Contents:
Massive phishing operation employing hundreds of domains to steal Naver credentials reveals infrastructure overlaps associated with the TrickBot banking trojan.
What Is Naver?
Naver is a South Korean online platform run by the Naver Corporation. It made its debut in 1999 as South Korea’s first web portal to develop and use its own search engine.
The resources used in this cyberattack demonstrate the magnitude of the threat actor’s attempt to gather login data that can be used in further attacks.
Naver Corporation was the world’s first operator to introduce the comprehensive search feature, which compiles search results from various categories and presents them in a single page. Naver has since added a multitude of new services ranging from basic features such as e-mail and news to the world’s first online Q&A platform Knowledge iN.
Naver Users under Attack
Naver credentials, in addition to granting access to regular user accounts, can also allow access to enterprise environments due to password reutilization.
Earlier this year, cybersecurity experts at cyber intelligence firm Prevailion discovered a large-scale phishing campaign aimed at stealing Naver users’ credentials.
They began their investigation with a domain name shared by Joe Slowik, mailmangecorp[.]us, which led to a “vast network of targeted phishing infrastructure designed to harvest valid login credentials for Naver.”
While investigating the hosting infrastructure being used to serve the Naver-themed phishing pages, PACT analysts identified overlaps with the WIZARD SPIDER [a.k.a. TrickBot] infrastructure.
542 unique domains were associated with the campaign, 532 of which were used for Naver-themed phishing. They observed that the operator would register a set of domain names that resolved to a single IP address using an email address.
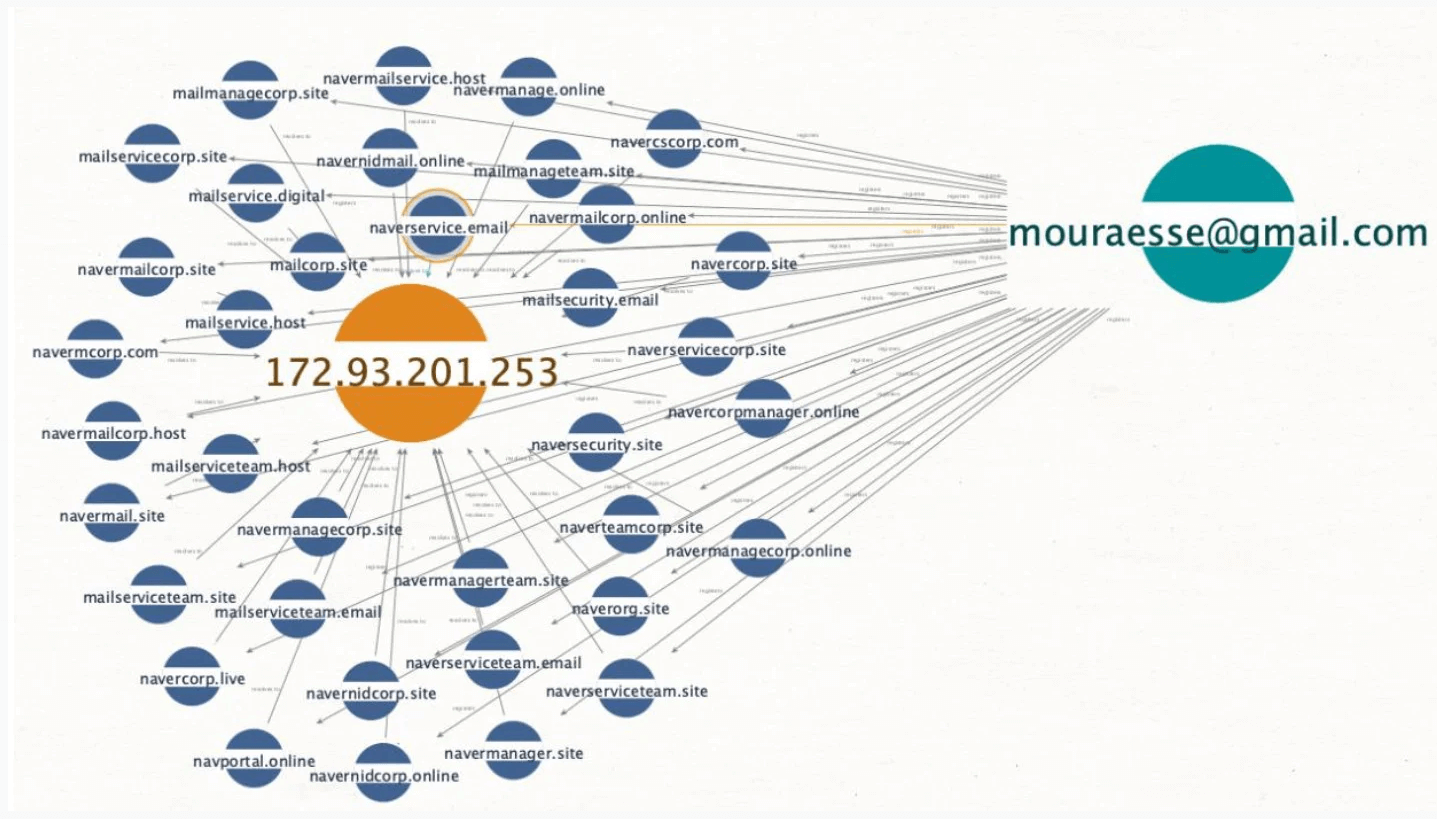
For the Naver operation, the attacker used multiple addresses to create registrant personas. According to BleepingComputer, the newest domains were registered in February, while the oldest ones were registered in August 2021.
The experts discovered that the domains resolving to the IP address in the image above were part of a redirect scheme (HTTP/302) that directed possible targets to bogus Naver platform login pages held on Hostinger.
Naver Phishing Operation in Progress
From the initial email address, the cyber intelligence company was able to discover another group of 58 phishing domains resolving to 23.81.246[.]131, an IP address that proved critical in establishing the initial connection between Naver credential phishing and the infrastructure linked with the TrickBot banking trojan.
Yesterday, Prevailion provided in a report additional indicators linking the Naver phishing domains to TrickBot infrastructure disclosed in public research from RiskIQ and Microsoft.
According to the researchers, everything indicates that the Naver phishing operation is still ongoing, as the infrastructure is still in use and multiple domains have been registered this month for this purpose.
The company added:
The Naver-themed phishing activity that was initially discovered does not appear to be the work of a ransomware group directly.
Nevertheless, these file-encryption cyberattacks are frequently preceded by phishing or credential-stealing operations carried out by associates or partners looking to gain access to systems of important targets.
How Can Heimdal™ Help?
Heimdal Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










