Contents:
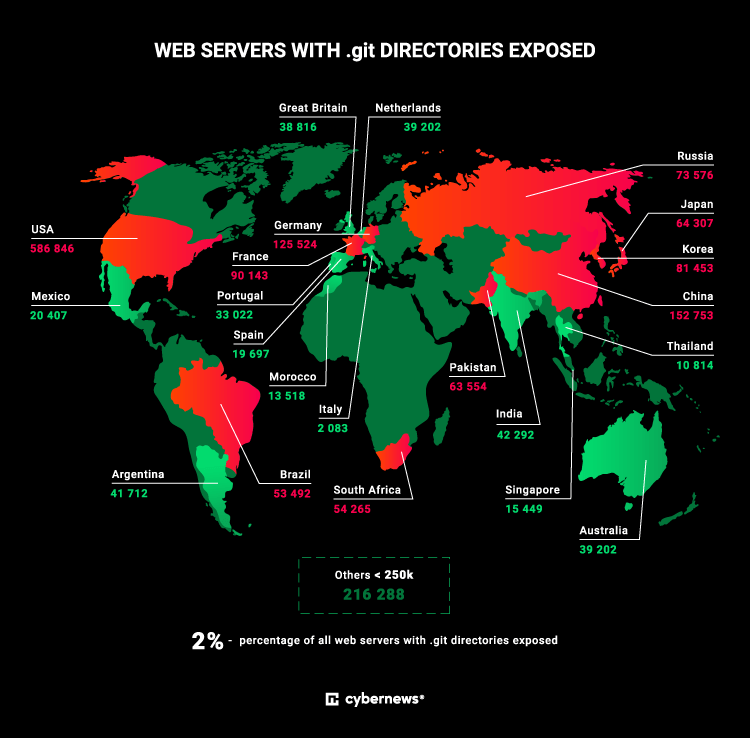
1.9 million .git folders containing critical project data are open to the public, discovered the Cybernews research team. The exposed folders are located mainly in the US (31%), followed by China (8%) and Germany (6.5%).
Git is a free and open-source distributed version control system (VCS) designed to coordinate work among programmers who create source code and allows them to track changes. A .git folder contains critical project information, such as remote repository addresses, commit history logs and other critical metadata. Leaving all this data open to the public poses a risk because it can result in breaches and system exposure.
According to another investigation by Cybernews, CarbonTV, a US-based streaming service, had left a server with its source code exposed, endangering both user security and the reputation of the company. Due to weak control of access to the .git folder, the source code was leaked.
1.9 Million IP Adresses With Public Access to .Git Folder Structure
Despite the risks, a more recent Cybernews investigation into IPv4 (Internet Protocol version 4) specifically, showed that the most widely used web service ports 80 and 444 are not always handled properly.
The research team discovered 1,931,148 IP addresses with live servers that had public access to the.git folder structure. 31% of the public .git folders are in the U.S, 8% in China and 6.5% in Germany.
And upon a closer look, the team found that the deployment credentials for 6.3% of the exposed .git configuration files were contained in the configuration file itself, as shown below.
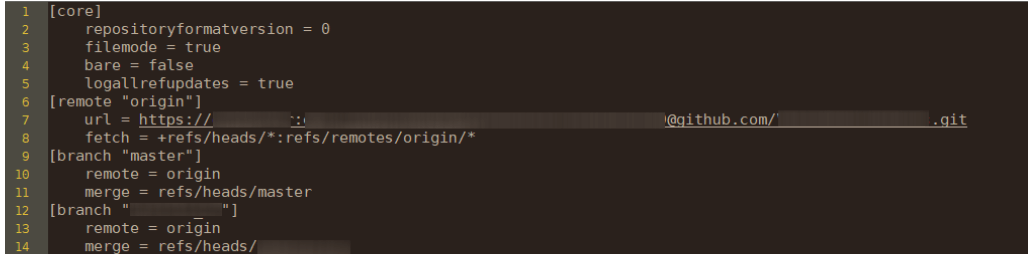
Having public access to the .git folder could lead to the exposure of the source code. Tools required to get parts or full source code from the .git folder are free and well-known, which could lead to many more internal leaks or easier access to the system for a malicious actor. Credential leaks are even worse. Threat actors could use them to view/access/pull/push all repositories, opening up even more opportunities for a malicious actor, such as planting malicious ads, changing content, and credit card skimming.
A statement from Martynas Vareikis, researcher at Cybernews
He also noted that developers should use the .gitignore file to tell Git which files to ignore when committing a project to the GitHub repository. And he added that, generally speaking, committing sensitive data, even to private repositories, is never a good idea.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








