Contents:
A hacking group dubbed Fail0verflow announced on Twitter that they have got the PS5 root encryption keys. These types of keys are usually used to perform PS5’s firmware decryption. Using these root keys could lead to the unlock of the gaming console, further resulting in homebrew software installation.
Hackers Have PS5 Root Encryption Keys: Details
They tweeted about this on the 8th of November, on Sunday evening, announcing having in possession the PlayStation 5 root keys.
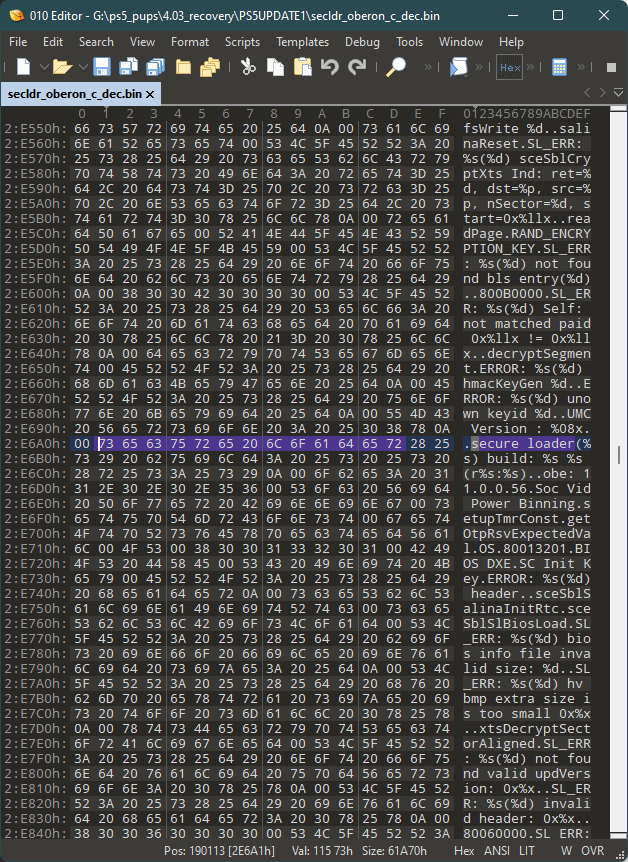
The picture posted on Twitter seems to contain data related to the PS5’s decrypted firmware. The code listed there seems to indicate some system’s secure loader. Decrypted firmware analysis could lead to code reverse engineering, allowing customized firmware creation. If this happens, they could use this to load homebrew software.
To extract the system software program of PS5 and the installing of a substitute can be done with the help of an exploit, as Cyware mentions. What this type of exploit would do is to provide a learn or write entry to the safe kernel of PlayStation 5.
The hacking group that made this announcement on Twitter did not give information on what exploit they used or if they used any. From the Tweet post, however, it comes out that a software program was used to gain access to these PS5 root encryption keys, indicating this way that no hardware modification had been performed.
PlayStation 5: A Second Hack in the Same Weekend
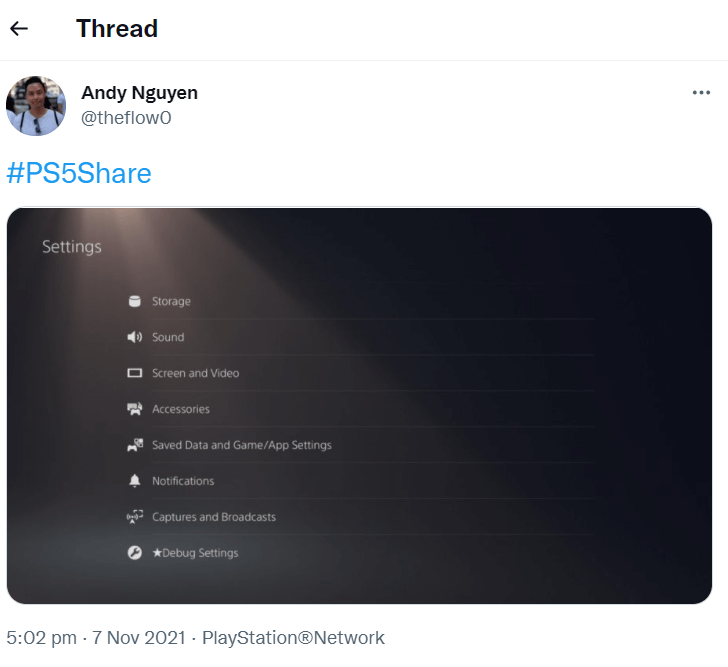
According to medium.com, in the same weekend, another announcement came on Twitter from Andy Nguyen, a Google security engineer also better known as theflow0, who published a print screen from where it comes out that PS5 was compromised. The posted picture indicates a list of usual PS5 settings among which one named “Debug Settings” can be noticed. This information allegedly indicated that theflow0 owns a PS5 kernel exploit.
As Wololo.net mentions,
The Debug Settings menu is a staple of testkit Playstation devices. This menu enables a series of QA/Dev related options on the console, including the possibility to Download/install package files. Although typically only present on testkits, the Debug Settings Menu is disabled on “retail” consoles. But it can be enabled on retail consoles by patching some flags, located at specific addresses in the firmware at Runtime. In other words, although the Debug Settings menu in itself is not a “hack”, having it showcased on a screenshot for a retail console is indicative that TheFloW has arbitrary write access on the console, meaning he’s most likely got a PS5 kernel exploit.
PlayStation Hack History
The PlayStation 5 was launched last year, but it seems that the latest Sony console is already vulnerable.
Another notable hack regarding PlayStation happened in 2011 that targeted PS3, 5 years later after the gaming console was launched. It was called the 2011 PlayStation Network Outage or the PSN Hack. The Play Station Network was used by PS3 owners and Playstation Portable machines.
As BBC was reporting at that time, the Sony enterprise confirmed that the cause of the outage was a hacking attack.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










