Contents:
A fresh variant of a phishing campaign has been recently detected. By its nickname MirrorBlast, its targets are finance enterprises. The attack methods it uses consist of malicious Excel documents that are almost untraceable.
MirrorBlast: How Does It Work?
The researchers who discovered this new phishing campaign were those from Morphisec Labs and according to their report, here is how MirrorBlast works:
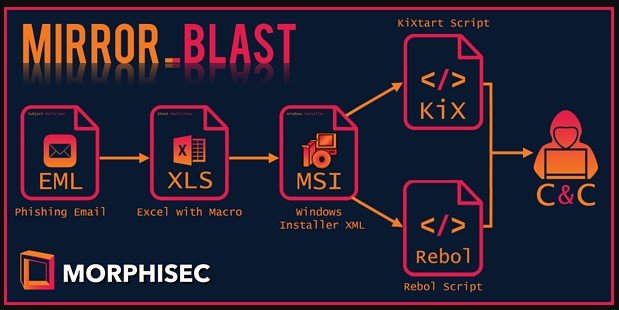
- It uses an obfuscated malicious code;
- Only a 32-bit Office version can be used to execute the macro code;
- After the target opens the compromised file and clicks on “enable content” a JScript script is executed by the macro;
- Then this triggers an MSI package downloading and installing;
- However, before this, an anti-sandboxing check is performed by the macro: this has the role to establish if computer name and user domain are the same things and if the user name is the same as “admin”;
- The MSI package will have two versions: one features the programming language REBOL, the other KiXtart.
- REBOL version: base64 encoded, it has the role of data exfiltration, for instance: OS version, user name, or architecture. The second stage where PowerShell is initiated through the C2 command follows.
- KiXtart version has also the role of data exfiltration, but now targeting a different type of info like domain, name of the computer, process list, and user name. Besides, it is also encrypted.
What’s interesting to mention is the way the malicious Excel file has been developed to bypass normal security software, as the researchers under discussion registered low detection rates.
New Phishing Campaign MirrorBlast: Who Is Behind?
According to the same experts who made the discovery, it seems that behind the new phishing campaign dubbed MirrorBlast is the TA505, a Russian threat group known for their particular methods of dropping Excel documents.
The attack chain of the infection bears a similarity to the tactics, techniques, and procedures commonly used by the allegedly Russia-based threat group TA505. The similarities extend to the attack chain, the GetandGo functionality, the final payload, and similarities in the domain name pattern. TA505 has been active since at least 2014 and, as far as analysts can ascertain, has a financial motivation for their actions. As a group, TA505 is most known for frequently changing the malware they use as well as driving global trends in malware distribution.
Besides, as per another report attributed to NCCgroup, TA505 exploits zero-day vulnerabilities in their cyberattacks: for instance, vulnerabilities exploitation with the goal of Clop ransomware deployment associated with attacks based on double extortion.
How to Stay Safe?
Phishing remains still a very well-known type of social engineering attack, as hackers regard human liability as a certain path to reach their goal. Most people will often not pay enough attention when clicking on a malicious document in a phishing e-mail.
To protect your business, you must ensure that you have the best security solutions to keep employees far from cyber threats. Heimdal™ has invested in the best email protection, having two excellent solutions: Email Fraud Prevention and Email Security. The first uses 125 analysis vectors combined with threat intelligence focusing on Business Email Compromise or CEO fraud, the latter keeps mail-delivered threats and supply chain attacks away. Curious? What are you waiting for? They are one click away!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










