There are lots of privileged access management solutions out there. So, finding one for your organization should be as easy as one-two-three. The truth is things are not that simple.
PAM tools do play a key role in any modern cybersecurity strategy. They enhance sensitive data security and prevent hackers from moving through and using your system as they please.
But they can also hinder productivity and even cause security gaps if not properly implemented.
The Challenge of Choosing the Right Privileged Access Management Solution
Choosing the best privileged access management tools begins with thorough research.
Vendors aren’t always consistent about how they package and name products’ features. This makes it uniquely difficult to compare like for like.
So, let’s review some key privileged access management terms:
Privileged account and session management (PASM)
PASM is the standard suite of privileged access tools. Generally, it includes policies for:
- implementing secure access controls
- managing sign-ins
- governing privileged credentials
Single sign-on, multi-factor authentication, and password management policies all fall into this category.
Privilege elevation and delegation management (PEDM)
PEDM is a newer functionality and is increasingly common in the tools we list below. It allows organizations to:
- analyze real-time behavioral patterns
- detect anomalies
- offer ‘just-in-time’ access
This prevents privilege creep and standing privileges.
Secrets management (SM)
These tools allow organizations to store and manage privileged credentials safely. Privileged credentials include passwords, keys, APIs, and tokens.
Cloud infrastructure entitlements management (CIEM)
CIEM helps analyze and manage security in cloud environments. It enables automated scanning and identification of privileged users and service accounts.
Most PAM software vendors offer the traditional PASM feature set in a single main product. PEDM, SM, or CIEM functionalities come through add-ons, modules, or other solutions.
However, this isn’t always the case. You might end up buying multiple tools just to get all the standard PASM features. This is where the power of proper research comes in.
In this blog, I’ll focus on PASM features and only refer to the others when relevant.
Top 12 Privileged Access Management Software Platforms
There are lots of good PAM options and each has pros and cons. The difference is mostly in the breadth of features, the ease of use, and the final cost.
Here are my top 12 picks:
Heimdal®
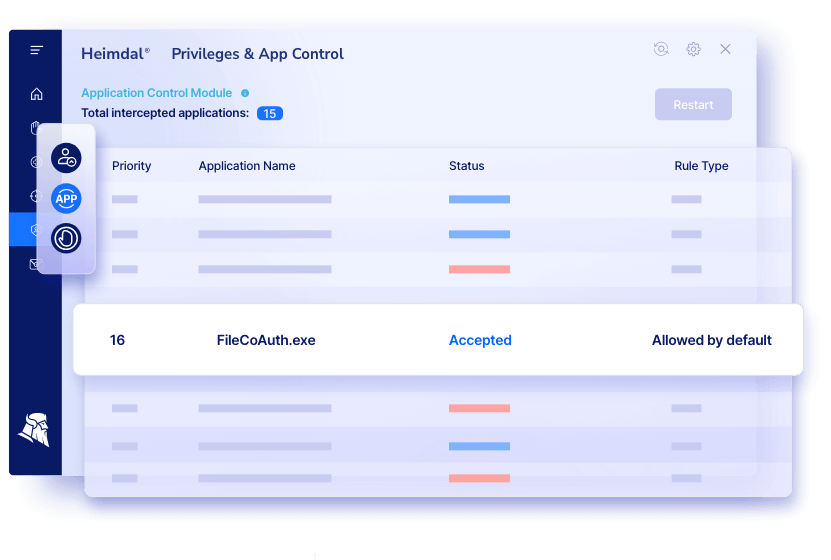
Heimdal®’s Privileged Access Management solution offers unparalleled control and flexibility to System Administrators, security teams and other IT professionals.
The module combines access management, privileged account and session management, and application control functions. The line-up proactively secures your environment and ensures compliance with industry standards like:
- Cyber Essentials
- NIS 2
- HIPAA
- PCI-DSS
- ISO 27001, etc.

Moreover, it helps in boosting the productivity of users and admins while being completely transparent.
Heimdal® Top Capabilities
- Total privilege management. Defines and manages role-based access control and delegation policies with ease. Supports implementing the principle of least privilege (PoLP)
- Threat-responsive rights management. Combined with Heimdal’s Next-Gen Antivirus it is the only software on the market that auto-deescalates user rights upon threat detection.
- Just-in-Time secured privilege access. By adopting JIT access to grant temporarily enhanced privileges to users, when necessary, you reduce the attack surface and mitigate the risk lateral movement.
- Enterprise credential vault. Heimdal’s PASM tool stores connection passwords safely to ensure safe credential management.
- Reporting and compliance. Generate comprehensive reports, monitor privileged access/session activities, and easily prove adherence to local or global regulatory standards.
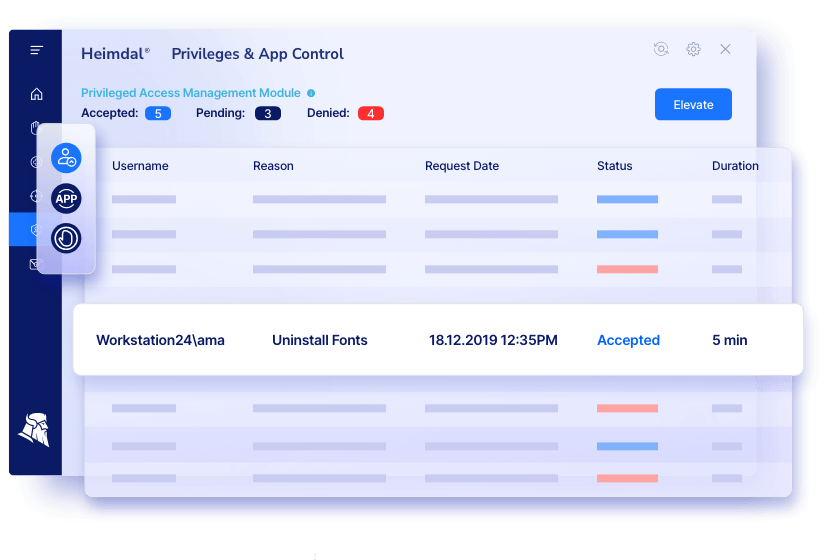
Pros
- Heimdal®’s PAM suite is modular and infinitely customizable. You can set filters, create white and blacklists, engage passive mode as defined by admins, and more.
- User-friendly interface.
- Heimdal® incorporates easy to enable Passive Mode for system indexing.
- Easy to enable auto-approval flow with defined rules and automatic de-escalation on threat.
- Heimdal® lets you expand your suite with cross-functional modules. You can control all of them in a single interface and dashboard.
For AD (Active Directory), Azure AD, or hybrid settings, Heimdal®’s Privileged Access Management enables PEDM-type non-privileged user account curation features.
The PAM solution under PEDM permits the maintenance of administrative rights for particular users and/or domain groups linked to particular endpoints or groups. Its Time-to-Live (TIL) function serves as a Just-in-Time (JIT) system.
Cons
As of now, Heimdal®’s solution is unable to send notifications in real time when user activity anomalies occur. The administrators must consider each request individually before determining whether or not to approve it.
Heimdal® Pricing
Heimdal®’s pricing for its solution depends on the size of the company and the number of managed endpoints. Book a personalized demo and get a custom price offer!
JumpCloud: Directory Platform
JumpCloud describes itself as “a single seamless solution for IT, HR, and security, that your users will love.”
The company offers several tiers of PAM and IAM tools, running from individual features to the full package. The most popular option is the “Directory Platform”, which showcases a wide range of PAM features.
JumpCloud Capabilities:
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Single sign on & IAM – Users report an effective and easy-to-use sign on experience.
- User and device management – Another popular feature due to the simplicity of managing multiple users and devices.
- Ease of use – The UI and overall navigation are intuitive and easy to use.
Cons:
- Limited Mac MDM support – The mobile device management (MDM) in Mac environments isn’t as extensive as in other operating systems.
- Lack of technical documentation – JumpCloud’s documentation isn’t as extensive as other providers’.
- Reporting/auditing – Some users have also asked for better tracking, auditing, and reporting features, for compliance reasons.
JumpCloud Pricing:
- Individual features: From $2 /user/month (Billed annually)
- Core Directory package: From $11 /user/month (Billed annually)
- PlatformPlus: From $18 /user/month (Billed annually)
JumpCloud has a sliding pricing scale. Users can choose individual features for $2-$5 each a month. For example, the password manager alone would cost $3 per user/per month.
There is also a free version of the full platform. It supports a maximum of 10 users and devices and includes 10 days of premium in-app support.
CyberArk: Privileged Access Manager
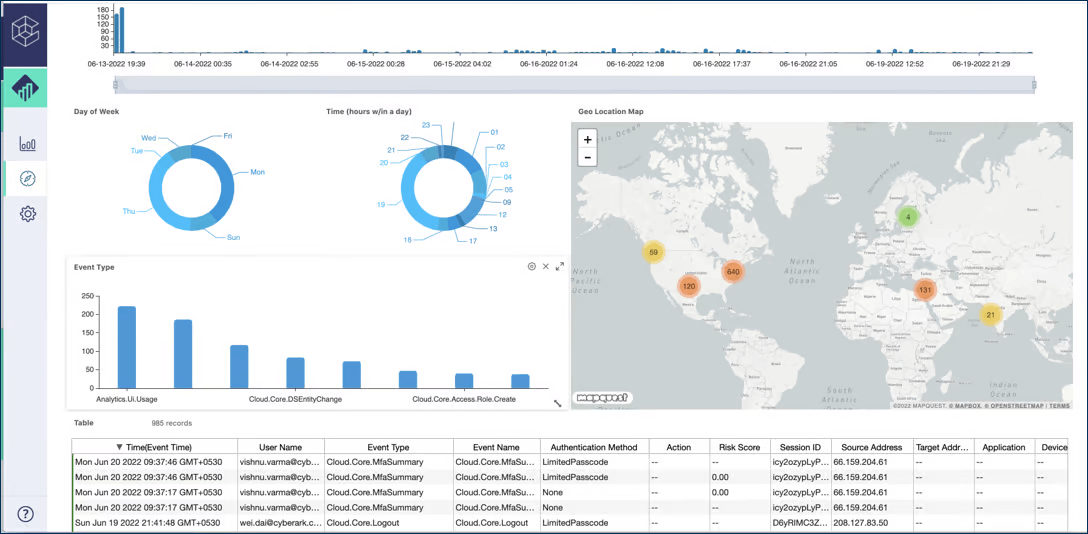
CyberArk is the oldest player in the PAM scene, with over two decades on the market. They’ve brought several innovations to the market, including vault technology, secrets management, and CIEM functionality.
But with scale comes challenges. The pricing and ease of use of CyberArk products, for instance, are cited as drawbacks. At the same time, some legacy features like privileged session management (PSM) now lag behind competitors.
The majority of CyberArk PAM features are available through their main product, Privileged Access Manager. Customers can also extend its features through separate services, such as:
- Identity Governance and Administration
- Secrets Management
- Endpoint Privilege Security (For PEDM functionality)
This may also cause confusion for some customers looking for a simpler, all-in-one solution.
CyberArk Capabilities
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Market scale – CyberArk’s size and market share means it has a large partner ecosystem and a wide range of integrations with other relevant technologies.
- Features – CyberArk offers a broad range of modern cybersecurity features, including just-in-time (or ‘just enough’) access, CIEM, secrets management, and more.
Cons:
- Product complexity – CyberArk products can be difficult to manage and upgrade. Users may also struggle to distinguish between their overlapping suite of features and solutions.
- Privileged session management – Some features like PSM struggle to match the output of smaller, more dynamic competitors.
- Pricing – CyberArk products are consistently placed at the top end of the PAM market.
CyberArk Pricing:
CyberArk does not publish its pricing details, and prospective customers are encouraged to book a demo to find out more.
That being said, reviews consistently place CyberArk among the most expensive products on the market. G2 gives it 3/4 stars for pricing, and user reviews suggest it is roughly 22% more expensive than the average PAM solution.
ManageEngine: PAM360
ManageEngine Capabilities:
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Pricing – ManageEngine’s pricing is generally considered lower than market average.
- Scale – The company’s customer base is distributed across multiple global regions, including EMEA, North America, and Asia Pacific.
- Discovery – PAM360 has extensive discovery capabilities to identify privileged users and service accounts across systems, databases, infrastructure, networks, etc.
Cons:
- Session management – Though some session management capabilities are available, the full functionality is only available through a resource-heavy HTML5 browser session emulation.
- PEDM – Though PEDM is bundled into the main product (unlike competitors), its functionality is less extensive.
- Wider functionality – Features such as secrets management, CIEM, and privileged credential management tend to lag behind the competition.
ManageEngine Pricing:
ManageEngine does not publish pricing details for PAM360 or other products. Instead, prospective customers are encouraged to get a quote or schedule a demo through the website to find out more.
Public reviews do not mention pricing information, though according to Gartner’s 2023 Magic Quadrant report, Manage Engine’s pricing is now “consistently less than market average.”
miniOrange: Privileged Access Management (PAM)

miniOrange is an established provider in the IAM and cybersecurity space. Its Privileged Access Management tool is designed to secure and manage access to sensitive systems, applications, and data across cloud, on-premises, and hybrid environments. The platform supports use cases across industries such as healthcare, finance, government, manufacturing, and IT, and is often considered a cost-effective option for organizations of varying sizes.
The miniOrange PAM solution provides a broad set of features aimed at enabling centralized privileged access control, monitoring, and compliance.
miniOrange Capabilities:
-
Privileged account discovery
-
Granular access control
-
Just-in-time access management
-
Real-time session monitoring and control
-
Privileged Elevation and Delegation Management (PEDM)
-
Password vaulting, management, and rotation
-
Single sign-on (SSO)
-
Multi-factor authentication (MFA)
-
Integration with SIEM, IAM, and ITSM platforms
-
Compliance management
Pros:
-
Modern PAM feature set – miniOrange includes advanced capabilities such as JIT access, PEDM, real-time session monitoring, MFA, password rotation, and audit reporting.
-
Flexible deployment – The solution integrates with a wide range of enterprise applications (such as SAP, ServiceNow, and Salesforce) and supports cloud platforms including AWS, Azure, and Google Cloud.
-
Support – Customers note responsive support availability across different time zones.
Cons:
-
Some advanced features require upgraded licensing tiers.
-
Organizations with complex customization needs may require additional implementation support.
miniOrange Pricing:
Pricing is based on the number of admin and end-user accounts, with optional costs for custom configurations. Billing is available monthly, quarterly, or annually. More detailed information is provided on the miniOrange pricing page.
BeyondTrust: Total PASM
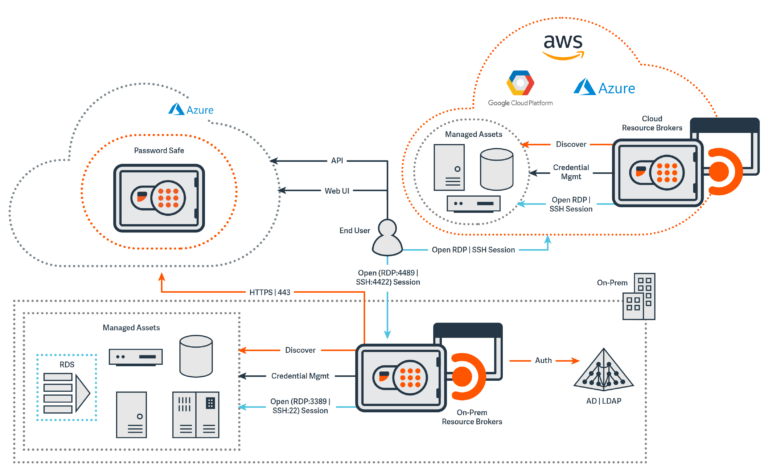
BeyondTrust is a PAM provider with global reach. Many of its customers are large global enterprises.
BeyondTrust offers two main products, known as Privileged Remote Access and Password Safe, which can be bundled together into the Total PASM package.
Privileged elevation and delegation management (PEDM) functionality is also available in a separate product called Privilege Management.
BeyondTrust Capabilities:
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- UNIX/Linux support – The UNIX/Linux support is often praised, with many considering this the go-to platform for these operating systems.
- Discovery – Users often cite the ease of use of the discovery capabilities as a key draw here.
Cons:
- Pricing – BeyondTrust products are generally priced at the top of the market.
- Multiple tools – Customers may also find costs and complexity rise as there are several different PAM products on offer, each with different features and use cases.
- Features – Tools such as single sign on, MFA, and PEDM aren’t available in the total PASM bundle. Customers may need to combine it with other BeyondTrust or third-party tools to achieve full coverage.
BeyondTrust Pricing:
BeyondTrust does not publish pricing details. Instead, prospective customers are encouraged to contact the sales team.
Public reviews do not mention pricing information, though according to Gartner’s 2023 Magic Quadrant report, Manage Engine’s pricing is “higher than market average.”
Okta: Privileged Access
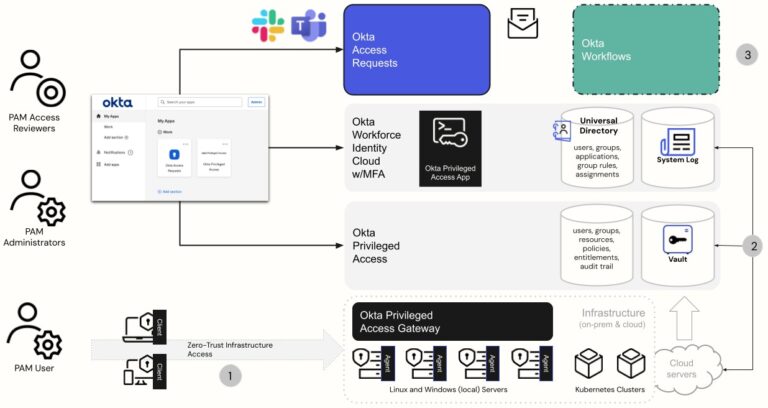
One of the newer entrants on this list, Okta is specifically designed for cloud-native organizations. Its main PAM offering, Privileged Access, comes as part of a wider suite of ‘Workforce Identity Cloud’ products. This includes tools offering multi-factor authentication, single sign-on, lifecycle management, and more.
The features in this list are based on capabilities available across all these products – though customers should be wary of the potential rising costs of multiple bundled subscriptions.
Okta Capabilities:
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Integration – Okta tools integrate well with each other and more traditional PAM software.
- Cloud-native – The suite of Workforce Identity Cloud tools is designed to work seamlessly in cloud, hybrid, or multi-cloud environments.
- Onboarding – Onboarding and offboarding of users are automated and therefore comparatively easy in Okta.
Cons:
- Auditing – Lack of auditing and compliance capabilities compared with other competitors is one key drawback.
- Expensive and complex – Okta’s resource-based pricing model can be difficult to understand, and the number of separate products on offer can also increase costs and complexity.
- No individual permissions – Unlike many PAM tools, you cannot govern and control access for individuals – only teams. This limits how granular the controls you implement can be.
Okta Pricing:
Okta’s Privileged Access product is available for $14 per resource unit/ per month, which roughly equates to the amount of compute power that the deployment will require.
Microsoft: Entra ID (Formerly Azure Active Directory)
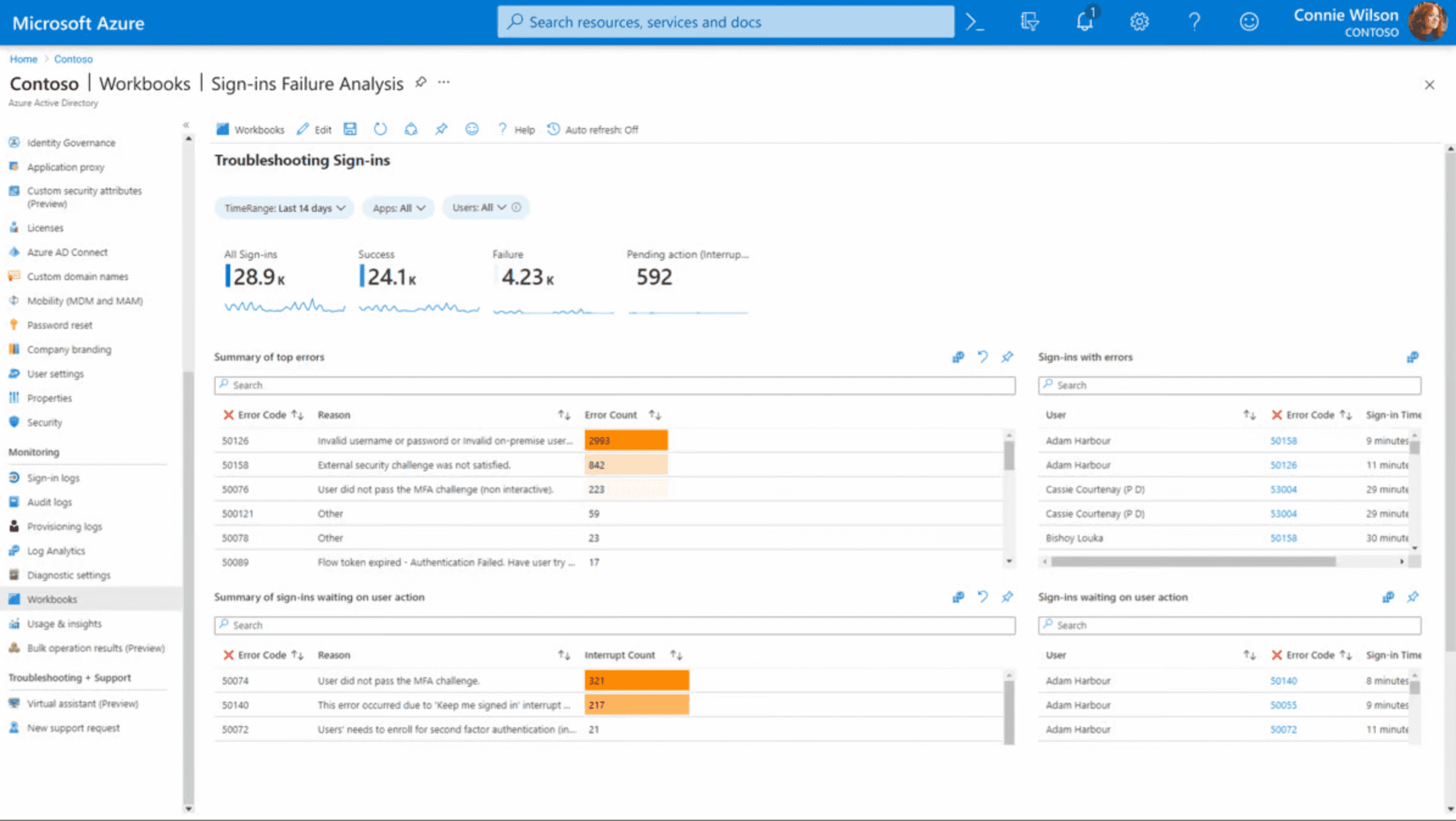
Microsoft Entra ID might seem like an unfamiliar name on this list. In fact, it’s actually just a new name for Microsoft’s Azure Active Directory. The new service was launched towards the end of 2023.
This is slightly different from other options on this list, as there’s a good chance you already have it. Any organization using Windows 11, Microsoft 365, or Azure services will effectively already have access to a basic Microsoft Entra ID package.
That’s because it acts as an extension of the existing identity and access management functionality all Microsoft customers already use to log in and authenticate.
Microsoft Entra ID Capabilities:
- Access control permissions
- Compliance management*
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Windows integrations – Microsoft Entra ID works well with other Microsoft technologies, making this an attractive choice for Windows-based organizations.
- Basic package – Microsoft offers a free package to all users and paid tiers to extend the functionality. This makes it easier to get started with these tools.
- Cloud security policies –Microsoft’s security tools work well for cloud and hybrid organizations. Users cite multi-factor authentication, conditional access policies, and password management as effective tools in this product.
Cons:
- Confusing features – It’s not instantly clear which features are available in different tiers of this product. Users may also struggle to work out how the different tiers interact with the Microsoft 365 and E5 packages – and by extension what features they already have and which they still need.
- User interface – Some users find the layout and UI of Entra ID less straightforward than third-party competitors.
- Microsoft only – Entra ID is an extension of the basic technology that all Microsoft 365, Windows, or Azure customers use. Non-Microsoft users will likely therefore find it less useful, and potentially confusing.
Microsoft Entra ID Pricing:
Microsoft Entra ID’s pricing information is publicly available on their website. The service includes three basic tiers of pricing model:
- Microsoft Entra ID Free: Free
This is effectively Microsoft’s default PAM suite, included as standard with cloud services like Microsoft Azure and Microsoft 365. It comes with basic authentication, single sign on, multi-factor authentication, and event logging capabilities.
- Microsoft Entra ID P1: $6.00 /user/month
The next tier up is available as a standalone product or included with a subscription to either Microsoft 365 E3 or Microsoft 365 Business Premium. Generally, it features more sophisticated versions of features from the free tier.
- Microsoft Entra ID P2: $9.00 /user/month
The premium tier includes advanced versions of most PAM features. Compared with P1, it includes more sophisticated end-user self-service and extra identity protection controls such as risk-based conditional access.
Customers of the Entra ID’s P1 and P2 tiers can also purchase a separate add-on:
*Microsoft Entra ID Governance: $7.00 /user/month
This is an advanced set of privileged access management capabilities to govern auditing and compliance. It adds extra features to Entra ID’s existing toolset, including an identity governance dashboard, lifecycle workflows, entitlement management with verified ID, and more.
WALLIX: Bastion
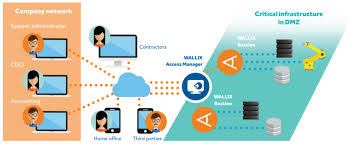
WALLIX is another long-standing player in the PAM market, having rolled out its original product in 2007.
Today, the standard suite of PASM functionality is covered by the main product: WALLIX Bastion. The company also offers PEDM tools through WALLIX BestSafe.
WALLIX Capabilities:
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Wide PASM capabilities – WALLIX Bastion offers a wide array of PASM tools, including features for session monitoring and auditing.
- Pricing – Though pricing is not publically released, it is generally considered to be competitive.
- Ease of use – Users report an easily navigable product and intuitive UI.
Cons:
- Lack of password rotation – Password rotation policies are not available for most machine or service accounts.
- Global reach – The customer base is generally confined to EMEA.
- Lack of discovery – WALLIX Bastion does not offer cloud infrastructure entitlement management (CIEM) functionality. This makes it less effective for organizations looking to automatically scan and identify privileged users and other identities.
WALLIX Pricing:
Like many providers on this list, WALLIX does not release its pricing information publicly. Potential customers are encouraged to get in touch to find out more. The vendor does, however, specify a series of pricing options:
- Perpetual license (+ 12-36 month maintenance subscription)
- Yearly license (+ 12-36 month maintenance subscription)
- On-demand (Monthly, + minimum 12-36 month maintenance subscription)
The software can also be purchased through cloud vendors such as AWS, Azure, and GCP.
Delinea: Secret Server
Delinea features a diverse set of security controls, though customers may be put off by the number of tools available. The standard set of PASM features (to manage privileged users and sessions) are available via the Secret Server product.
PEDM, secrets management, and CIEM functionality can all be added via additional tools, such as Privileged Behavior Analytics, Privilege Manager, and the Account Lifecycle Manager.
Despite the breadth of functionality, some users may find the overlapping functionalities between these products confusing.
Delinea Capabilities:
- Access control permissions
- Compliance management
- Password management
- Access management
- Credential management
- Single sign on
- Authentication
- Multi-factor authentication
- User management
Pros:
- Good for UNIX/Linux – Delinea has a competent product offering. In particular, users cite the PEDM functionality across Unix/Linux devices as among the best in the market.
- User experience – Customers generally note a smooth experience working with Delinea tools.
Cons:
- Overlapping products – Some users may find the range of products confusing – and costs may quickly rise when multiple solutions get bundled together.
- Functionality – Some common functionality is missing with Delinea, and users may find they need to install extra tools or configure PowerShell commands for features that are more easily available in other products. For instance, there’s currently no support for cloud infrastructure entitlement management (CIEM) and RDP session management requires additional tools to be installed.
- Service accounts – The functionality for managing service and machine accounts is less sophisticated than some other vendors on this list – particularly those involving local systems.
Delinea Pricing:
Delinea does not provide public pricing information for its Secret Server product. However, reviews suggest that it is among the more expensive products in the market. G2 user reviews rate it as 4/4 for expense, roughly 26% more than the market average.
ARCON: PAM

Like many providers on this list, ARCON has several different security tools available, which may cause confusion, including PAM Enterprise, Endpoint Privilege Management, My Vault, and Global Remote Access. The features discussed below are based on the PAM Enterprise product.
ARCON Capabilities:
- Password vault
- Virtual grouping
- Single sign on
- Ephemeral access
- Session monitoring
Pros:
- Features – Users and reviews suggest the functionality is generally above average when compared with other providers on this list.
- Password capabilities – ARCON features a sophisticated set of password management capabilities, including a secure password vault, frequent password changes, as well as multi-factor authentication, and single sign on.
- Auditing – The product also offers a detailed audit trail of privileged activities, complete with reports and analytics.
Cons:
- Interface – A common complaint from ARCON customers relates to the user interface, which isn’t as straightforward as some competitors.
- Customer base – ARCON’s customers are mostly based in Asia Pacific and EMEA, meaning it may be less attractive for US-based organizations.
- Product stack – There are several products available and it may be confusing to understand which are needed – and costs will likely rise as separate solutions are bundled together.
ARCON Pricing:
ARCON does not publish pricing information. Gartner considers its pricing to be ‘competitive’.
One Identity: Safeguard
One Identity aims to provide a unified approach to cybersecurity across a whole range of different products and features. Their PAM and IAM management tools are designed to integrate seamlessly with active directory, identity governance, and other tools – to provide a 360-degree approach.
The standard suite of PASM features is available through the Safeguard product. This splits into three modules, each of which can be purchased individually:
- Safeguard for privileged passwords
- Safeguard for privileged sessions
- Safeguard for privileged analytics
There are also a number of additional products and tools that businesses can add to this core package.
Examples include Active Roles which can provide just-in-time/just enough privileged access, and Identity, Governance, and Administration, which provides extended life cycle management and auditing capabilities.
One Identity Capabilities:
- Privileged session management & remote access
- Single sign on
- PAM lifecycle management
- Privilege elevation and delegation management
- Machine identity and secrets management
Pros:
- Ease of use – Safeguard is designed to be easy to use and users generally praise the product’s intuitive UI.
- Customer support – One Identity assigns an account and customer success manager to each account, making their overall customer support a real draw.
Cons:
- No CIEM functionality – One Identity does not offer CIEM tools, unlike other providers on this list. Instead, customers can access limited governance and auditing functionality through One Identity Governance & Administration – though this will generally be in addition to the main Safeguard product.
- Overlapping products – Even with the full suite of Safeguard modules, customers may find they have to add other One Identity products to get the full functionality. Active Roles, for instance, is required for just-in-time privilege access and the One Identity IGA tool boosts the auditing and governance functionality.
One Identity Pricing:
One Identity does not publish pricing, and no information is available to provide further details.
Getting the Right Tools for the Job
If you’ve made it this far, hopefully you understand a little more about the complex PAM landscape, and how you can distinguish between the confusing array of products and services available.
As is always the case in cybersecurity, there’s no one-size-fits-all approach.
Instead, it’s important to take the time to properly understand your needs and the specific tools you already have.
By doing that, you’ll be better placed to understand your requirements and which providers are best placed to fulfill them.
Choosing the right privileged access management solutions ensures your organization has the necessary security controls to protect critical assets while maintaining compliance and operational efficiency.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security






