Contents:
One of the more popular solutions used when deploying, scaling, and managing containerized apps in the Cloud, the Kubernetes containers are often threat actors’ targets.
This is the main reason that made the NSA and CISA publish a set of recommendations to help organizations strengthen their security.
The 52-page cybersecurity technical report released by the afore-mentioned security organizations came as a support and guidance effort considering the Kubernetes environment is a constant target for cyber attackers.
What Makes the Kubernetes Systems Easy Targets?
Hackers have multiple motivations for these attacks, ranging from data theft, cryptocurrency mining, and even denial-of-service (DoS) attacks.
According to the NSA, the principal causes for a compromised Kubernetes environment are supply-chain attacks, malicious actors, and insider threats.
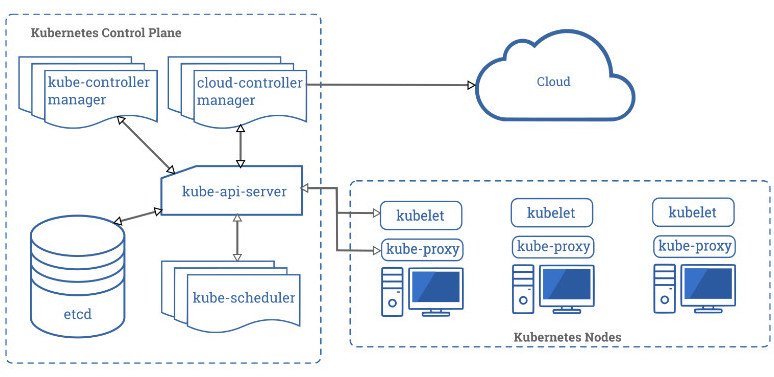
Kubernetes is an automation system that handles deployment, management, and scaling container-run apps most of the time. Kubernetes are organized in clusters and most commonly hosted in the cloud, the main purpose and advantage being that this provides a more flexible approach than traditional software platforms.
Targeted mainly for 3 reasons, Kubernetes systems are traditionally attacked for data or processing power theft. The other reason being DoS attacks, however, cyber actors will try, as mentioned above, to use Kubernetes to harness a network’s underlying infrastructure for computational power for purposes such as cryptocurrency mining.
The report details recommendations to harden Kubernetes systems. Primary actions include the scanning of containers and Pods for vulnerabilities or misconfigurations, running containers and Pods with the least privileges possible, and using network separation, firewalls, strong authentication, and log auditing.
It’s a known fact that administrators can’t prevent all three risks, but fortunately, they are able to strengthen the security of a Kubernetes cluster by avoiding common misconfigurations and apply mitigations to minimize security risks.
The NSA also notes that supply-chain attacks “are often challenging to mitigate,” as a malicious threat actor usually gets in by exploiting a vulnerability or leveraging any misconfigurations.
The NSA also clearly mentioned that one other significant source of threat is the one posed by insiders to the respective organizations. They can be anyone with the right set of skills and access to the network ranging from sysadmins, regular users with special privileges, or even cloud service providers.
Insiders with special access to an organization’s Kubernetes infrastructure may be able to abuse these privileges.
The defensive actions that can be taken against these threats are to scan containers and Pods for bugs and misconfigurations and review all Kubernetes settings regularly in order to make sure that the system is benefiting from the latest updates, patches, and available upgrades.
The “Kubernetes Hardening Guidance,” document explains the security recommendations and provides examples.

You can study the entire Kubernetes Hardening Guide document here.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










