Contents:
Threat actors found a new attack vector spamming open-source ecosystem with packages that contain links to phishing campaigns.
144,294 phishing-related packages have been uploaded to open-source package repositories, like NPM, PyPi, and NuGet.
The Magnitude of this Phishing Campaign
Analysts at Checkmarx and Illustria say that all packages and associated user accounts were almost certainly produced using automation. This conclusion is due to the large scale of the attack, the similar project description, and the auto-generated names used by cybercriminals.
The attackers used a large number of packages with names related to hacking, cheats, and free resources to promote their phishing campaign. Some of the package names included “free-steam-codes-generator,” “yalla-ludo-diamond-hack,” “a3-still-alive-hack-diamonds”, and “project-makeover-hack-gems.” These names were designed to lure users into downloading the packages and clicking on the links to the phishing sites.
On NuGet were found the most malicious packages, no less than 136,258, PyPI had 7,894 phishing packages, and NPM only had 212.
The links to the phishing sites were implanted in the description of the packages to improve the search engine optimization (SEO) on the fake websites by connecting them to a legitimate site like NuGet.
The packages were uploaded in stashes for a couple of days, a frequent indicator of malevolent behavior.
Details About the Phishing Sites
The phishing links lead to the same 90 domains that host over 65.000 fake URLs.
“In some cases, the threat actors promote fake Steam gift card generators, Play Station Network e-gift card codes, Play Store credits, Instagram followers generators, YouTube subscribers generators, and more”, according to BleepingComputer.
Once on the sites, visitors were demanded to introduce their email, username, and account passwords. Although fake websites may mimic the promised free generator, they failed on delivering it, asking users for “human verification.”
After a series of redirections, the visitor arrived on a legitimate eCommerce website, like AliExpress, one of the largest internet shopping platforms in the world. Cybercriminals are using affiliate links to make money from the affiliate program on AliExpress.
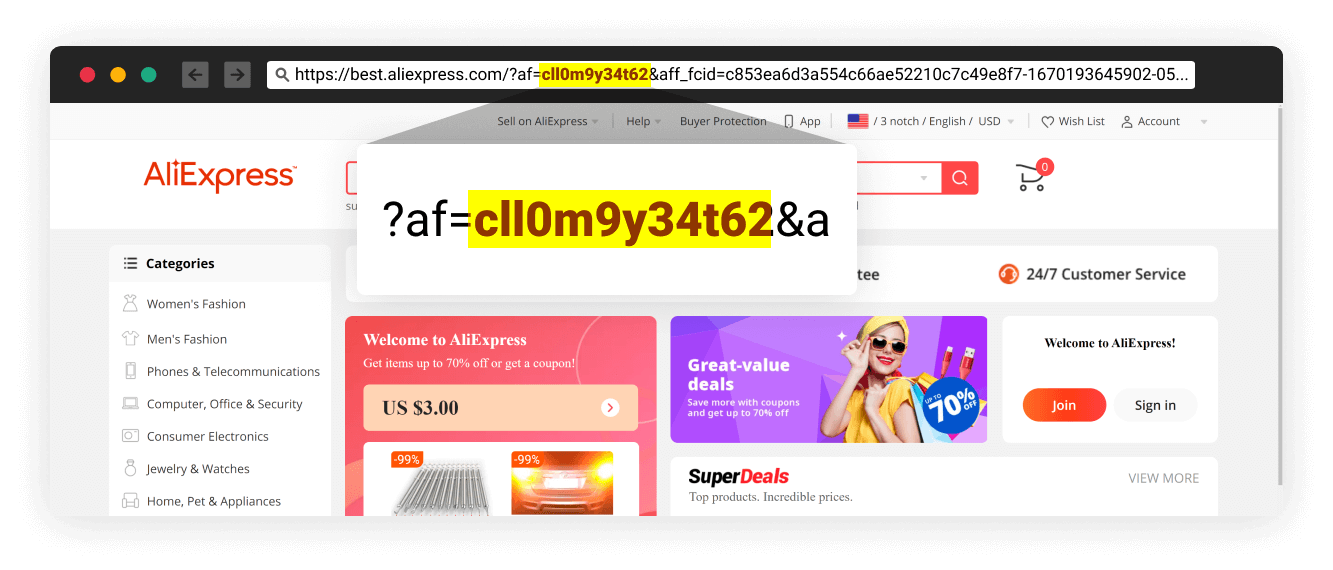
The stolen credentials can be another source of revenue if the hackers chose to sell them on the dark web.
Since this campaign was discovered all the phishing packages have been removed, but threat actors can use the same automated method to reintroduce packages with different names from new accounts.
Here is the complete list of URLs used in this campaign.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







