Contents:
You may recall that only a few days ago, the DeadBolt ransomware group began encrypting QNAP NAS systems all over the world, claiming that they were doing so in order to take advantage of a zero-day vulnerability in the device’s software.
Customers using QNAP realized that their files had been encrypted and that their file names had been prefixed with the.deadbolt file suffix, when the assaults first started to take place.
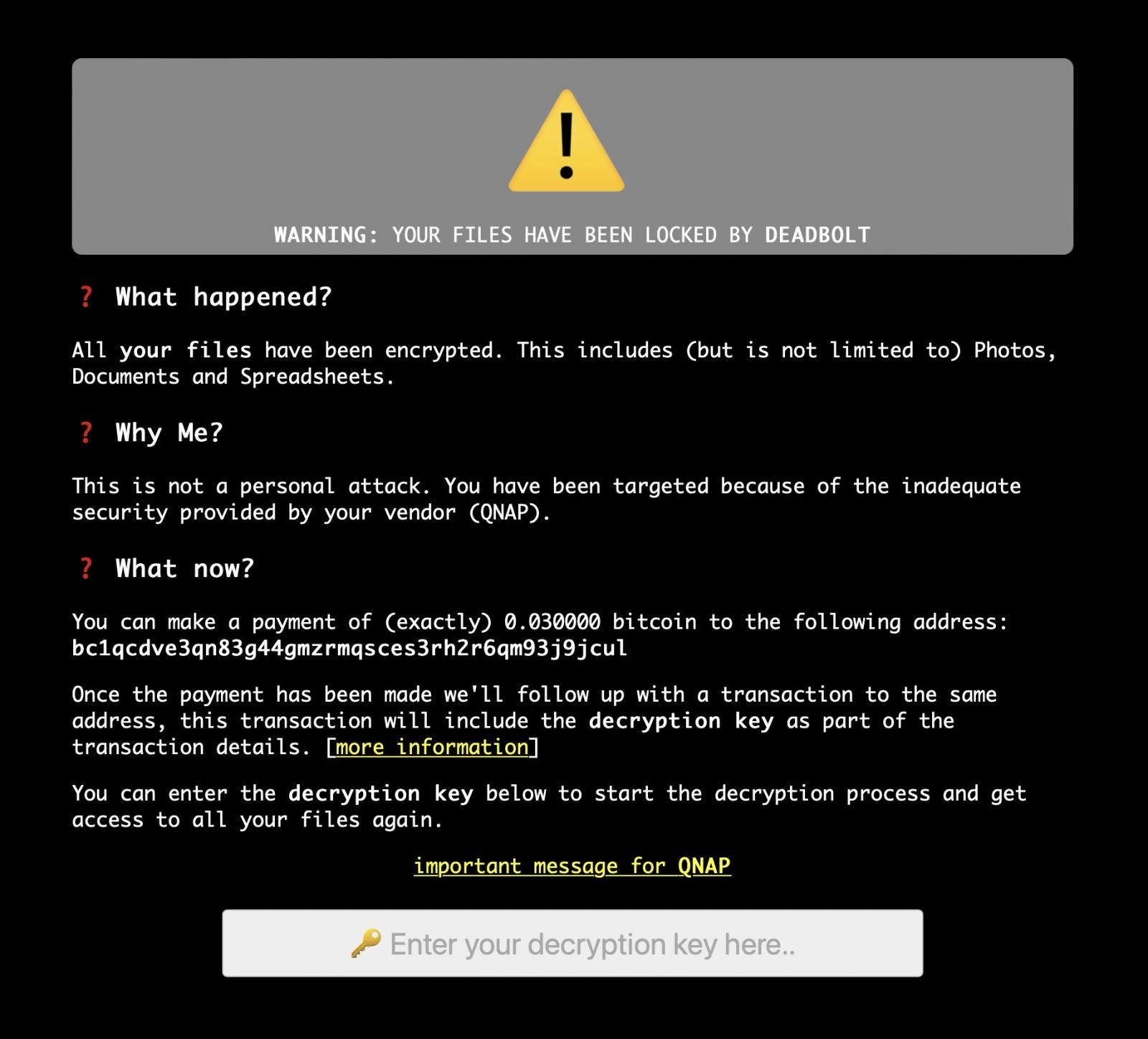
The threat actor claims to be using a zero-day vulnerability to hack into QNAP devices and encrypt data with the DeadBolt ransomware, which appends the.deadbolt suffix to file names once they have been encrypted.
How Is Qnap Dealing With the Situation?
QNAP has forced Network Attached Storage (NAS) devices to be upgraded with software that contains the most recent security patch in order to protect its customers from the DeadBolt ransomware.
A day after becoming aware of the assault, QNAP issued a warning to clients, advising them to protect their Internet-connected NAS systems from DeadBolt by upgrading to the most recent QTS software version, deactivating UPnP, and turning off port forwarding.
Soon after issuing the warning QNAP took a more drastic step and forced all customers’ NAS devices to be updated to version 5.0.0.1891, which was the most recent universal firmware released on December 23rd, 2021, according to the company.
A number of security updates were added in this version as well, but almost all of them are connected to Samba, which is unlikely to have been the target of this assault.
Some customers discovered that their iSCSI connections to the devices were no longer functional following the upgrade, indicating that the update did not proceed well.
Further investigation revealed that other customers who had acquired the decryption key and were in the process of decrypting discovered that the firmware upgrade also deleted the ransomware executable and the ransom screen that had been used to commence decryption. This stopped them from continuing the decryption process after the device had completed its update process.
As reported by BleepingComputer, an official QNAP support agent responded to several concerns about the company requiring customers to upgrade their firmware, explaining that it was necessary to safeguard consumers from the continuing DeadBolt ransomware assaults.
We are trying to increase protection against deadbolt. If recommended update is enabled under auto-update, then as soon as we have a security patch, it can be applied right away.
Back in the time of Qlocker, many people got infected after we had patched the vulnerability. In fact, that whole outbreak was after the patch was released. But many people don’t apply a security patch on the same day or even the same week it is released. And that makes it much harder to stop a ransomware campaign. We will work on patches/security enhancements against deadbolt and we hope they get applied right away.
I know there are arguments both ways as to whether or not we should do this. It is a hard decision to make. But it is because of deadbolt and our desire to stop this attack as soon as possible that we did this.
How Can Heimdal™ Help?
Ransomware is one of the most dangerous threats to business-critical assets nowadays. Keep it away with our Ransomware Encryption Protection tool, which protects against malicious encryption attempts while a ransomware attack is going on, making sure that your business does not become a victim of data loss and exfiltration.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










