Contents:
A recent phishing attack that was intercepting Zoom users to get their Microsoft exchange credentials was unraveled.
This email attack aimed at over 21,000 users targeting the National Healthcare Company and managed to bypass Microsoft Exchange Email Security (a mail and calendaring server used by millions of businesses around the world).
How the Attack Works
Researchers at Armorblox explained that “The email attack had a socially engineered payload, bypassed Microsoft Exchange email security, and would have been delivered to over 21,000 users if Armorblox had not successfully stopped this malicious email attack.”
The title of the phishing email was “[External] For name of recipient on Today, 2022”, including each victim’s name. Then, the email body stated that two messages are awaiting a response from the user.
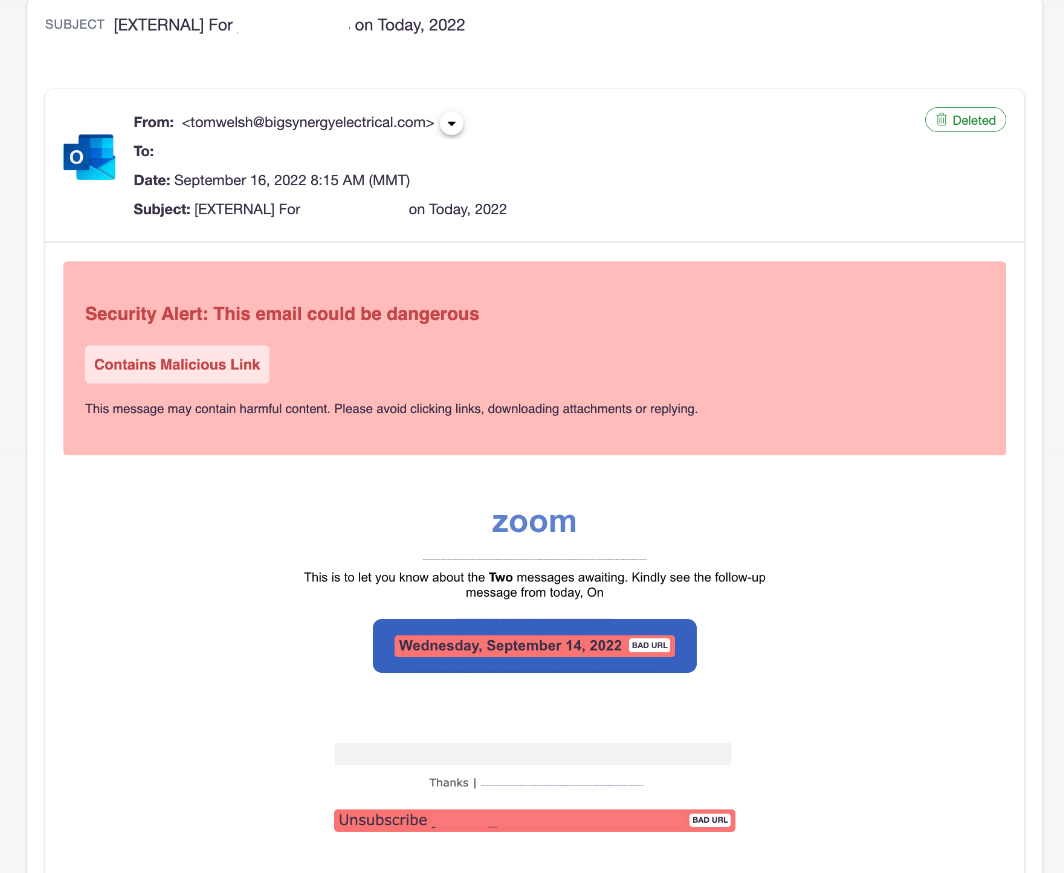
The email contained two malicious URLs, one was linked to the main call-to-action button, while the other served as a shadow unsubscribe link. The victim was directed to a landing page where Microsoft account credentials were requested.
To be trustworthy, the campaign used the Zoom logo and branding in the phishing email and a fake look-alike Microsoft login landing page.
The email included a Zoom logo at the top in order to instill trust in the recipient that the email communication was a legitimate business email communication from Zoom – instead of a targeted, socially engineered email attack.
The threat actors managed to bypass Microsoft Exchange email security controls using a valid domain with just one infection reported in the last 12 months. The domain passed all email authentication checks: DKIM, SPF, and DMARC.
How to Stay Safe
To safeguard your data and your business, there are a few steps you can take:
- Enhance native email security with layers of security that employ a significantly different approach to threat detection. In this way, you will be safe from spear phishing, business email compromise, or credential phishing attacks like this one.
- Be aware of social engineering cues instead of automatically executing emails coming from service providers. Examine the sender’s name, sender’s email address, the language within the email, and any logical inconsistencies within the email.
- Use multi-factor authentication on all accounts possible and password management software.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







