Contents:
The team discovered the flaws in NETGEAR DGN-2200v1 series routers while they were conducting an investigation on device fingerprinting. The researchers warned that exploitation of these vulnerabilities could result in identity theft and full system compromise.
Tracked as PSV-2020-0363, PSV-2020-0364, and PSV-2020-0365, they range in CVSS rating from high (7.4) to critical (9.4). Microsoft reported the discovery to NETGEAR, which has released a security advisory patching the flaws.
According to Microsoft’s Jonathan Bar Or, exploits for these firmware vulnerabilities can compromise a network’s security, making way for threat actors to roam free through an entire organization.
We noticed a very odd behavior: a device owned by a non-IT personnel was trying to access a NETGEAR DGN-2200v1 router’s management port. The communication was flagged as anomalous by machine learning models, but the communication itself was TLS-encrypted and private to protect customer privacy, so we decided to focus on the router and investigate whether it exhibited security weaknesses that can be exploited in a possible attack scenario.
As Security Week reported, the team managed to document side-channel attack scenarios and authentication bypass exploits that allowed the retrieval of secrets stored in the NETGEAR routers.
“Routers are integral to networking, so it is important to secure the programs supporting its functions”, Bar Or added.
The researchers performed a static analysis of the HTTPd binary and dynamic analysis. Eventually, they found some “pseudo-code” as the first-page handling code inside HTTPd, automatically approving certain pages such as “form.css“ or “func.js.”
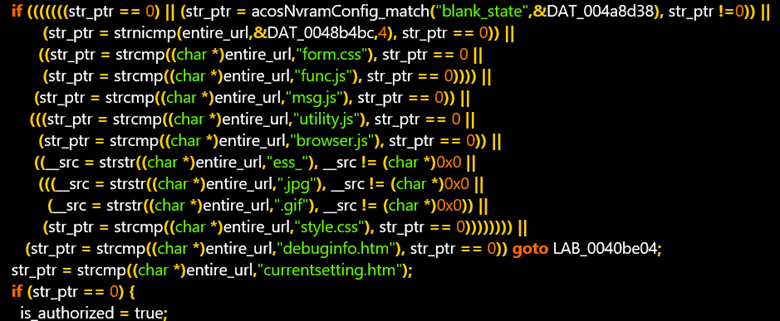
Image Source: Microsoft
Usually, this would not be a problem. However, “one thing that stood out was the fact that NETGEAR decided to use strstr to check if a page has “.jpg”, “.gif” or “ess_” substrings, trying to match the entire URL” Bar said. This meant that by appending a GET variable with the relevant substring (such as “?.gif”), the researchers could access any page on the device, including those requiring authentication.
The team decided to dig even deeper to see how the authentication was implemented. They found out that router credentials could also be gained using a side-channel attack.
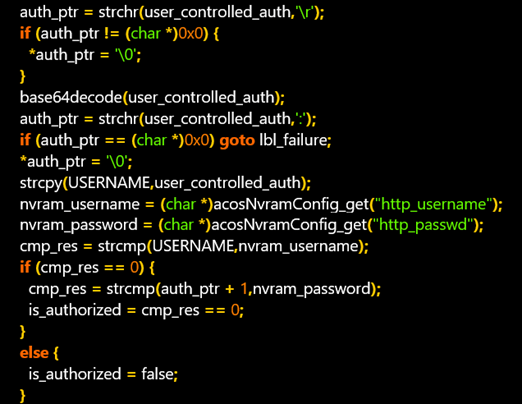
Image Source: Microsoft
Ultimately, the researchers wanted to see if they could recover the user name and password used by the router by another existing weakness. They focused on the device’s backup and restore feature, and by reverse-engineering the functionality, they found that it was possible.
After some preparatory steps, the contents are DES-encrypted with a constant key “NtgrBak”. This allows an attacker to get the plaintext password (which is stored in the encrypted NVRAM) remotely. The user name, which can very well be variations of ‘admin’, can be retrieved the same way.
The discovery of these security holes comes less than a week after Eclypsium, a U.S. company that addresses firmware security threats, revealed several high-severity firmware vulnerabilities that expose millions of Dell computers to stealthy attacks. The Dell SupportAssist vulnerabilities were allowing attackers to remotely execute code within the BIOS of impacted devices.
Recently, Microsoft has made firmware and IoT security a priority, with two strategic acquisitions – Refirm Labs and CyberX, both meant to support the tech giant’s ability to pinpoint and fix weak links at the firmware layer.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








