Contents:
Please check out our latest piece of news that shares some new updates on the matter. PrintNightmare is actually a zero-day bug and Microsft provided mitigation measures until they release security updates. The news below describes the old updates present at that moment.
This news was updated clarifying that PrintNightmare Exploit is not a zero-day bug and it’s the same as CVE-2021-1675, because the latter was not fully patched by Microsoft.
Windows Print Spooler, the Windows software program whose job is to manage the printing process, has been recently subject to threats. A new exploit targets the Spooler file. A POC (proof of concept) on this topic has been mistakenly revealed by Chinese researchers, who brought to the public’s attention their input regarding the matter of a supposedly new zero-day bug. This happened because of confusing this threat called now PrintNightmare Exploit to CVE-2021-1675, another system vulnerability that has been investigated and patched by Microsoft on the 8th of June. Meanwhile, it was clarified that CVE-2021-1675 was not fully patched by Microsoft and left room for PrintNightMare that should not be treated as a zero-day bug, as initially believed. However, the leaking of information on PrintNightmare Exploit, in the hands of a threat actor, could lead to the whole system takeover.
PrintNightmare Exploit Is Actually the Same as CVE-2021-1675
The latest vulnerabilities discovered in Windows Print Spooler led to confusion among researchers and leaking of POC yet unintended for a public purpose, because of the lack of corresponding patches.
Thus being said, as BleepingComputer reports, the course of actions went as follows: firstly, Tencent, AFINE, NSFOCUS, and other researchers teams have come across CVE-2021-1675, a Windows Spooler vulnerability that went from a high-security exploit in Microsoft’s terms and indicated as a way for a hacker to use the rights access in a malicious way to a critical threat status that could lead to REC (remote code execution) allowing hackers to perform remote command on a user’s device.
Investigating this issue, QiAnXin researchers published their POC in a demo demonstrating how a hacker can use this to both perform REC and privilege escalation. The Sangfor Chinese Team was investigating this in parallel and seeing the demo posted by QiAnXin and the fact the Microsoft patched CVE-2021-1675, published their POC on another vulnerability named now PrintNightmare exploit with yet unreleased patches.
It was thought that CVE-2021-1675 and PrintNightmare are different because the latter seemed to be zero-day malware. In other words, this in hands of a hacker could lead to full system takeover and malware insertion in the Windows domains servers. The POC was taken down meanwhile, but the distributed info was already shared.
Meanwhile, it was clarified that Microsoft did not provide a complete patch for CVE-2021-1675. This means that PrintNightmare should not be treated separately, like a zero-day bug, as per Yunhai Zhang and Benjamin Delpy’s confirmations and it actually targets systems that are updated.
How Could PrintNightmare Exploit Affect Users?
The threat of the PrintNightmare Exploit is real. It could lead to:
- Being exploited through a malicious authentication;
- This allows a hacker to execute code at a system level on a remote domain controller leading to Active Directory domain controllers takeover.
- PrintNightmare does not pose a threat only to domain controllers;
- Any installation that Windows performs and that includes the Spooler Service can serve as a target.
What Can Be Done
Waiting for a patch for this newly discovered threat, you should:
- Disable the PrintSpooler on computers exposed to the threat. This can be done either from the Powershell script or from the Group Policy Settings;
- Limit network access on servers in absolute need of Print Spooler;
- Pay attention to Microsoft updates that will surely release a patch in the near future.
What Other Measures Have Been Taken?
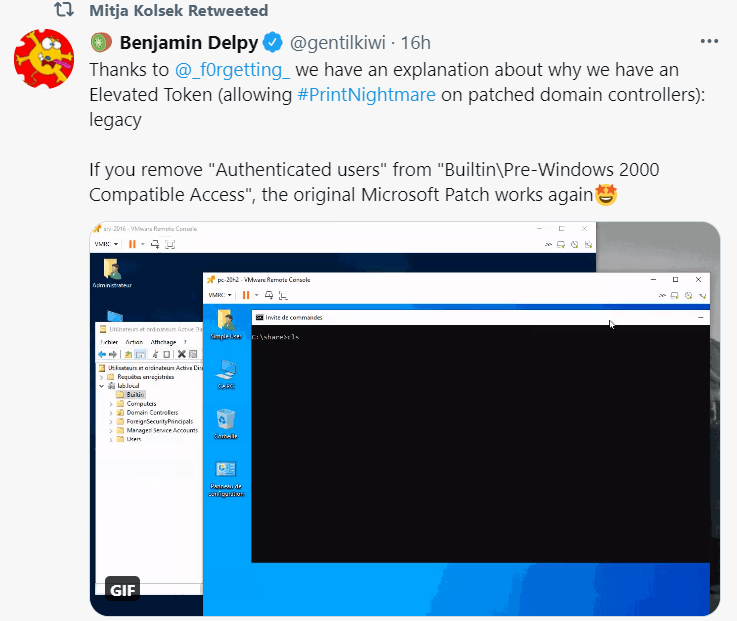
Other people are now investigating the issue. LARES company made public a Sysmon configuration file that can be used for telemetry purposes and a sample of the PrintNightmare attack, then Florian Roth used the Sangfor researchers’ discovery on the exploit to create some Sigma rules that can be used. Matthew Hickey and Benjamin Delpy also made some experiments. The first used a Windows Server 2019 Machine exposed to PrintNightmare exploit threat that was updated and managed to get full system privileges through a usual Domain User account and the latter could get REC on a system that was entirely patched. Therefore the current Windows updates do not stop the newly discovered PrintNightmare exploit and it is a real threat, until fixing it.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








