In the next few years, a growing number of organizations across Europe will face investigations for non-compliance with the NIS2 Directive.
If they are found to have poor cybersecurity practices, they may well be forced to pay multi-million Euro fines and other penalties.
The best way to manage the risk of NIS2 penalties is, of course, to comply by following cybersecurity best practices.
But things aren’t always so straightforward, and many organizations may face scrutiny, audits, and investigations for potential infractions – even if they do have good security in place.
In this article, you’ll learn about how to manage this risk:
- Overview of NIS2 fines and penalties
- How to avoid NIS2 fines in the first place
- How to negotiate a NIS2 fine and reduce the severity of penalties if you do get breached
Learn more on how Heimdal helps comply with
EU'S NIS2 Directive
Do I need to be NIS2 compliant?
Being a large or medium organization offering services like healthcare, public administration, transportation, energy, water or other utilities, finance, waste management, etc. means you must be NIS2 compliant.
NIS2 is designed to improve cybersecurity among organizations operating in the European Union that are important to the bloc’s economy and stability.
The Directive has a two-tier approach and varying sizes of fines, depending on how critical the organization is deemed to be:
- ‘Essential’ entities: Maximum fines of €10,000,000 or 2% of the total worldwide annual turnover, whichever is higher. Essential entities include large companies providing critical services such as energy, water or finance.
- ‘Important’ entities: Maximum fines of €7,000,000 or at least 1.4% of total worldwide annual turnover, whichever is higher. Important entities include medium-sized businesses offering critical services, as well as large companies in sectors like manufacturing, agriculture, or waste management.
Besides the NIS2 fines themselves, the authorities will also have powers to penalize individuals at businesses that are found to be non-compliant.
Senior executives will be made personally liable for poor cybersecurity practices. The aim here is to focus minds (the reality in many firms is that security is still seen as an ‘IT thing’, and not a concern for C-level staff).
In cases of major negligence, the authorities may actually prosecute individuals (with the potential of imprisonment in extreme scenarios).
In less serious cases, the named individual may be barred from carrying out managerial responsibilities.
How to avoid NIS2 fines
In a recent Heimdal webinar, we spoke with security and compliance expert Larisa Mihai.
Larisa has worked with multiple businesses to help them deal with compliance challenges in the EU.
We picked her brains about how firms can manage their NIS2 risk.
For Larisa, by far the most effective way of dealing with NIS2 is through what she calls “continuous compliance”. This is the idea that firms should be constantly monitoring themselves to see how compliant they are against regulations.
All too many firms bury their heads in the sand about regulations, simply hoping they’re compliant, but without really knowing.
Continuous compliance has two big benefits:
- Reduces non-compliance risk: By regularly monitoring your own compliance, you’ll quickly identify any gaps, close them down, and avoid the consequences.
- Collects evidence of compliance: Regularly monitoring your environment should give you a clear base of evidence that you follow the rules. If you ever get audited by the authorities, you can quickly show them that you’re following best practices.
How to comply with NIS2

Complying with NIS2 requires a combination of people, processes and technology.
If NIS2 applies to your organization, you will need to:
Conduct a cybersecurity risk assessment
Document the threats you face, conduct pen testing and identify any weaknesses (among other actions).
Assess how well you currently comply with NIS2
Get key stakeholders together in a room. There should be people from:
- IT
- Legal
- HR
- Senior executives
To build a true picture of your current compliance status.
Develop security policies
If necessary, create or update security policies. At a minimum, you need to:
- Use two-factor authentication
- Make employees update passwords regularly
- Decide how to manage employee devices and third-party apps
- Restrict access to sensitive data at a minimum
Deploy advanced cybersecurity technology
- Use multi-factor authentication
- Implement end-to-end encryption
- Prepare a secure backup
- Prepare an incident response plan
- Apply patches regularly
- Use AI- powered threat detection and other advanced security tools
Discover our
Top 5 NIS2 Compliance Software
Review your incident response procedures
NIS2 requires organizations to notify the competent authority in their country of suspected or confirmed breaches within 24 hours.
A more detailed update should follow after 72 hours. You’ll then need to provide a final report within a month.
Carry out a supply chain risk assessment
Under NIS2, organizations may also be held responsible if a data breach at one of their suppliers eventually affects them.
You will therefore need to conduct third and fourth party risk assessments to verify whether or not your suppliers are following good security practices.
Free template: Vendor risk assessment template
Review your company culture
If you have to undergo a NIS2 audit following a breach, the auditors may interview employees and senior executives to find out how aware they are of cybersecurity best practices.
You should check that employees do actually get security training during onboarding, plus regular refreshers.
To follow Larisa’s recommendation about “continuous compliance”, it’s really helpful to have one, named individual at the business whose job it is to monitor the above factors.
This person should:
- Conduct NIS2 supply chain checks each time you sign contracts with new vendors
- Make sure employees get security training
- Check if employees did update their passwords
- Find out if staff are following any unsafe practices
- Regularly connect with senior teams and technical staff about policies, security testing and ways to further improve your defenses
- Keep a record of all their actions
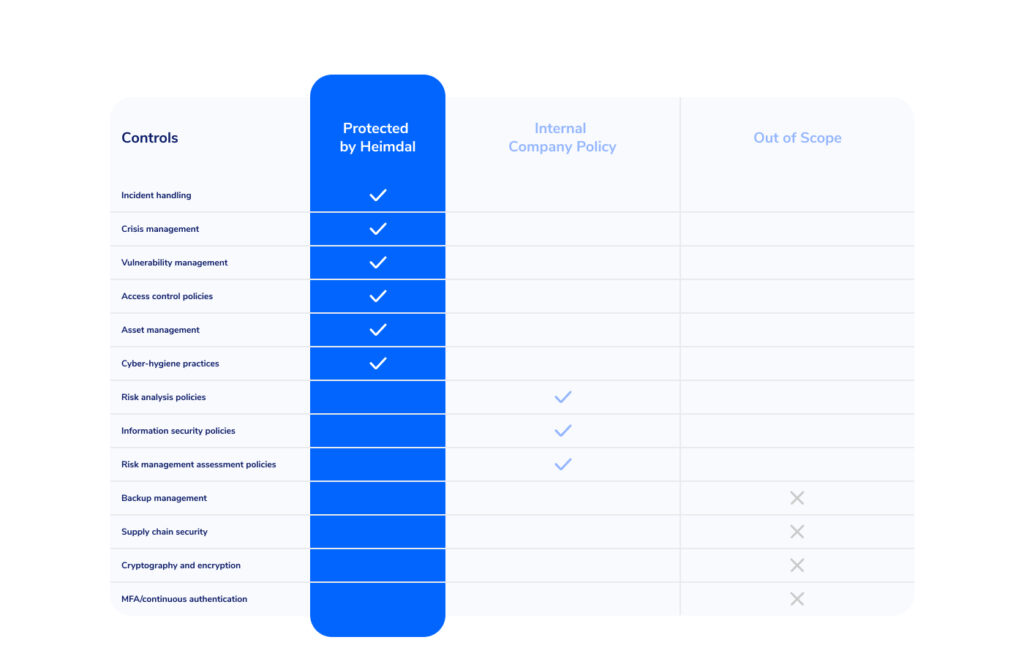
To make continuous compliance easier, use Heimdal’s NIS2 report.
The solution continuously monitors your IT environment for signals of NIS2 compliance, helps identify vulnerabilities, assets, or poor cyber hygiene (and more).
You can then respond to any issues and make the necessary changes.
Managing and negotiating NIS2 fines if you do get breached
Even with good security practices in place, there is always a risk that criminals will breach your defenses.
If this happens, organizations that come under NIS2 will face an audit from the authorities in their country.
As mentioned above, the most severe NIS2 fines could amount to €10,000,000 or more.
However, as Larisa pointed out, there will usually be room to negotiate the size of these penalties. Firms that can show they’ve made clear efforts to comply may well be able to reach a lower settlement with the authorities.
How can you do this? Once again, it’s all about continuous compliance.
Collect your evidence

- Larisa Mihai, Compliance Expert
If you have consistently collected data proving you have tried to comply, the authorities are likely to take this into account when deciding on the size of NIS2 fines.
Continuous compliance means you should have a large file of evidence showing that you’ve created policies, carried out tests and deployed security technology.
Nothing is guaranteed here. But with clear evidence of compliance efforts, the authorities are likely to be more lenient.
On the other hand, if you fail to collect evidence, it’s much harder to prove you’ve tried to comply – even if you genuinely did.
Larisa continues:

- Larisa Mihai, Compliance Expert
MSPs – be ready to defend against supply chain blame
Managed service providers who offer IT support to ‘essential’ or ‘important’ companies in the EU could also face legal action if their customers’ systems get breached.
If their customers get fined under NIS2, they may decide to sue any MSPs who supply them. If they can claim you failed to provide adequate security, there is a real risk they could take you to court – and win.
To avoid this risk, Larisa recommends that:

- ,
In practice, this is about clearly explaining to customers that, should they fail to follow good security practices, any breaches will not be your responsibility.
Ideally, you should write this into a contract. But for more ad hoc issues, you should put any advice or recommendations you give in writing.
Larisa adds:

- ,
The answer, she says, is email.
Not only should you email any advice or recommendations, Larisa also suggests that you: “push for them to send me something back in reply [to your advice], such as ‘I acknowledge the information’, or ‘I understand the risk’”. This way, you should be protected from any attempts to blame your business.
Manage your risk of NIS2 fines and penalties
At the time of writing (early 2025) no NIS2 fines have so far been imposed.
Nevertheless, it’s really only a matter of time before an ‘essential’ or ‘important’ organization gets breached – and we will soon see how national authorities decide to use their new powers.
To manage this risk, all EU businesses that come under NIS2 will really benefit from taking a “continuous compliance” approach.
Ready to get started? Use our NIS2 compliance solution to assess how you’re performing and track your progress.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








