Contents:
Threat actors are becoming more and more cunning. A new Twitter post from Microsoft made public their process on tracking a new BazaCall Malware Campaign. Users receive e-mails that trick them into calling a pseudo-call center. They are asked to download a file that contains nothing more than infected software. The payload is this way initialized through a malignant macro.
What Is This BazaCall Malware Campaign About?
Behind this mischievous campaign stands a group of cybercriminals called BazaCall (or BazarCall). They use the BazarLoader malware and send phishing e-mails to users. These inform users that their trial subscription to some kind of service should be canceled or renewed. To do this, users need to call the phone number provided in the e-mail. From that point, the threat actors pose as call center agents and guide them to download the malware BazarLoader in order to modify the status of their subscription. If they do not call that fraudulent call center, the text in the e-mails says that users will be charged with a monthly fee so they have to act immediately.
How Do Hackers Act?
It was discovered that threat actors use the kit for penetration testing from Cobalt Strike and the Active Directory Data Base (AD). This way, credential information and identity of an organization are prone to theft, ZD Net reports.
Microsoft Lets Users See the Progress They Track
Microsoft is currently tracking this campaign as they announced on Twitter.
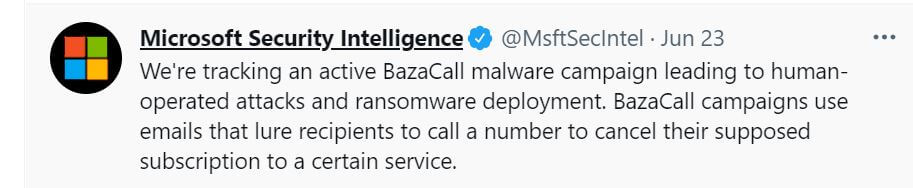
Moreover, to assist users, Microsoft is continuously publishing short updates on their Twitter account related to this topic and they even launched a GitHub page to keep people informed on the tracking. A GitHub platform is basically a Web-based graphical interface built mainly for programmers and developers to share teamwork in creating and updating codes. In other words, it is a hosting service that is a public home for code writing and updating. Microsoft uses these details to let the tracking process in plain sight of the users, pointing to the phishing e-mails, the queries they use and suggest to fight against the hacker’s methods, and how Cobalt Strike is managed to use compromised Excel macros and Windows NT Directory Services, or NTDS on the purpose to steal the AD files.
The Palo Alto Networks Intelligence Analyst, Brad Duncan, also said in a post that one of the cybercriminals’ tactics is to never use the same phone numbers or use two phone numbers per day in the targeted e-mails, according to DarkReading.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security