Contents:
Outlook and Thunderbird accounts are being targeted by a new info stealer malware known as StrelaStealer. The malware behaves as most info stealers do, meaning they attempt to steal data from various sources, such as browsers, cryptocurrency wallet apps, cloud gaming apps, the clipboard and so on.
Distribution and Execution
Earlier this month, researchers from DCSO CyTec first noticed what was previously an unknown malware, seemingly going after Spanish-speaking users. StrelaStealer enters the victim’s system following phishing attacks, via email attachments. For example, it can present itself as an ISO file containing the executable msinfo32.exe, that sideloads the malware via DLL order hijacking.
Another instance noticed by the researchers involved an ISO containing the LNK file Factura.lnk as well as an HTML file (‘x.html’), which is a polyglot file. This file can be treated as different formats depending on the application that opens it.
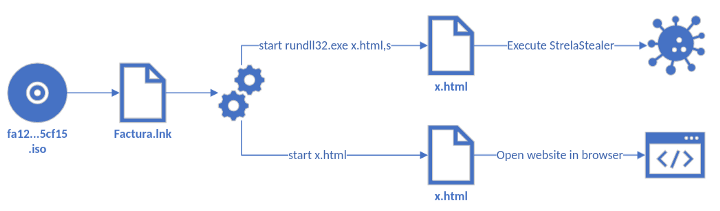
Execution of StrelaStealer via polyglot
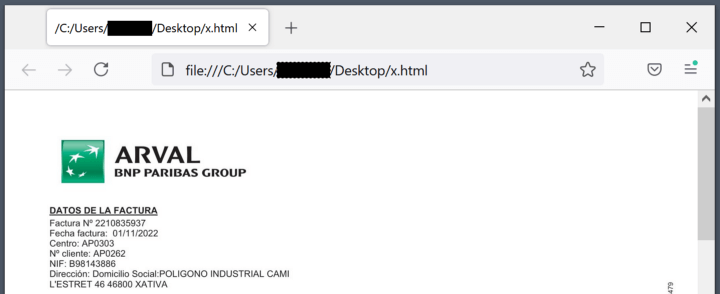
Upon executing the Fractura.lnk file,the x.html will execute twice, first using rundll32.exe to run the embedded StrelaStealer DLL and then as HTML to load the decoy document in the browser, meant to give legitimacy to the whole process.
StrelaStealer searches for the %APPDATA%\Thunderbird\Profiles\ directory, as BleepingComputer explains, looking for logins.json and key4.db, the password database, and exfiltrates their contents to a C2 server. In Outlook`s case, the malware reads the Windows Registry, retrieves the software’s key and then locates the IMAP User, IMAP Server, and IMAP Password. Because the IMAP Password contains the user password in encrypted form, the malware proceeds to use the Windows CryptUnprotectData function to decrypt it before further exfiltrating to the C2 server.
Next, StrelaStealer makes sure the C2 received the data by waiting for a specific response. If the response arrives, it quits, but otherwise it enters a 1-second sleep and repeats the routine.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







