Contents:
A new variant of Punisher ransomware was discovered recently. The malware spreads through a fake COVID tracking application and its victims are users from Chile.
The threat actors still take advantage of the victims’ need to track COVID-related information.
How It Works?
Cyble researchers unraveled the phishing website hosted at covid19[.]digitalhealthconsulting[.]cl. This fake site deployed ransomware disguised as a COVID tracking application.
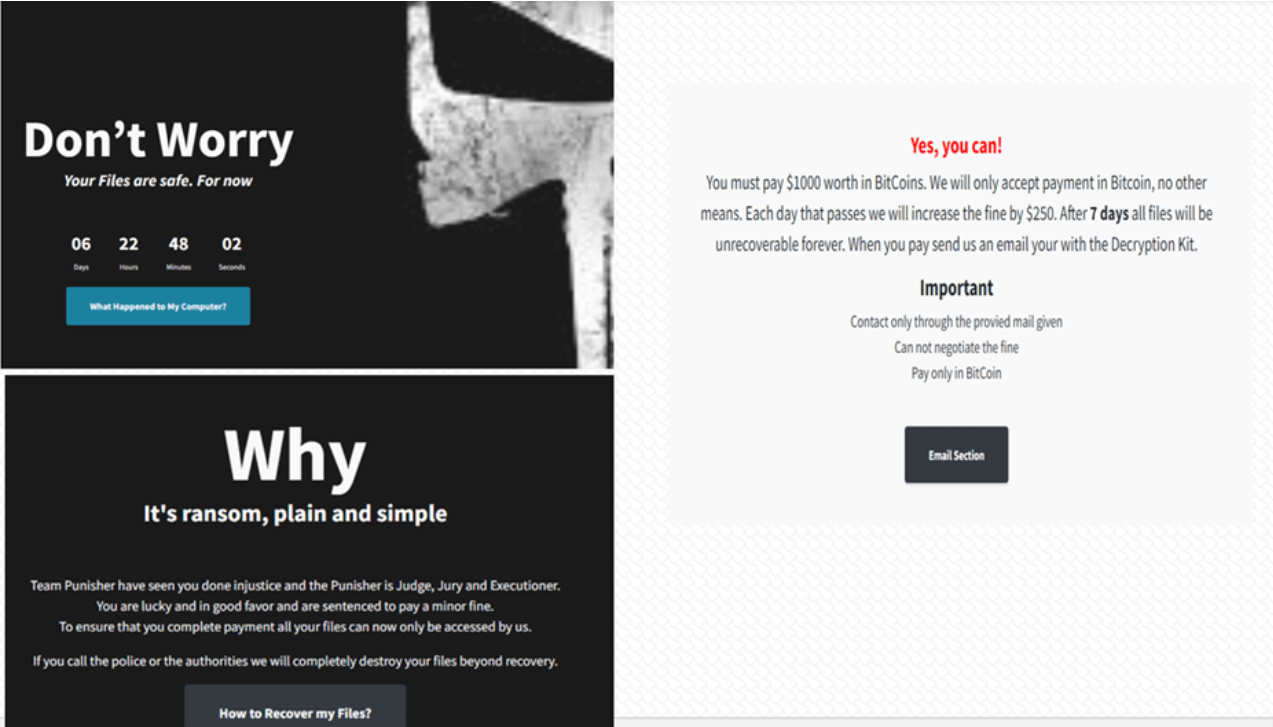
After infecting a system, the ransomware appends data to ransom notes such as System ID, unique identifier of each victim, BTC address for the ransom payment, date of infection, and JavaScript codes to start the timer, which will also increase the ransom amount after a specific timeframe.
Punisher ransomware utilizes a free template of a ransom note which is personalized by adding content specific to each of its targets.
The note is found in a file shortcut named “unlock your files.lnk” and demands the user to pay $1000 in Bitcoin for the decryption key.
Looking at its way of operating and the sum of money demanded from the victims, this strain of ransomware seems to be designed for individual users, rather than for large organizations
“The files encrypted by this ransomware can also be easily decrypted as it uses AES-128 symmetric algorithm for its encryption,” Cyble added.
How to Stay Safe from Punisher Ransomware?
To keep your device and data safe, you should follow the cybersecurity measures below:
- Download COVID applications or any kind of applications only from trusted sources.
- Do regular backups of your data and keep those backups on different devices, offline or on a separate network.
- Always update your software and systems on all your devices.
- Use strong security software on all your devices, including mobile
- Do not open any suspicious links or attachments if you can’t verify them.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







