Contents:
It is not often that ransomware groups attack Russian corporate networks, however OldGremlin, also known as TinyScouts, is one of the few cybercrime gangs that primarily focuses on Russian companies.
Until now, OldGremlin were known to mainly target enterprise networks running on Windows, but researchers discovered their file-encrypting malware operations have expanded towards Linux machines as well.
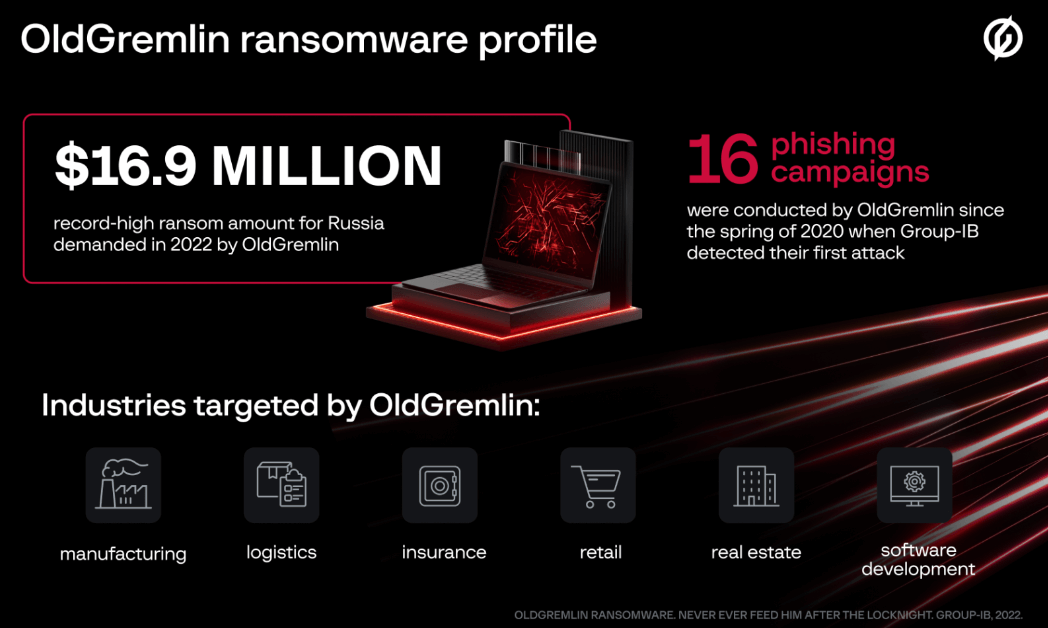
The Russian-speaking gang carried out 16 malicious campaigns in just over two years, mainly extorting Russian entities but that does not mean that organizations from other countries are completely safe.
OldGremlin Campaigns
Also going by TinyScouts, due to the names of the functions in the malicious code they use, OldGremlin is characterized by a small number of campaigns per year with million-dollar ransom demands. As an example, the largest ransom amounted to $4.2 million in 2021, and this year, it went up to $16.9 million.
According to BleepingComputer, the attacks are launched via phishing emails that impersonate well-known organizations – RBC media group, consultant groups, developers of management systems, lobby groups, Minsk Tractor Works, a dental clinic, financial entities, law firms, a company in the metals and mining industry.
In their report, the Singapore-headquartered cybersecurity company Group-IB states that OldGremlin has adapted their method this year. It also started with a malicious email but instead of distributing the initial stage payload directly through a malicious document, the attacker tricks the victim into downloading the document from a file-sharing service. Then, OldGremlin stays on the victim network for more than a month, collecting information that allows the discovery of high-value systems for encryption.
It is further reported that, once access is gained, OldGremlin hackers move to establish persistence by creating scheduled tasks, gaining elevated privileges using Cobalt Strike, and even the CVE-2020-3153 and CVE-2020-3433 flaws in Cisco AnyConnect, while also gaining remote access to the compromised infrastructure using tools such as TeamViewer.
OldGremlin has debunked the myth that ransomware groups are indifferent to Russian companies. According to our data, the gang’s track record includes almost twenty attacks with multi-million ransom demands, with large companies becoming their preferred targets more often.
Ivan Pisarev, Head of Dynamic Malware Analysis Team at Group-IB
OldGremlin struck again on August 23, 2022, with emails embedding links pointing to a ZIP archive payload hosted on Dropbox to activate the killchain. The self-developed toolkit list on which the threat actors rely on includes:
- a reconnaissance tool
- malicious LNK files
- multiple backdoors (TinyPosh, TinyNode, TinyFluff, TinyShell)
- tool to extract data from Credential Manager
- tool to bypass antivirus software
- tool to isolate a device from the network
- TinyCrypt ransomware
There is no exaggeration in saying that OldGremlin is a highly skilled and dangerous threat actor, which at any time might turn to organizations other that Russian-based ones.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









