Contents:
Google researchers have recently revealed a new Rowhammer technique that expands threat actors’ reach on a target machine as DRAM chips become smaller.
Dubbed Half-Double, this technique capitalizes on the worsening physics of some of the newer DRAM chips to alter the contents of memory.
Rowhammer, which was first discovered back in 2014, is a vulnerability through which repeated access to one address can allow a threat actor to compromise data stored at other addresses.
According to Google’s Project Zero researchers, Rowhammer attackers work because DRAM cells are gradually becoming smaller and closer together. As DRAM manufacturing scales down chip features to smaller physical dimensions, to fit more memory capacity onto a chip, it has become harder to prevent DRAM cells from interacting electrically with each other.
As a result, accessing one location in memory can disturb neighbouring locations, causing charge to leak into or out of neighbouring cells. With enough accesses, this can change a cell’s value from 1 to 0 or vice versa.
Recent research has revealed DDR3 and DDR4 kinds of memory are vulnerable to the attack. Security analysts have also concluded that these attacks can be done using JavaScript rather than complicated malware code. The attacks can help a threat actor escalate privileges, root a device, or cause denial-of-service attacks against security software tools.
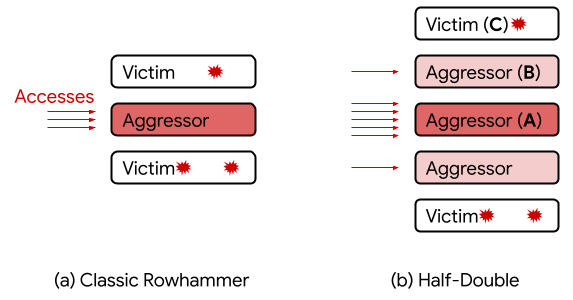
Image Source: Google Security Blog
As observed by researchers Salman Qazi, Yoongu Kim, Nicolas Boichat, Eric Shiu, and Mattias Nissler, Rowhammer used to operate at a one-row distance: when a DRAM row is repeatedly accessed (the “aggressor”), bit flips were found only in the two adjacent rows (the “victims”).
Nevertheless, with Half-Double, they have witnessed Rowhammer effects propagating to rows beyond adjacent neighbors, at reduced strength.
Given three consecutive rows A, B, and C, we were able to attack C by directing a very large number of accesses to A, along with just a handful (~dozens) to B. Based on our experiments, accesses to B have a non-linear gating effect, in which they appear to “transport” the Rowhammer effect of A onto C. Unlike TRRespass, which exploits the blind spots of manufacturer-dependent defenses, Half-Double is an intrinsic property of the underlying silicon substrate. This is likely an indication that the electrical coupling responsible for Rowhammer is a property of distance, effectively becoming stronger and longer-ranged as cell geometries shrink down. Distances greater than two are conceivable.
This discovery proves that as RAM chips have become smaller, the Rowhammer attack can be used to affect a wider number of cells.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










