Contents:
On the 20th of April, Heimdal®’s SOC team has discovered that an unknown APT has been launching smishing attacks against Nordea Bank customers. The data analyzed so far suggests that the threat actor takes advantage of the MitID authentication mechanism in order to redirect the customer to a fake webpage for various malicious actions on target. So far, no victims have been reported.
The Details in the Case of the Nordea Bank Smishing Campaign
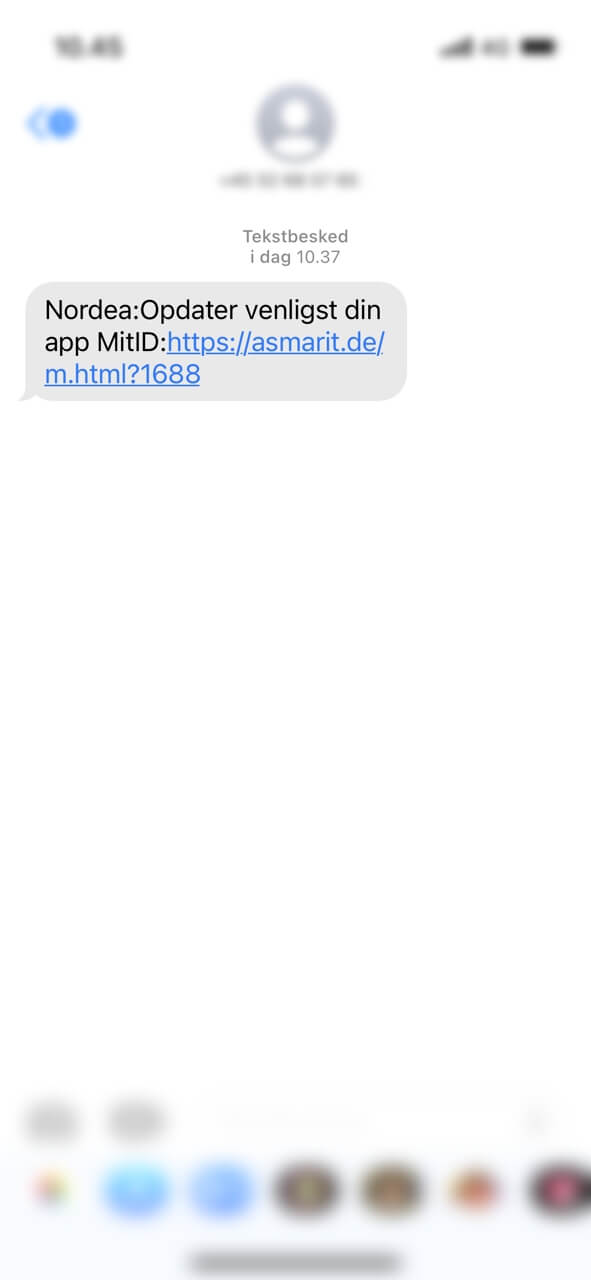
Acting on a tip received from an anonymous source, Heimdal® has uncovered that several devices using Nordea’s online banking application have been bombarded with cryptic messages, allegedly sent by the institution in question. The SMS instructs the client to update MitID application hosted on the device. However, instead of the expected app store redirect, the URL enclosed in the SMS points the user to an external, APT-curated resource. In all cases, the malicious SMS presents the following text.
Translated from Danish to English, the message reads:
Nordea: Please update your MitID app: [malicious link redacted].
Technical Analysis
Our subsequent digital forensics analysis has revealed the following information.
WHOIS query indicates that the URL enclosed in the SMS points to the asmarit.de domain, registered under https://www.rhein-it.de/, a hosting and domain management service based in Germany. However, this aspect neither relates to the threat actor itself nor to the victim(s), since the last modification has been committed back in 2017.
A closer analysis of the URL itself reveals a covert redirect to the 35-175-177-12.cprapid.com domain, more specifically to the cPanel-generated https://35-175-177-12.cprapid.com/nord/, allegedly associated with Nordea Bank. Furthermore, a subsequent IP lookup has concluded that the attacker used an EC2 AWS machine (probably hosted on the eastern side of Northern America) in order to stage the attack.
Taking all the available data into account, we have managed to formulate the methodology employed by the threat actor to enact this phishing attempt. The hacker sought a cheap hosting service and a free generated domain to serve as the phishing website.
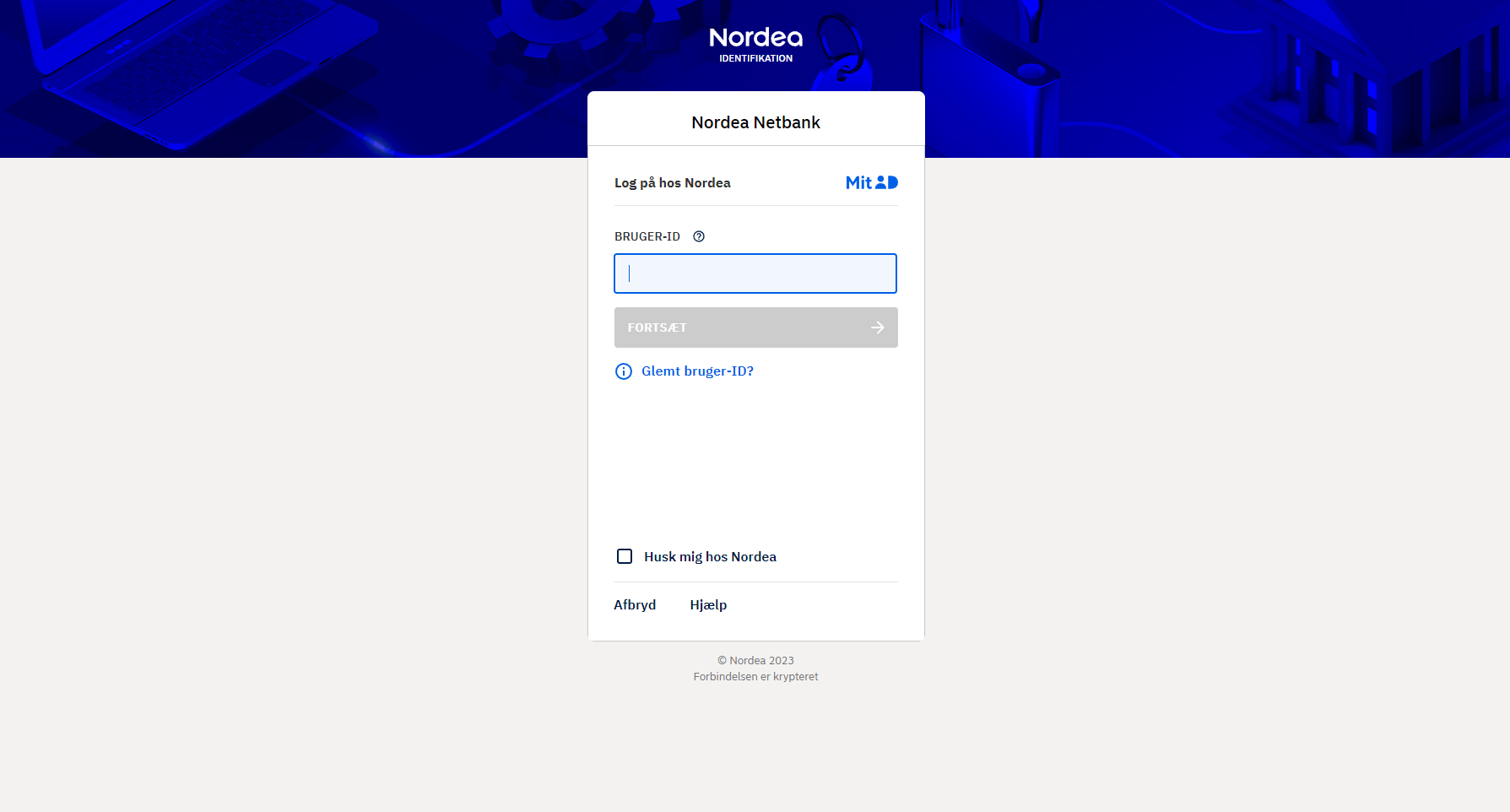
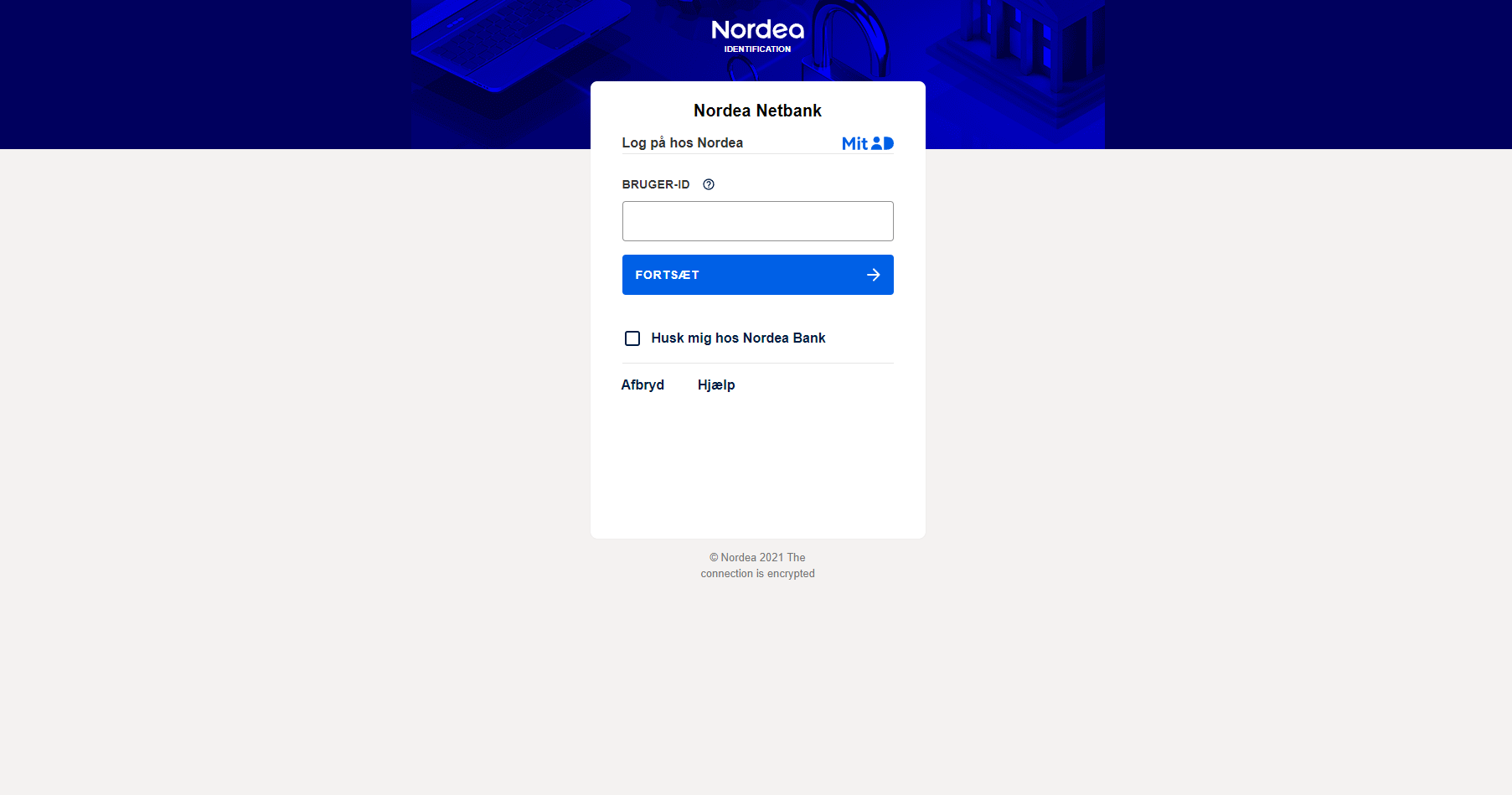
Since the autogenerated domain would not inspire confidence and, implicitly, won’t lure the user into interacting with it, they most likely compromised the asmarit.de website. Afterward, they placed a redirect URL webpage on the compromised resource and used it as a front for the actual phishing website. Finally, the attacker cloned the Nordea authentication page via an unknown automatic tool. See the below pictures for reference.
Nordea Bank Legitimate MitID Authentication Page
Cloned Nordea Bank MitID Authentication Page
Anti-phishing Cybersecurity Tips
Below, you will find a short, but comprehensive list of tips on how to guard yourself against phishing and smishing attempts.
Avoid opening suspicious-looking ads
Bear in mind that some Google ads you may come across are not malicious. However, this doesn’t mean that you should open everyone, just because the item looks interesting or was on your Wishlist (those can be tracked across apps and platforms). If you do open a link via SMS, make sure it has the HTTPS certificate – check for the padlock icon next to the link.
Deploy and employ next-gen anti-phishing protection
Some phishing attempts, such as the one we’ve discussed, employ a sophisticated anti-detection mechanism, allowing them to get past your antivirus. To counter these threats, you use an anti-malware solution that looks beyond the ‘file’ and ‘code’ level.
Heimdal® Threat Prevention – Network, Heimdal®’s award-winning network-facing DNS-filtering solution, can prevent threats from reaching your machine by blocking traffic to and from any malicious C&C server.
Too good to be true!
It’s the golden rule of the Internet: if something looks too good to be true, then it’s, most likely a scam. So, if some website requests very personal info to take possession of some fabulous prize, then it’s a scam. Also, keep in mind that anniversary sweepstakes, such as the one mentioned in the fake ad, are usually announced on the company’s website.
Conclusion
The Nordea Bank Phishing campaign was conducted via a legitimate hosting and domain-generation service, that was used to host the necessary credential-stealing resources. Moreover, the threat actor managed to reinforce credibility by employing a legitimate website that redirected the user to the crafted webpage.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security