Contents:
Researchers recently discovered a new malware family named “Domino”, allegedly created by ITG14, also known as the FIN7 threat group. Reportedly, ex-Conti hackers have been using it since at least February 2023 to spread Project Nemesis info stealer or Cobalt Strike. Due to massive code overlap with the Lizar post-exploitation toolkit, researchers also attributed the new Domino malware to FIN7.
According to cybersecurity experts, hackers have been using the ”Dave Loader” malware loader for their attacks since the end of 2022.
Domino Malware Attacks Explained
The Domino malware family has two components, a backdoor and the loader that injects an info-stealing malware DLL into the memory of another process.
The loader is linked to ex-TrickBot and ex-Conti ransomware members and was seen deploying Cobalt Strike beacons that utilize a ‘206546002’ watermark. The same watermark was previously seen in the Royal and Play ransomware operations.
Previously, the Dave Loader also deployed Emotet, used in the Conti ransomware operation in June 2022, and by the BlackBasta and Quantum ransomware gangs.
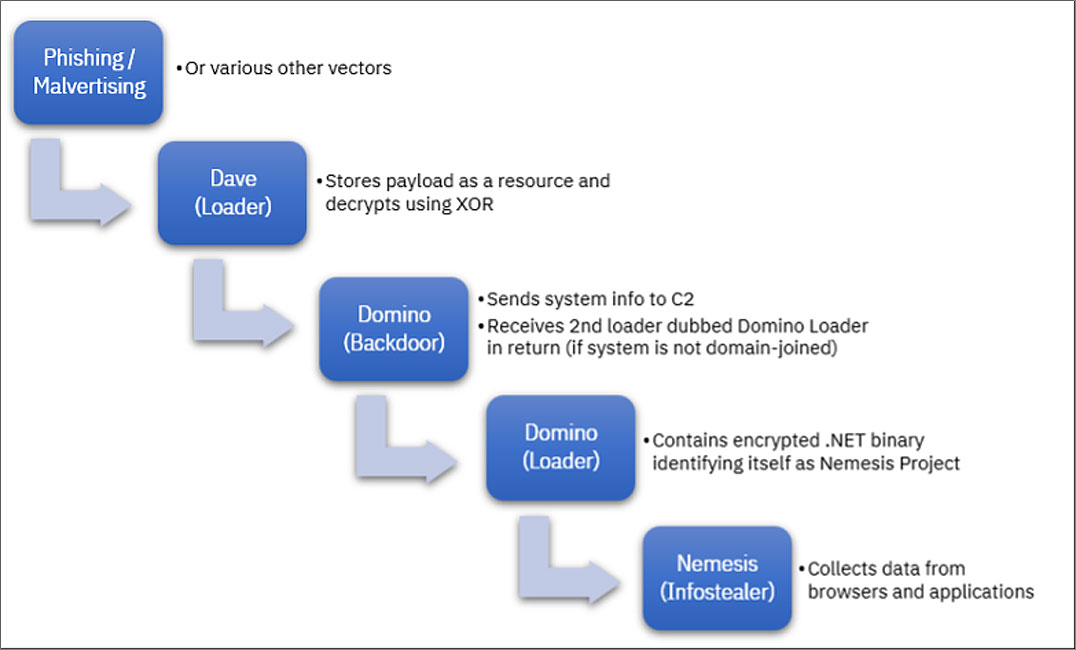
Here are the steps of action that follow accessing a malicious link – phishing, malvertising, etc.:
- Dave Loader drops Domino Backdoor, which is a 64-bit DLL that will enumerate system information. The data about running processes, usernames, and computer names is sent further to the attacker’s command-and-control server. Domino Backdoor also receives commands to execute or payloads to install.
- Domino Backdoor installs Domino Loader. Then the loader installs Nemesis Project, an embedded .NET info-stealer that can collect credentials stored in browsers and apps, cryptocurrency wallets, and browser history. To enhance persistence, Domino Loader can also plant a Cobalt Strike beacon.
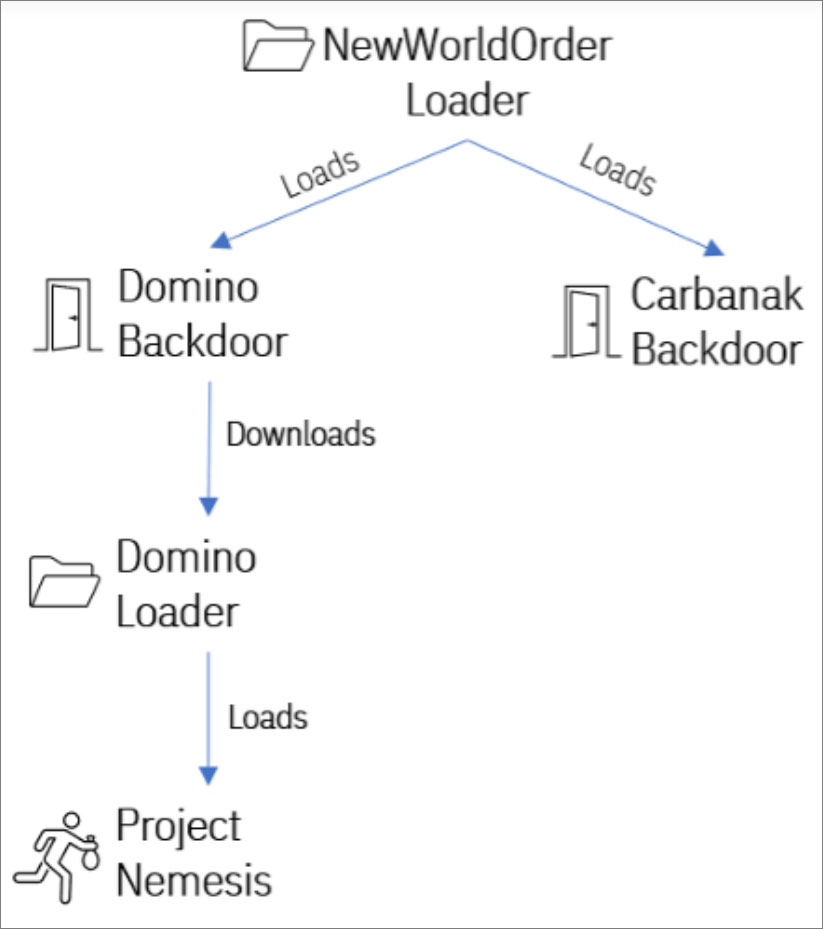
Researchers also found that another loader named ”NewWorldOrder” is used to deploy the Domino malware. The loader was frequently observed in FIN7’s Carbanak attacks.
How to Keep Safe from Domino Malware
Just like roughly 91% of online threats, Domino Malware also leverages DNS security gaps to breach corporate systems. The malware is reportedly deployed on previously compromised endpoints and uses DNS to send stolen data to its C&C server.
In this case, DNS filtering, which blocks any malicious domains spotted, can prevent threat actors from entering a system. If hackers use new domains, that are not known to be malicious yet, for their attack, predictive DNS technology is the only solution that can keep a company`s endpoints safe.
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security