Contents:
A Netgear RCE was fixed by the computer networking enterprise, a high-severity bug located in their SOHO routers (Small Offices/Home Offices). More specifically, the vulnerability was discovered in the Circle parental control, the service that uses root permissions to run on the mentioned SOHO devices.
How the Netgear RCE Can Be Exploited
The vulnerability was dubbed CVE-2021-40847. In a usual case, if the service is stopped, the attack vector disappears. In this case, the issue lies in the fact that the Circle update daemon, the place where the bug was located, is enabled by default. Because of this, even if the service is turned off, the vulnerability is still an exploit means in the hands of hackers.
Adam Nichols, who is a security researcher at GRIMM, also explained in a report detailing this vulnerability that
The update process of the Circle Parental Control Service on various Netgear routers allows remote attackers with network access to gain RCE as root via a Man-in-the-Middle (MitM) attack.
You can also read more about Man-in-the-Middle attacks in my colleague Elena’s well-documented article.
It’s also worth mentioning that what is enabled by default are not the parental controls themselves, but the Circle update daemon which lets the vulnerability be exploited, as per the above-mentioned report.
To succeed in exploiting the bug, hackers should intercept traffic or change the network traffic. This allows them to achieve remote code execution root on the router they target. What happens after is that they get root access and the consequences are severe: cybercriminals have complete control over network traffic and this might lead to reading access to data that is encrypted, including data related to corporate network devices.
What Is Circle Netgear?
Netgear stands for a multinational computer networking enterprise with its headquarters in San Jose, California. Networking hardware production is what the company does.
Circle is basically a technology that allows parents to control children’s devices, devices connected to the home network. It can be bought separately or you can buy a Netgear router that comes with Circle functionality within.
An Attack Chain Described
If a cybercriminal compromises a router of an enterprise employee, for instance, he can use that access to breach the corporate network. In this sense, Adam Nichols related in the same report how such an attack might unfold:
First step
The hacker chooses a company. Then he makes some checks to establish what ISP (Internet service provider) the employees of that company use.
Second step
The cybercriminal might use phishing or exploits or any other means to compromise the ISP.
Third step
If the ISP is successfully compromised this leads to the compromising of routers that are vulnerable to the bug in the discussion found in the Circle Parental Control Service.
Fourth step
The compromised routers will allow communication with corporate computers connected to those infected routers. This way, hackers can go further and compromise the identified enterprise computers.
Fifth Step
The infection spreads from corporate computers to the corporate network and leads to data leakage.
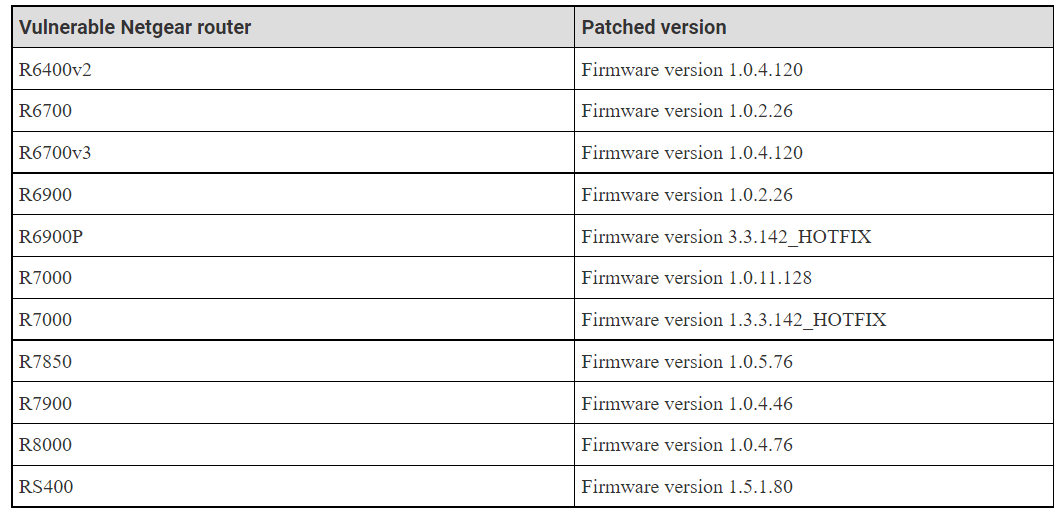
What Are the Vulnerable Routers?
Here are the routers vulnerable to this Netgear RCE bug:
What to Do Against Netgear RCE
According to BleepingComputer, Netgear released a security advisory last week and advised customers to download as soon as possible the latest firmware in order to mitigate the threat of this vulnerability.
To do these, here are some steps to be followed:
- First, you should go to NETGEAR Support.
- Then you should identify on the website your device searching by model number.
- Then click on download once you found it.
- You will see Current Versions and you should just pick the first ones named Firmware Version.
- You should click on Release Notes.
- Those Release Notes include instructions on how to install the firmware.
Another good threat mitigation measure would be the use of VPN clients when connecting to corporate environments.
Last, but not least, it’s interesting that this Netgear RCE fix comes after Netgear enterprise fixed the Demon’s Cries, Draconian Fear, and Seventh Inferno vulnerabilities that targeted smart switches, a topic that we also wrote about in previous posts.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








