Contents:
Atlassian has released a security advisory to address a critical Jira vulnerability in Jira Data Center and Jira Service Management Data Center products resulting in arbitrary code execution abilities.
Tracked as CVE-2020-36239, the vulnerability can cause critical remote code execution due to a missing authentication flaw in Jira’s implementation of Ehcache, an open-source component.
This advisory discloses a critical severity security vulnerability introduced in version 6.3.0 of Jira Data Center, Jira Core Data Center, Jira Software Data Center, and Jira Service Management Data Center (known as Jira Service Desk prior to 4.14). Affected versions of Jira Data Center and Jira Service Management Data Center can be found in the table above (see “Affected Versions”).
The bug comes nearly a month after precarious system features in the Atlassian project were revealed, allowing threat actors to easily access systems, obtain confidential information and steal users’ sessions.
In an email announcement seen by BleepingComputer, Atlassian asks its customers to update their instances as soon as possible as a means of correcting this error:
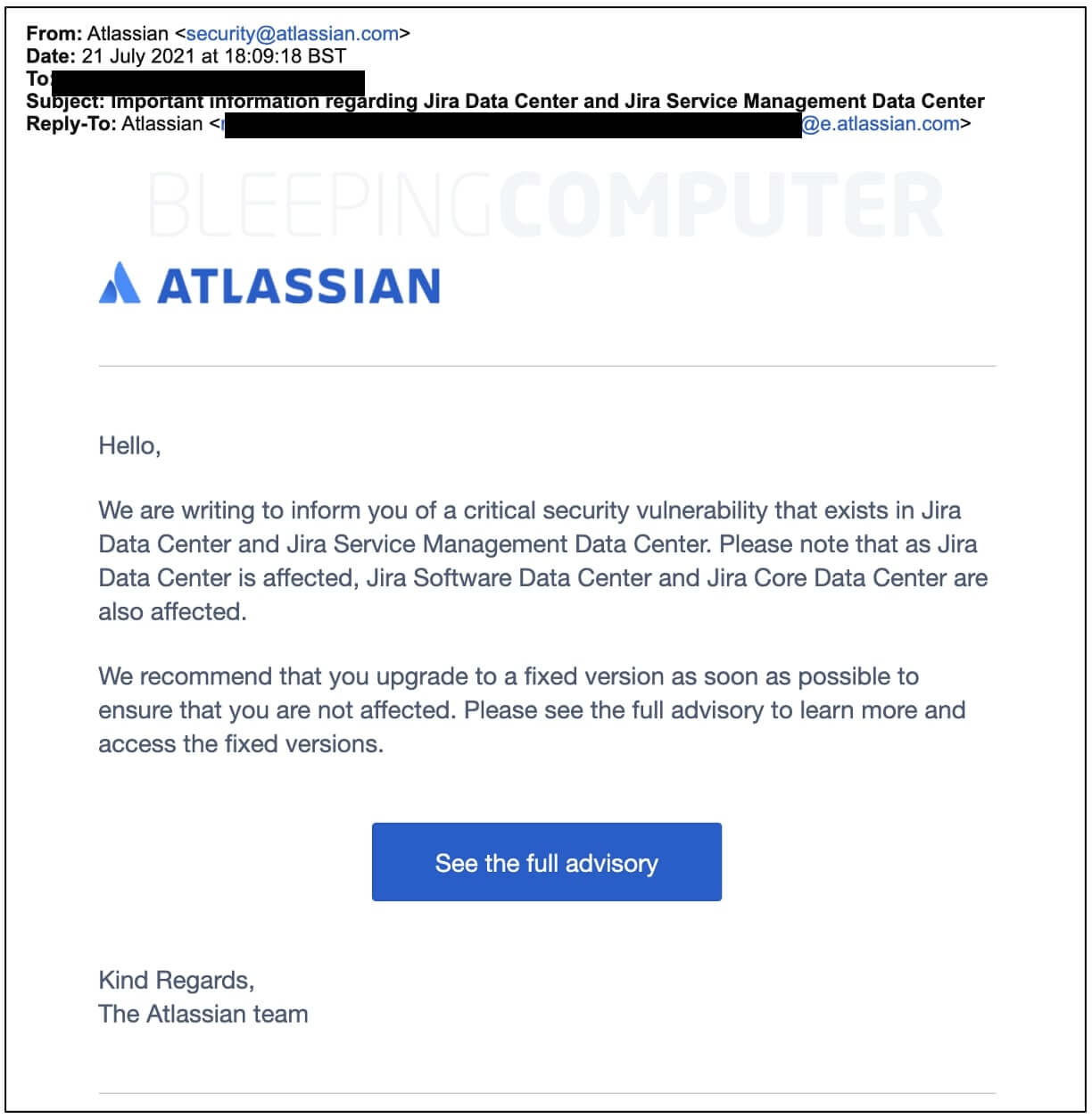
Image Source: BleepingComputer
As reported by Ax Sharma, the Jira vulnerability originates from unrestricted access to Ehcache RMI ports. Ehcache is an open-source, standards-based cache that boosts performance, offloads databases, and simplifies scalability. It’s the most widely-used Java-based cache because it’s robust, proven, full-featured, and integrates with other popular libraries and frameworks.
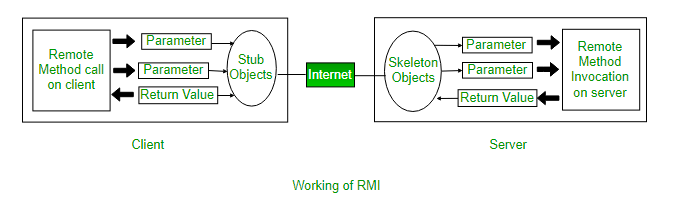
RMI (remote method invocation), is an API that provides a mechanism to create a distributed application in Java. RMI allows programmers to invoke methods present in remote objects—such as those present within an app running on a shared network, right from their application as they would run a local method or procedure. “All this is done without the programmer having to worry about implementing the underlying networking functionality, which is where RMI APIs come in handy”, Sharma writes.
Atlassian recommends customers who have downloaded and installed any of the following versions to upgrade their installations immediately to fix this new Jira vulnerability:
- Jira Data Center
- Jira Core Data Center
- Jira Software Data Center
- Jira Service Management Data Center
While Atlassian strongly suggests restricting access to the Ehcache ports to only Data Center instances, fixed versions of Jira will now require a shared secret in order to allow access to the Ehcache service.
Luckily, Non-Data Center instances of Jira Server (Core & Software), Jira Service Management, Jira Cloud, and Jira Service Management Cloud are not affected by the vulnerability.
Atlassian has also provided mitigations for customers unable to upgrade their instances.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security