Contents:
Microsoft has patched a misconfiguration issue affecting the Azure Active Directory (AAD) identity and access management service that allowed unauthorized access to many “high-impact” applications.
The vulnerabilities were reported to Microsoft in January and February 2022, after which the company implemented fixes and gave Wiz a $40,000 bug bounty.
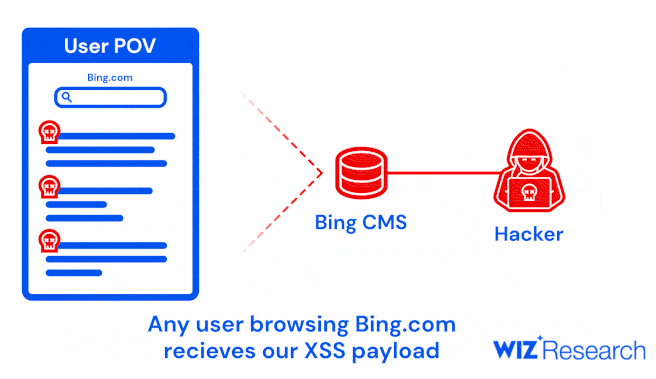
One of these apps is a content management system (CMS) that powers Bing.com and allowed us to not only modify search results, but also launch high-impact XSS attacks on Bing users. (…) Those attacks could compromise users’ personal data, including Outlook emails and SharePoint documents.
How Could this Vulnerability Lead to Unauthorized Access?
The core of the vulnerability derives from a phenomenon known as “Shared Responsibility confusion,” in which an Azure app might be incorrectly configured to enable users from any Microsoft tenant, leading to the possibility of unauthorized access.
Curiously, it was discovered that a number of Microsoft’s own internal programs exhibited the same behavior, allowing external parties to get read and write access to the affected applications.
This includes the Bing Trivia app, which the cybersecurity firm exploited to modify search results in Bing and even homepage content as part of the “BingBang” attack chain.
The flaw can be exploited to launch a cross-site scripting (XSS) attack on Bing.com and retrieve a victim’s Outlook emails, calendars, Teams communications, SharePoint documents, and OneDrive files.
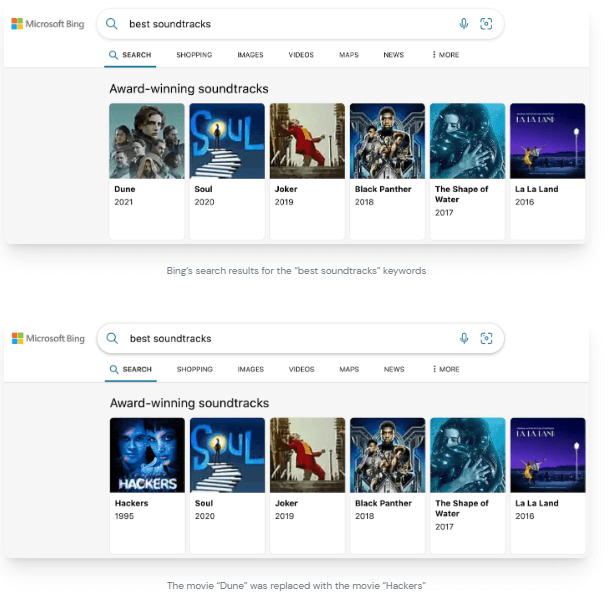
A malicious actor with the same access could’ve hijacked the most popular search results with the same payload and leak sensitive data from millions of users.
Mag News, Central Notification Service (CNS), Contact Center, PoliCheck, Power Automate Blog, and COSMOS were also discovered to be susceptible to the misconfiguration vulnerability.
The development follows the disclosure by enterprise penetration testing firm NetSPI of a cross-tenant vulnerability in Power Platform connectors that may be exploited to access sensitive data, explains The Hacker News. Microsoft fixed the deserialization issue in December 2022, following the publication of the problem in September 2022.
The research also coincides with the release of remedies to address Super FabriXss (CVE-2023-23383, CVSS score: 8.2), a reflected XSS vulnerability in Azure Service Fabric Explorer (SFX) that might result in unauthenticated remote code execution.
The complete analysis published by Wiz is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security