Contents:
Earlier this month, Iran’s transportation ministry confirmed a cyberattack against its computer systems, which has caused the portal page of the ministry and its affiliated pages to go offline.
Messages about train delays or cancellations were posted on display boards at stations across the country. What’s more, electronic tracking of trains across Iran failed.
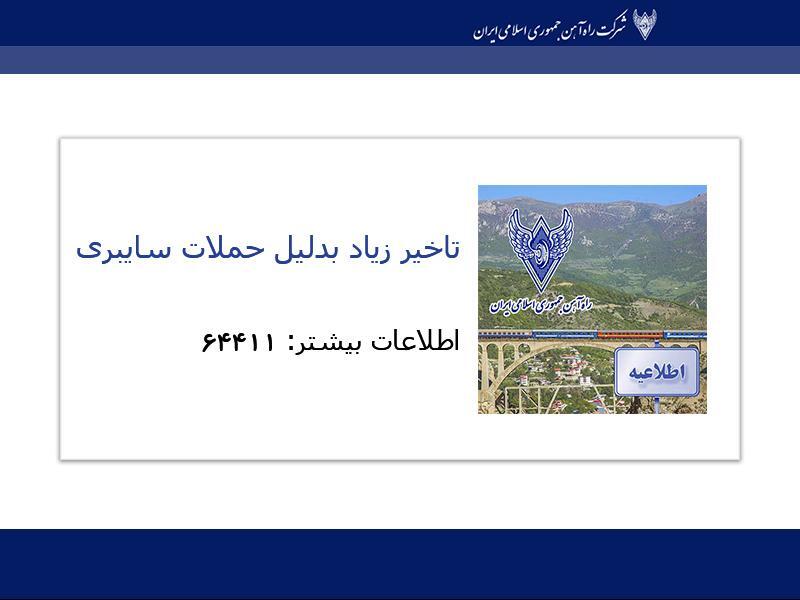
The attackers also urged passengers to call for information, listing the phone number of the office of the country’s supreme leader, Ayatollah Ali Khamenei.
A phone number–64411–was displayed on boards of train stations today in #Iran amid the reported cyberattack on the rail system. It directed commuters there to call for more information. It matched the number to #Iran‘s Supreme Leader’s Office that is displayed on his website. pic.twitter.com/IQQ85I6QhJ
— Iran International English (@IranIntl_En) July 9, 2021
Recently, SentinelOne researchers have published a new analysis revealing they have come across an unknown data-wiping malware, dubbed MeteorExpress, that was part of the disruptive cyberattack.
What Is A Wiper?
As Ryan Naraine explained in Security Week, wipers are considered the most destructive of all malware types, having been observed mostly in attacks in the Middle East, with the 2012 Shamoon attacks against Saudi Aramco as the most prominent example.
According to SentinelOne threat hunter Juan Andrés Guerrero-Saade, the researchers were not able to connect the wiper’s activity to a previously identified threat group nor to other attacks. Nevertheless, the artifacts suggest that this wiper was developed in the past three years and was designed for reuse.
MeteorExpress M.O.
The report reveals the threat actors abused Group Policy to distribute a cab file to conduct their attack.
The overall toolkit consists of a combination of batch files orchestrating different components dropped from RAR archives. The archives decompressed with an attacker supplied copy of Rar.exe coupled with the password ‘hackemall’. The wiper components are split by functionality: Meteor encrypts the filesystem based on an encrypted configuration, nti.exe corrupts the MBR, and mssetup.exe locks the system.
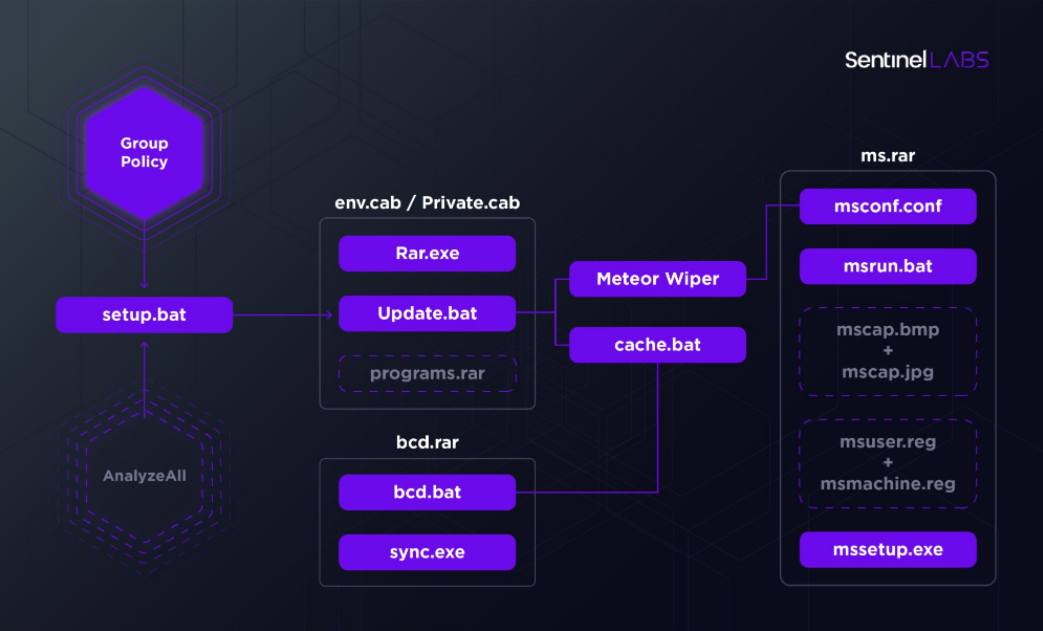
MeteorExpress Attack Chain
As opposed to ransomware attacks, wipers are not used to generate revenue for the malicious operators. Their aim is to cause chaos for an organization or to distract IT administrators while another attack is taking place.
While we were able to recover a surprising amount of files for a wiper attack, some have eluded us. The MBR corrupter, nti.exe, is most notable among those missing components (…).
Guerrero-Saade explained that the toolkit is a combination of batch files orchestrating different components dropped from RAR archives. He added that the wiper components are split by functionality: “MeteorExpress encrypts the filesystem based on an encrypted configuration, nti.exe corrupts the MBR, and mssetup.exe locks the system.”
MeteorExpress Screen Locker
He also noted that MeteorExpress takes a set of paths from the encrypted config and walks these paths, wiping files. What’s more, the wiper deletes shadow copies and removes the machine from the domain to avoid means of quick remediation.
Additional functionalities of MeteorExpress include:
- Changing passwords for all users
- Disabling screensavers
- Process termination based on a list of target processes
- Installing a screen locker
- Disabling recovery mode
- Changing boot policy error handling
- Creating scheduled tasks
- Logging off local sessions
- Changing lock screen images for different Windows versions (XP, 7, 10)
- Creating processes and executing commands
All in all, the threat hunters described the attacker as “an intermediate level player” with tooling that can sometimes seem amateurish.
However, it is notable that the operators behind MeteorExpress were familiar with the general setup of their target, features of the domain controller, and the victim’s choice of backup system (Veeam). In the researchers’ opinion, that implies a “reconnaissance phase that flew entirely under the radar and a wealth of espionage tooling” that they’re yet to uncover.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security