Contents:
According to a new study of over 10,000 malicious JavaScript samples, over 25% of the samples analyzed use JavaScript obfuscation methods to prevent detection and analysis.
What Is Obfuscation?
Obfuscation is a powerful technique used by hackers and security teams all over the world. Both parties use it for different reasons, but their goal is the same: to make the source code indecipherable, hard to understand, and interpret.
Obfuscation is a technique frequently used by cybercriminals in order to make it more difficult to examine malicious scripts and to thwart security solutions.
Frequent obfuscation methods include:
- Instruction pattern transformation;
- Metadata or unused code removal;
- Subroutine reordering
- Dummy code insertion;
- String encryption;
- Code transportation
Security researchers at cloud service company Akamai technologies have examined more than 10.000 malicious JavaScript samples including malware droppers, phishing pages, scammers, and cryptominers’ malware.
They noticed that more than 25% of the analyzed samples employ JavaScript obfuscation methods to avoid exposure. This percentage suggests that malicious actors who want to avoid detection continue to use obfuscation techniques.
As noticed by BleepingComputer, the majority of these obfuscated samples seem so to have similar code because they were bundled by the same packers, so their code structure appears to be similar even though the function is different.
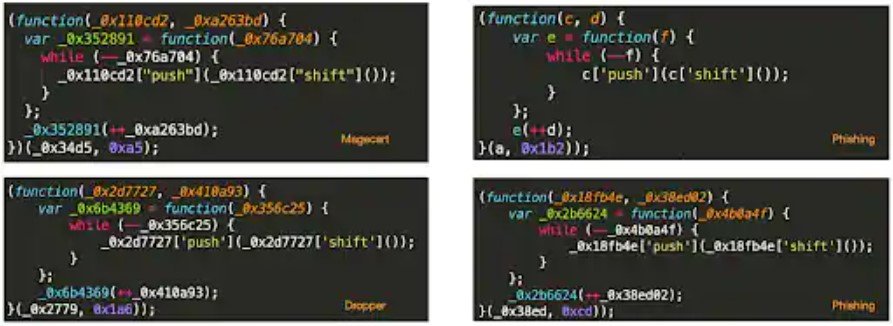
In the forthcoming SecTor congress, Akamai intends to present more information on how they concentrate their detection efforts on packing techniques rather than the file code itself.
Research that will be presented at the SecTor 2021 conference introduces a technique that profiles the unique functionality of packers to detect JavaScript prior to it being obfuscated, regardless of the original code. That way, any JavaScript code that represents a threat — like phishing, malware droppers, or scammers — will be detected based on the techniques the packer introduces.
Obfuscation Is Not All Bad
As explained in the report, JavaScript obfuscation isn’t used just for malicious activities. The analysis of the top 20,000 websites (according to Alexa.com) shows that at least 0.5% of files used packer obfuscation techniques.
According to the report, additional investigation reveals that the technique being used is the result of various legitimate scenarios, including:
- Websites that are attempting to hide some of their client-side code functionality;
- Code that was obfuscated by a third-party provider;
- The obfuscation of confidential data such as email addresses.
This evidence makes the difficulties in identifying malicious JavaScript easier to understand, as obfuscation alone does not imply the existence of malicious code.
The method of identifying malicious obfuscation necessitates more sophisticated machine learning techniques capable of distinguishing between malicious and benign obfuscated JavaScript.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security