Contents:
FFDroider, a recently discovered information stealer malware, steals credentials and cookies saved in web browsers in order to hijack targets’ Facebook, Instagram, and Twitter accounts.
Cybercriminals love social media accounts, particularly verified ones because they can use them for a variety of malicious purposes, such as cryptocurrency frauds and malware distribution. These verified accounts become even more appealing when they have access to the social media site’s advertising platforms, enabling hackers to use the stolen credentials to run malicious ads.
How Is FFDroider Spread?
As per a comprehensive technical analysis conducted by security researchers at cloud security company Zscaler, just like most malware, FFDroider info stealer is distributed through software cracks, free software, games, and other files got from torrent sites.
As explained by BleepingComputer, when these downloads are installed, FFDroider is also installed but is masquerading as the instant messaging application Telegram to avoid being detected.
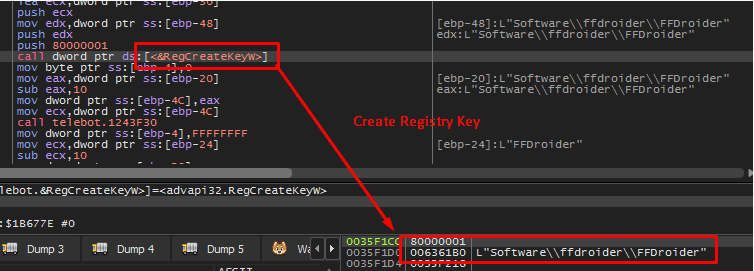
The malware will generate a Windows registry key called “FFDroider” once it is launched, which is how the info stealer got its name.
The attack cycle
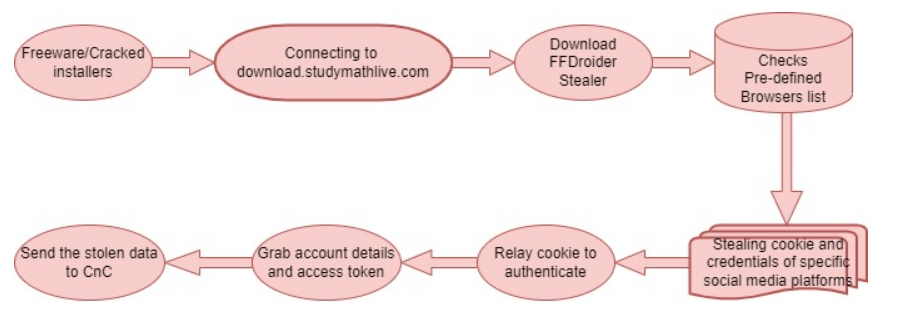
The new malware is focusing on cookies and account credentials saved in Google Chrome (and Chrome-based browsers), Mozilla Firefox, Internet Explorer, and Microsoft Edge.
Why Is It Targeting Social Media Accounts?
Unlike most password-stealing malware, the developers of FFDroid aren’t interested in all account credentials saved in web browsers. Instead, the malware operators are concentrating their efforts on stealing credentials for social media accounts and eCommerce websites such as Facebook, Instagram, Amazon, eBay, Etsy, Twitter, and the WAX Cloud wallet portal.
The objective is to collect legitimate cookies that can be used to authenticate on these platforms, which the info stealer malware tests on the fly during the procedure.
On Facebook
For instance, if the authentication succeeds on Facebook, FFDroider malware retrieves all Facebook pages and bookmarks, the number of the target’s friends, and their account billing and payment details from the Facebook Ads manager.
Malicious actors could use this information to run deceptive ad campaigns on social media platforms in order to spread their malware to a broader audience.
On Instagram
The stealer will open the account edit web page after successfully logging in to Instagram to scoop up the account’s email address, phone number, username, password, and other private information.
What’s interesting about the FFDroider malware is that it’s not just attempting to steal credentials; it’s also trying to log in to the platform and snatch additional data.
Following the data theft and transmission of everything to the C2 Command and Control server, FFDroid focuses on downloading more modules from its servers at predetermined intervals.
How to Stay Protected
In order to stay away from this type of malware, users are recommended to avoid illegal downloads and unreliable software sources.
As an extra safety measure, people can upload downloads to VirusTotal to verify if antivirus software recognizes them as malware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








