Contents:
A new Python-based malware that targets online gambling companies in China was recently discovered by Trend Micro researchers Joseph C Chen, Kenney Lu, Jaromir Horejsi, and Gloria Chen.
Dubbed BIOPASS RAT, the malware targets its victims through a watering hole attack, tricking them into downloading a malware loader disguised as a legitimate installer for well-known apps such as Adobe Flash Player or Microsoft Silverlight.
According to the researchers,
BIOPASS RAT possesses basic features found in other malware, such as file system assessment, remote desktop access, file exfiltration, and shell command execution. It also has the ability to compromise the private information of its victims by stealing web browser and instant messaging client data.
Apart from these basic features, BIOPASS abuses popular live-streaming software, thus enabling watching the victim’s computer screen in real-time. What’s more, the malware can also steal private data from web browsers and instant messaging applications.
“We consider BIOPASS RAT as still being actively developed”
The threat actors behind BIOPASS seem to target online gambling websites visitors in China. The sites are injected with JavaScript code that serves the malware under the guise of installers for Adobe Flash Player or Microsoft Silverlight installers.
Adobe no longer supports Flash Player after December 31st, 2020, and blocked Flash content from running in Flash Player beginning January 12, 2021. The company strongly recommended all users immediately uninstall Flash Player to help protect their systems.

Image Source: Trend Micro
The same goes for Silverlight. Microsoft Silverlight reached the end of support on October 12th, 2021. Silverlight development framework is currently only supported on Internet Explorer 11.

Image Source: Trend Micro
The researchers found that the script retrieving BIOPASS checks if the visitor has been infected and it is typically injected into the target website’s online support chat page.
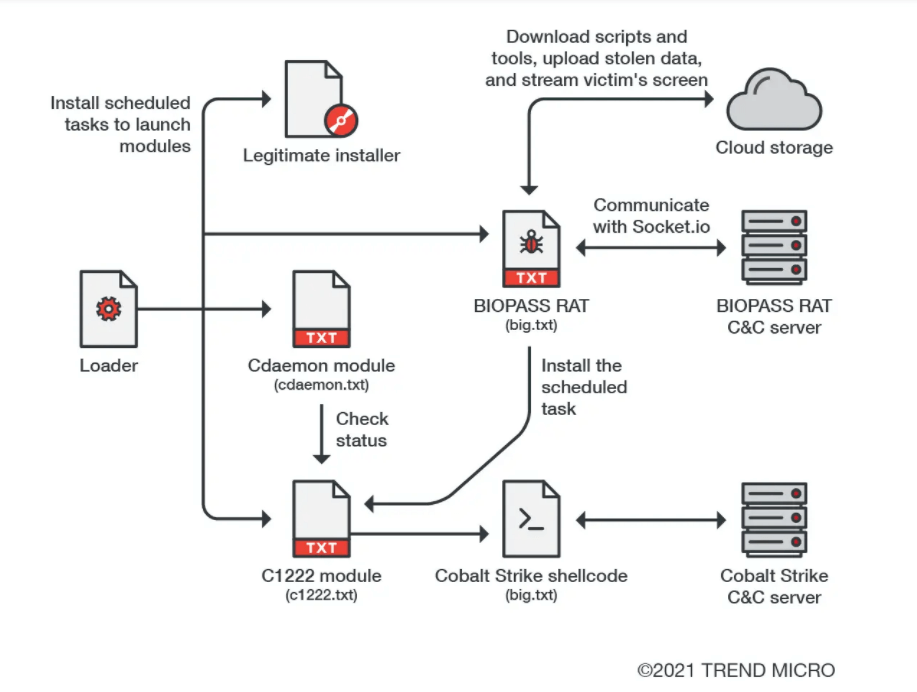
The initial delivery mechanism of BIOPASS RAT uses a watering hole, a compromised website in which the malicious actors inject their custom JavaScript code to deliver malware. In most of the cases that we observed, the attackers usually place their injection script in their target’s online support chat page.
Image Source: Trend Micro
The operator provides the legitimate installers for Flash Player and Silverlight, and the apps are being downloaded from the official websites or stored on the attacker’s Alibaba cloud storage.
The BIOPASS RAT is stored in the same place, along with the DLL and Python libraries necessary for running Python scripts on machines where Python is not installed.
Scheduled tasks that are activated on a new login are created. These tasks can run a BPS backdoor or a Cobalt Strike loader.
We also noticed the path string “ServiceHub”, which is a path to the extracted Python runtime. After the hex decoding of the arguments, we get a Python one-liner that downloads additional Python scripts from the cloud.
BIOPASS Abuses Popular Live-Streaming Software
According to the report, BIOPASS also downloads FFmpeg that monitors the victim’s desktop via RTMP live streaming to the cloud.
The Open Broadcaster Software, an open-source solution for video recording and live streaming, is downloaded as well, allowing the threat actor to connect to the relevant RTMP address to watch the streaming.
What’s more, the malware downloads the screenshot-cmd tool, which takes a screenshot of the victim’s screen with the tool and saves it as a PNG file with a random number as the file name. The malware uploads the screenshot files to cloud storage.
A command that enumerates installation folders for multiple messaging applications like WeChat, QQ, and Aliwangwang was also found.
BIOPASS is also responsible for extracting sensitive data like cookies and logins from several web browsers (Google Chrome, Microsoft Edge Beta, 360 Chrome, QQ Browser, 2345 Explorer, Sogou Explorer, and 360 Safe Browser).
Although the researchers weren’t able to identify the threat actor behind the BIOPASS RAT, they’ve found several clues that show how the malware might be connected with the Winnti Group, also known as APT41.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security