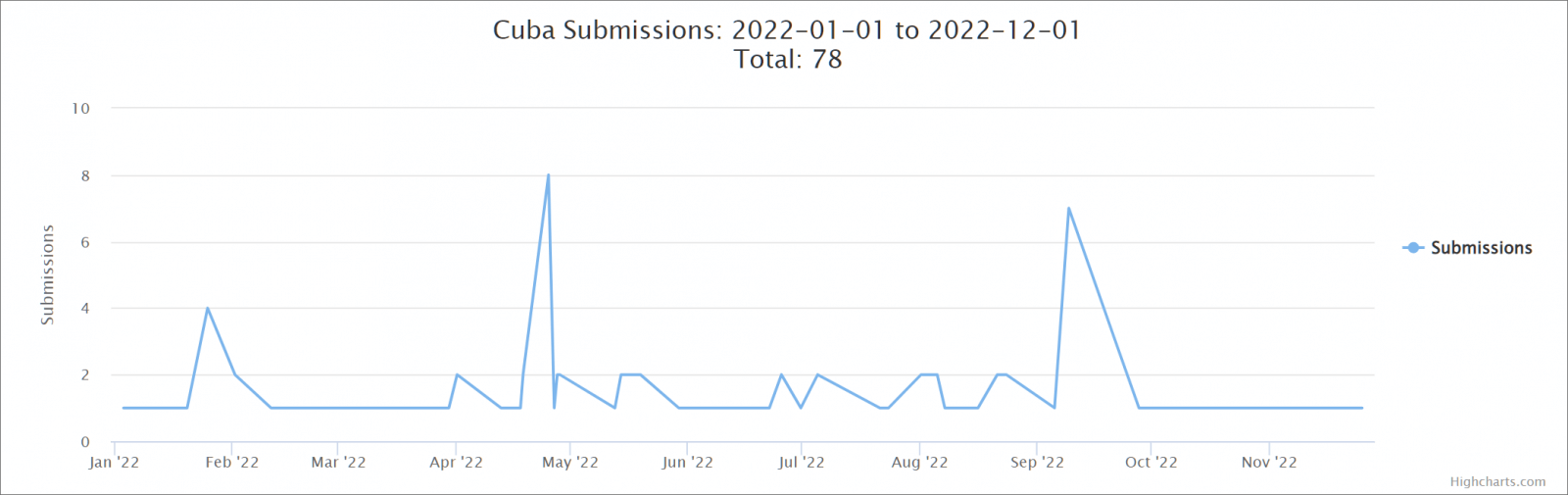
Advisory paints a grim picture, but samples submitted to the ID-Ransomware platform for analysis show it’s not very active. Unfortunately, this means that even if the ransomware weren’t very busy, it would still impact its victims.
The Age Of Malware In The Digital World
Cuba ransomware payloads are being delivered through Hancitor, which gives the operators easy access to previously compromised enterprise networks.
The Hancitor malware downloader has been known to drop information stealers, Remote Access Trojans, and other types of ransomware onto infected systems.
Cybercriminals use various methods to deliver malware, including phishing emails, stolen identities, Microsoft Exchange exploits, and Remote Desktop Protocol (RDP) tools.
After gaining a foothold on infected devices within their targets’ networks, Cuban ransomware threat actors deploy payloads remotely and encrypt files with the “.cuba” extension.
In their recent advisory, the FBI asked for help detecting Cuba ransomware activity. If your network is experiencing Cuban ransomware, please contact your local FBI Cyber Squad.
Information that might be helpful to identify ransomware gang members includes “boundary logs showing communication to and from foreign IP addresses, a sample ransom note, communications with ransomware actors, Bitcoin wallet information, decrypt files, and a benign sample of an encrypted file.”
The FBI urges ransomware victims not to pay, explaining that there is no guarantee that it will prevent data leaks and cyberattacks in the future. Victims are encouraged to contact their local FBI field offices as soon as possible after an attack.
Organizations at risk of being a victim of this ransomware operation should ensure they have patched known vulnerabilities, trained their employees and users to spot and report phishing attacks and enforce MFA across their environment.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








