Contents:
One of the world’s largest energy organizations, Saudi Aramco has fallen victim to a data breach in which cybercriminals have stolen 1 TB of proprietary company data that they are now offering on the darknet, BleepingComputer reports.
Saudi Aramco, officially the Saudi Arabian Oil Company is a Saudi Arabian public petroleum and natural gas company based in Dhahran.
As of 2020, it is one of the largest companies in the world by income, bringing in almost $230 billion in annual revenue. Saudi Aramco has both the world’s second-largest proven crude oil reserves, at more than 270 billion barrels (43 billion cubic meters) and the largest daily oil production of all oil-producing companies.
The attackers are selling the entire data stolen from Saudi Aramco to individual buyers on an online hacking group starting at $5M but the price is negotiable.
The oil giant has told BleepingComputer that the cyberattack didn’t affect Aramco’s operations.
How Did the Saudi Aramco Data Breach Happen?
The cybercriminal gang known as ZeroX, which is offering 1 TB of data belonging to Saudi Aramco for sale, claims the data itself was stolen from the company sometime in 2020 though some of the files contained in the dump date all the way back to 1993.
When asked by BleepingComputer as to what technique was employed to obtain access to the systems, the threat actor did not explicitly spell out the flaw but instead called it “zero-day exploitation.”
In order to make prospective buyers purchase the data, a small sample collection of Aramco’s blueprints and proprietary papers with redacted Personally Identifiable Information (PII) was initially published on a data breach marketplace forum in June 2021.
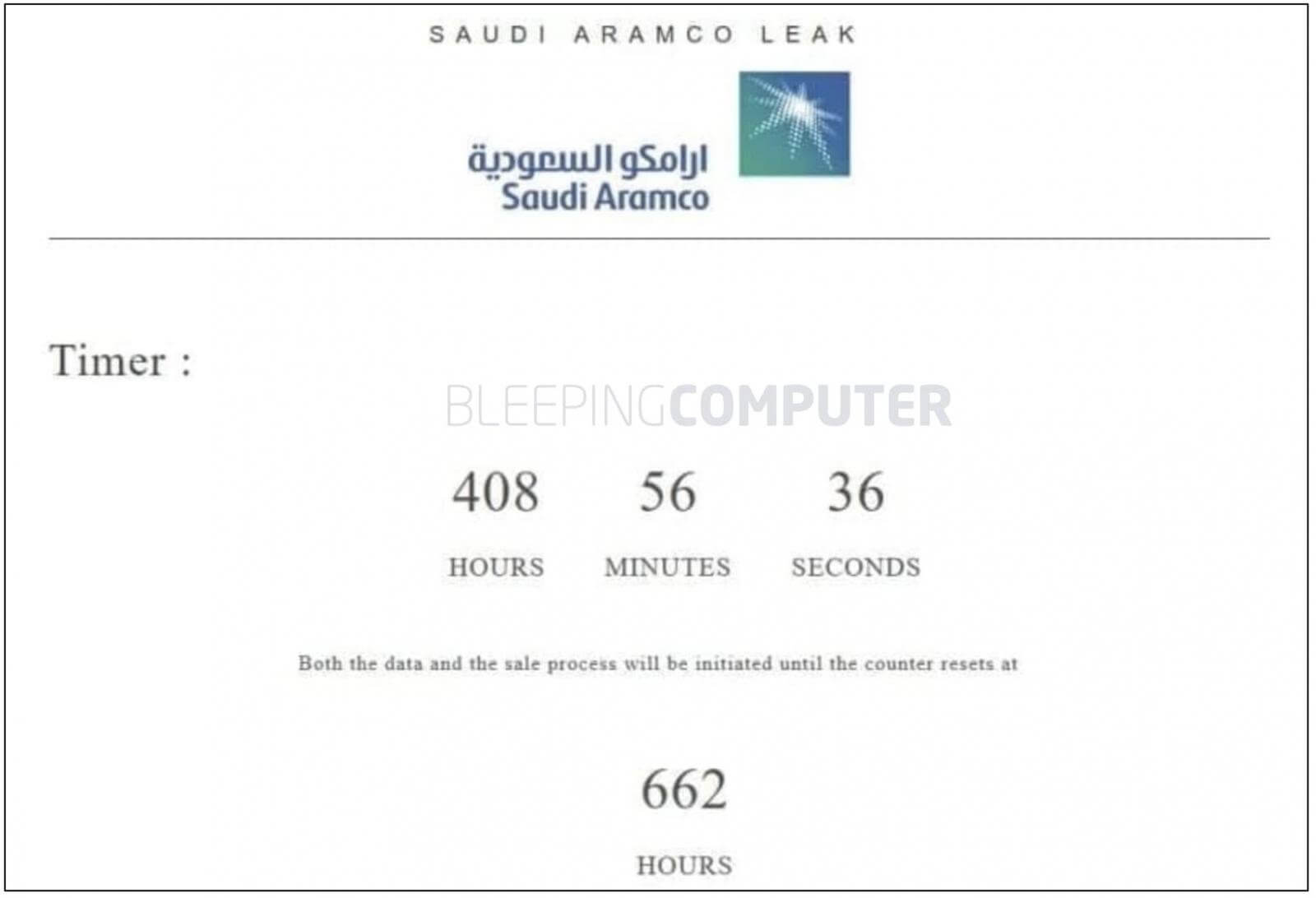
However, when ZeroX made its initial post, the .onion leak site used showed a countdown timer that was set to 662 hours. Once this 28-day long timer comes to an end, the sale and negotiations for the data will start.
The hacking group told BleepingComputer that the choice of “662 hours,” was deliberate and a “puzzle” for Saudi Aramco to solve, but the exact motive behind the choice continues to be unclear:
According to ZeroX, the 1 TB dump contains full information on 14,254 work staff including their names, photos passports, emails, phone numbers, residence permit (Iqama card) numbers, job title, ID numbers family information, and more.
However, it also contains project specifications, internal analysis reports, network layouts, location maps with precise coordinates, and a list of Aramco’s clients, along with invoices and contracts.
Here are some samples of stolen Saudi Aramco data and blueprints shared on the leak site:
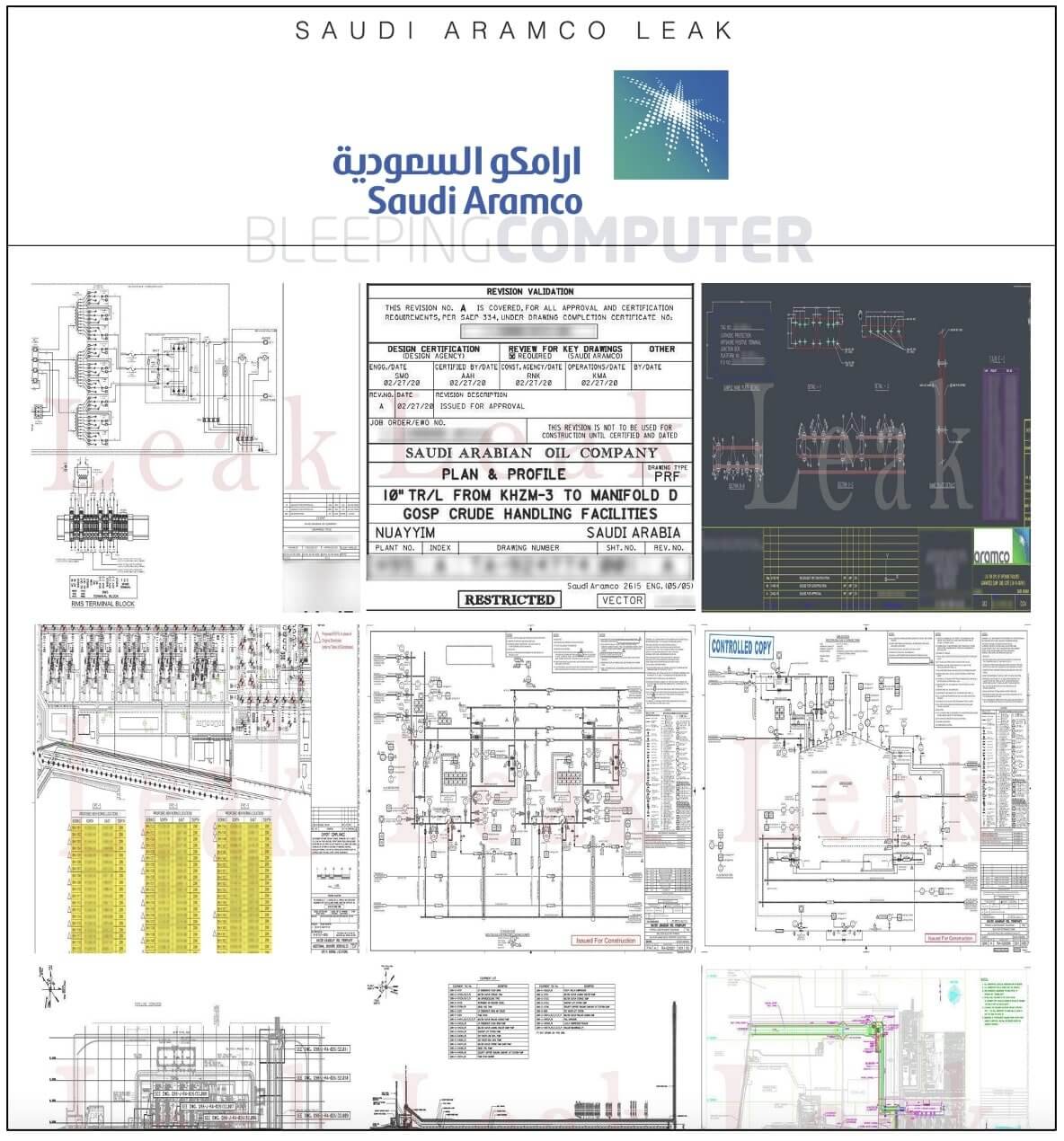
Samples published by the gang on the leak site have personally identifiable information (PII) redacted, and a 1 GB sample alone costs US$2,000, paid as Monero (XMR).
According to BleepingComputer, ZeroX cybercriminals have been negotiating the sale with five clients.
Was the Saudi Aramco Data Breach a Ransomware Attack?
Apparently not. Both the oil company and the ZeroX hackers have confirmed to BleepingComputer that this is not a ransomware incident.
The hackers did try to contact Saudi Aramco to notify them of the data breach but did not attempt extortion nor demanded ransom.
Saudi Aramco claims that the data was stolen from third parties, rather than direct exploitation of Aramco’s systems.
Aramco recently became aware of the indirect release of a limited amount of company data which was held by third-party contractors.
The energy organization confirmed that the release of information didn’t affect their operations, and the company continues to maintain a strong cybersecurity posture.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










