Contents:
MITRE Corporation announced that state-backed hackers used Ivanti zero-day vulnerabilities to breach their system.
The attack happened in January 2024 and impacted MITRE’s Networked Experimentation, Research, and Virtualization Environment (NERVE). NERVE is an unclassified collaborative network that researchers use.
The two Ivanti vulnerabilities were:
- authentication bypass CVE-2023-46805
- command injection CVE-2024-21887
None of them had an available patch when the attack happened.
How did hackers breach MITRE?
At the core of the attack were two Ivanti zero-days and the fact that MITRE did not detect in time a lateral movement activity.
MITRE followed best practices, vendor instructions, and the government’s advice to upgrade, replace, and harden our Ivanti system, but we did not detect the lateral movement into our VMware infrastructure. At the time we believed we took all the necessary actions to mitigate the vulnerability, but these actions were clearly insufficient.
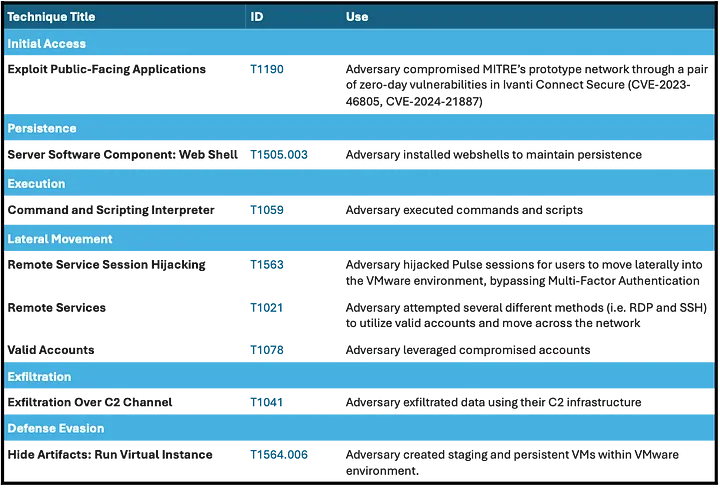
Source – MITRE Engenuity
Researchers at MITRE say the attack started in January 2024. After reconnaissance:
- Hackers used two Ivanti zero-days to breach MITRE`s Virtual Private Networks (VPNs)
- They used session hijacking to work around multi-factor authentication
- Used a compromised admin account to move laterally
- The attackers harvested credentials and maintained persistence through backdoors and webshells
How to mitigate a zero-day attack’s impact
The MITRE breach is a reminder that even those who abide cybersecurity standards can be victims of cyberattacks. In case of hackers exploiting a zero-day, the difference is in how much they can advance into the network. Or in how the attack impacts data integrity.
Robertino Matausch, Cybersecurity Expert @Heimdal says there is no such thing as 100% security.
The MITRE breach is a wake-up call. Falling victim to a cyberattack is not a question of if, but when! For now, I don`t see what MITRE could have done to avoid it. The question is was Ivanti providing the patches fast enough? If not – Ivanti’s fault, if yes Mitre was not fast enough patching.
Robertino Matausch, Cybersecurity Expert @Heimdal
This doesn’t mean you should resign to the thought that a system breach can happen no matter how thoroughly you try to avoid it.
To mitigate the impact of a zero-day attack you should:
- Use network segmentation to prevent the attack from spreading
- Enforce a Zero-trust policy and the principle of least privilege (PoLP)
- Use a DNS filtering tool to detect and block inbound and outbound malicious communication
- Strengthen passwords
- Use a NextGen AV
- Use End-to-end encryption
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

- End-to-end consolidated cybersecurity;
- Complete visibility across your entire IT infrastructure;
- Faster and more accurate threat detection and response;
- Efficient one-click automated and assisted actioning


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










