Contents:
Security researchers have uncovered a new campaign aimed at multiple military contractors responsible for weapon manufacturing, including an F-35 Lightning II combat aircraft component supplier. The highly focused attacks start with an employee-specific phishing email, which triggers a multi-stage infection with several persistence and detection avoidance methods.
What makes this campaign outstanding is its use of PowerShell stager obfuscation and safe C2 architecture.
The Attack Explained
The attack was carried out starting late summer 2022 and targeted at least two high-profile military contractor companies.
According to BleepingComputer, the initial infection began with a phishing email sent to employees of the targeted companies. The email contained a malicious attachment, a ZIP file containing a shortcut file (“Company & Benefits.pdf.lnk”). Upon executing, the malware would connect to the C2 and launch a chain of PowerShell scripts that infected the system.
Accessing the file, disguised as a PDF, would trigger a seven-stage PowerShell execution chain characterized by heavy obfuscation that uses multiple techniques such as reordering/symbol obfuscation, IEX obfuscation, byte value obfuscation, raw compression, reordering, string replacement, and backtick obfuscation.
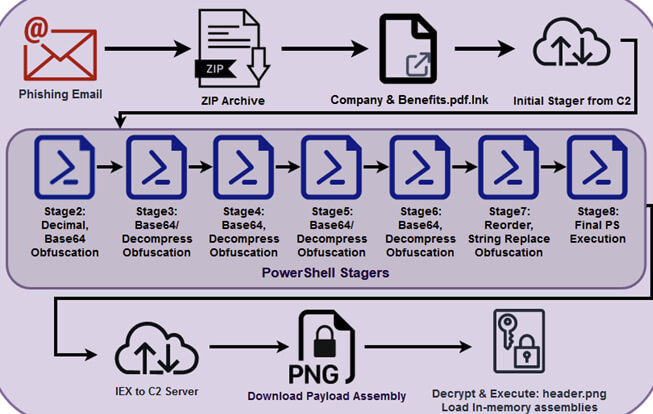
Infection Chain (Source)
The script also checks the screen height is over 777 pixels and the memory is above 4GB to avoid sandboxes, looks for a list of processes connected to debugging and monitoring tools, and confirms that the system was installed more than three days ago. If any of the checks fail, the script will disable the network adapters of the system, will configure the firewall to block all traffic, delete everything in the devices it detects, and then shut down the computer. However, if the language of the system is Russian or Chinese, the malware exists without causing any damage.
If all of the checks are successful, the script then inserts Windows Defender exclusions for “.lnk,” “.rar,” and “.exe” files as well as for directories necessary for the malware’s operation and disables the PowerShell Script Block Logging. A final payload (“header.png”) that has been AES-encrypted is downloaded from the C2 once the PowerShell stager has finished the procedure.
Attack Infrastructure
The domains used for the C2 infrastructure supporting the campaign were registered by the attackers in July 2022 and hosted on DigitalOcean. The domains were later moved to Cloudflare to benefit from its CDN and security services, including IP address masking, geoblocking, and HTTPS/TLS encryption.
Some C2 domains used by the attackers include “terma[.]wiki”, “terma[.]ink”, and “terma[.]dev”, “terma[.]app”
The campaign looks like the work of a sophisticated threat actor who knows how to hide its tracks from detection protocols. The attackers have not been yet found.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








