Contents:
On Thursday, Microsoft revealed it has discovered a wide-scale malicious email campaign operated by Nobelium, the threat actor responsible for the SolarWinds attacks.
According to Corporate Vice President Tom Burt, Nobelium is currently conducting a phishing campaign after the Russian-backed group managed to take control of the account used by USAID on the Constant Contact email marketing platform.
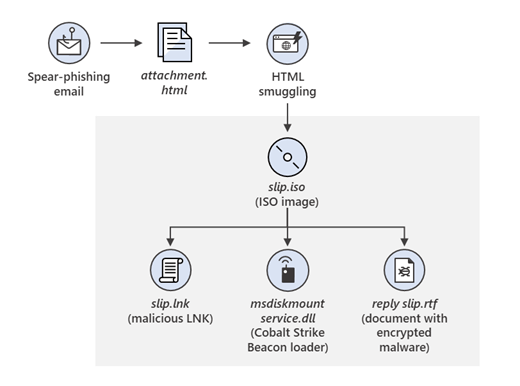
Example Flow of HMTL/ISO infection chain.
Image Source: Microsoft Threat Intelligence Center
This new wave of attacks targeted approximately 3,000 email accounts at more than 150 different organizations, including government agencies, think tanks, consultants, and non-governmental organizations.
Nobelium launched this week’s attacks by gaining access to the Constant Contact account of USAID. Constant Contact is a service used for email marketing. From there, the actor was able to distribute phishing emails that looked authentic but included a link that, when clicked, inserted a malicious file used to distribute a backdoor we call NativeZone. This backdoor could enable a wide range of activities from stealing data to infecting other computers on a network.
The tech giant added that most of the emails were blocked, and there is no reason to think the attacks involve any vulnerability in Microsoft products.
According to a post from the Microsoft Threat Intelligence Center, back in February, Microsoft observed how Nobelium was changing its approach to infect victim computers with malicious code.
In the May 25 campaign, there were several iterations. In one example the emails appear to originate from USAID <ashainfo@usaid.gov>, while having an authentic sender email address that matches the standard Constant Contact service. This address (which varies for each recipient) ends in @in.constantcontact.com, and (which varies for each recipient), and a Reply-To address of <mhillary@usaid.gov> was observed. The emails pose as an alert from USAID, as seen below.
Source: Microsoft Threat Intelligence Center
Once the victim clicks on the link, a malicious ISO is delivered that contains a decoy document, a shortcut, and a malicious DLL with a Cobalt Strike Beacon loader dubbed NativeZone. If the shortcut is run, the DLL is executed and Nobelium achieves persistent access to compromised systems.
The successful execution of these malicious payloads could enable Nobelium to conduct action-on objectives, like lateral movement, data exfiltration, and delivery of additional malware.
Nobelium is best known for the SolarWinds supply chain attack that provided hackers with access into as many as 18,000 government entities and Fortune 500 companies, as to at least nine federal agencies and more than 100 companies were exposed to the breach.
To reduce the impact of this threat, Microsoft recommends applying the following mitigations:
- Turn on cloud-delivered protection in Microsoft Defender Antivirus or the equivalent for your antivirus product to cover rapidly evolving attacker tools and techniques.
- Run EDR in block mode so that Microsoft Defender for Endpoint can block malicious artifacts, even when your non-Microsoft antivirus doesn’t detect the threat or when Microsoft Defender Antivirus is running in passive mode.
- Enable network protection to prevent applications or users from accessing malicious domains and other malicious content on the internet.
- Enable investigation and remediation in full automated mode to allow Microsoft Defender for Endpoint to take immediate action on alerts to resolve breaches, significantly reducing alert volume.
- Use device discovery to increase your visibility into your network by finding unmanaged devices on your network and onboarding them to Microsoft Defender for Endpoint.
- Enable multifactor authentication (MFA) to mitigate compromised credentials. Microsoft strongly encourages all customers download and use passwordless solutions like Microsoft Authenticator to secure their accounts.
- For Office 365 users, see multifactor authentication support.
- For Consumer and Personal email accounts, see how to use two-step verification.
- Turn on the following attack surface reduction rule to block or audit activity associated with this threat: Block all Office applications from creating child processes.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











