Contents:
Heimdal Security’s internal data has recently uncovered an increase in traffic to malicious websites. With the COVID-19 pandemic sweeping across the Continent, more and more companies have decided to fast-track the migration to remote work. During this transitionary period, employees, have had various issues accommodating with the new work- and lifestyle. One the consequences of this accelerated process is that the number of malicious attacks has increased accordingly. The role of this article is to highlight changes in users’ cybersecurity habits and to chart the phenomenon’s evolution. We shall also include Heimdal Security’s recommendations on how to counter this surge in ‘malicious traffic’.
Overview
The phenomenon has first been encountered in the second week of March, briefly after the World Health Organization recommended remote work if and when possible. Migration to remote work has been described as a ‘painstaking experiment’, with most enterprises and SMBs lacking the proper means to deploy and maintain a remote infrastructure of this magnitude.
Per this article’s introduction, one of the ramifications of this accelerated process is that the users fail to observe strict cybersecurity protocols when assigned to work from home compared to operating from a company-designated location. The data extracted from Heimdal Security’s database proves that there’s been a surge in malicious attack. Furthermore, per the same information, the number of file-based malware detected on end-point level is significantly higher after employees took up remote work compared to the beginning of 2020, when most were working from the office.
In-depth analysis
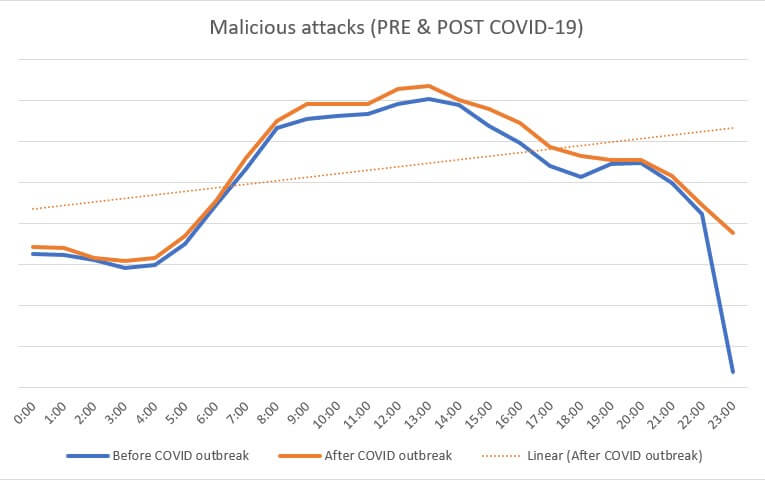
Our internal data reveals that between the 00:00 – 23:00 interval, approximately 1,000,000 malicious attacks (attempts to establish a connection between the endpoint and a Command & Control server) occurred. The reference timeframe is 27 February – 27 March.
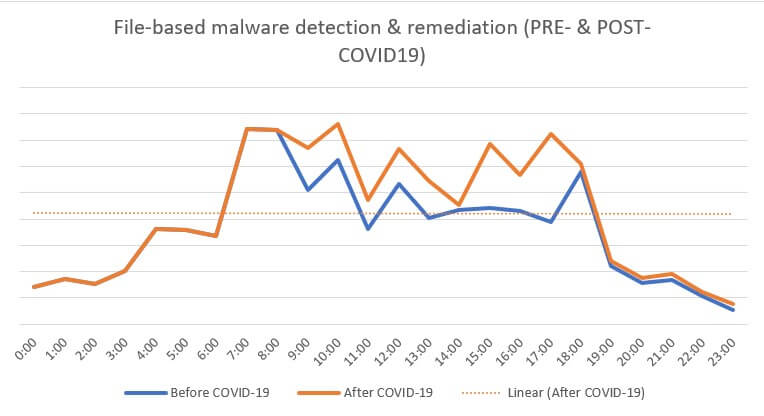
Concomitantly, throughout the aforementioned interval, approximately 10,000 file-based malware has been detected. Compared to the pre-COVID reference timeframe (December – January), there is a 20% increase in detection of file-based malware and an 8% increase in malicious attacks.
The dynamic analysis performed on the extracted data reveals that the number of malicious attacks has increased by 5% during official office hours (09:00 – 18:00). Subsequently, the number of infections detected per endpoint has seen a 30% increase during the post-COVID timeframe.
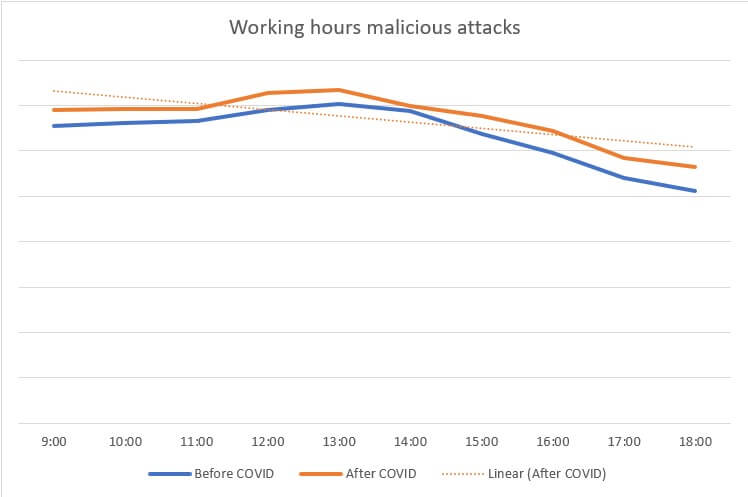
As far as the distribution is concerned, the highest number of attacks (approximately 6%) appears to have occurred in or around lunchtime (13:00). One plausible explanation would be that employees are more likely to access malicious content during the lunchbreak (i.e. attempting to stream a pirated movie from an unsecure website) then during the rest of the schedule, when they are considered to be under supervision.
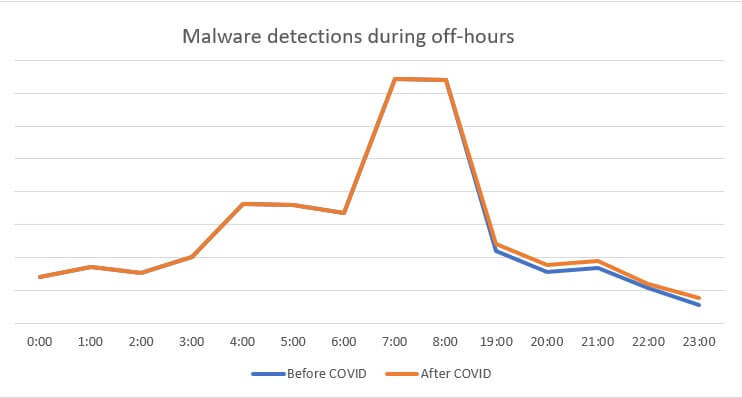
In terms of infection with or by file-based malware, the amplitude has been recorded at around 7:00 AM. The most plausible explanation in this case would be that some employees would get up early in order to perform various non-work-related tasks. This may take them to websites with potentially malicious content.
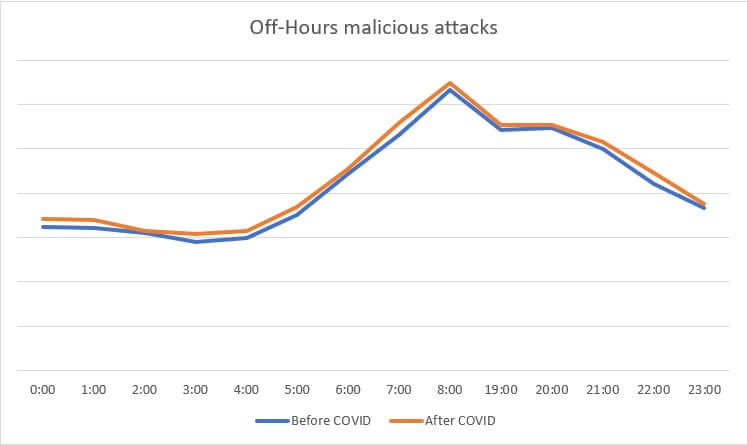
File-based malware detection activity during off hour (18:00 – 08:00) is marginal, before and after the COVID-19 outbreak. For reference, Heimdal Security’s internal data records a 2.37% increase in off-hour malware detection & remediation since the beginning of the Work from Home Exodus.
Comparative analysis
In highlighting the contrast between the two timeframes (pre- and post-COVID), in terms of malicious attacks and file-based malware detections at endpoint level, we have broken down the phenomenon into two subsets: occurrences (file-based malware detected at endpoint level vs. malicious attacks) during work hours (09:00 – 19:00) and off-hours (00:00 – 08:00/19:00 – 24:00).
Work hours – malware vs. malicious attacks
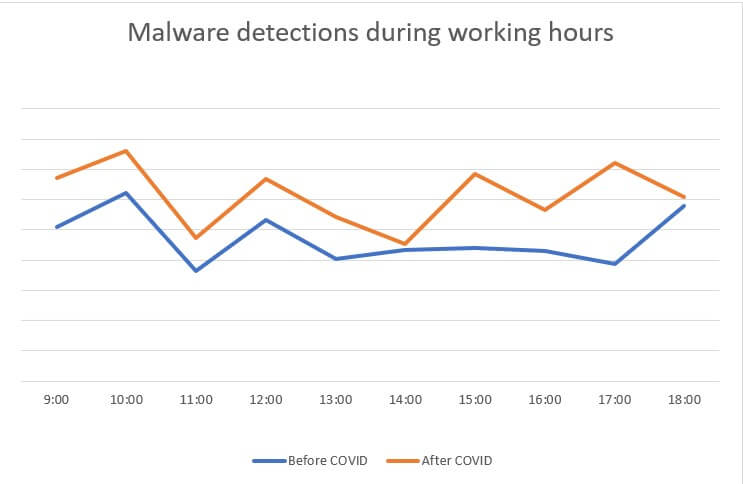
On average, there has been an 33% increase in file-based malware detection (post-COVID compared to pre-COVID timeframe). The most significant percentile increase (86% compared to pre-COVID timeframe) has been recorded around 17:00. At around that time, having completed the tasks for the day, most employee may begin reviewing non-work-related materials, thus increasing the risk of endpoint infection. This is how the file-based malware detection & mediation trend looks like.
Analyzing the data subset pertaining to malicious attacks detected during working hours, there has been 6%, on average, increase in malicious attacks (post-COVID compared to pre-COVID). Please see below graph for additional information.
Off-hours (non-work-related activities) – malware vs. malicious attacks
Taking a closer loom at the off-hour data subsets for both file-based malware detections and malicious attacks, we have discovered a 6% (avg) increase in the no. of malware infections and a 4% increase in malicious attacks. Compared to the working hours values (33% versus 6%), we find the non-working-hours increments as negligible. Please consult the graphs below for additional information.
Here’s how the malicious attacks graph looks like.
File-based malware detection graph can be consulted below.
No information is available on the typology of websites accessed by the employees during the reference timeframe. However, no attempts have been made to override company-enforced firewall rules in order to access these external resources.
In regards to the malware pathology, Heimdal™ Security’s internal data reveals that more than 80% of detected malware were trojans; adware, phishing, and rootkits account for the rest.
Since the beginning of the phenomenon, no data exfil attempts have been registered or any cues that would point to the existence of criminal infrastructure. Based on the available data, the forensic analysis concludes that the spike in malicious attacks and infections is due to the fact that most employees fail to observe strict cybersecurity protocols when working remotely.
Outlook
Based on the data analyzed so far, the forensic analysis concludes that the increase in traffic to malicious websites is not to be attributed to malicious actors attempting to exfil valuable information, but rather to pernicious and complaisant cybersecurity praxis on the end-user side. The actions required to curb the ascending trend in both malicious attacks and file-based malware detection is education. Please review the “Tips” section for more info on how to increase your company’s global cyber-resilience factor.
Work from home cybersecurity recommendations
The COVID-19 took the entire world by surprise, forcing companies to either suspend any activity or move everything online. Truth be told, the existing IT infrastructure, whether we choose to view it from a company or ISP standpoint, was simply not designed to handle such loads. You may have already noticed that OTA apps we took for granted (i.e. WhatsApp for business, Skype, Microsoft Teams) have reached the proverbial breaking point.
Still, we mustn’t lose track of the fact that cyber-criminals are always on the lookout for vulnerabilities and will act if given the opportunity. Working from home doesn’t mean you should forget about cybersecurity hygiene.
The case at hand proves that malicious actors are on the prowl, and we should take all the necessary precautions to ensure that we safeguard the company’s assets, as well as our personal data. Below, you will find a comprehensive list of security measures you should start using as soon as possible.
1. Use a work-dedicated machine
If you’ve been issued a machine by the company, then you should use it instead of your personal device. Work machines usually employ additional layers of security, which will help increase the cyber-resilience factor.
2. Deploy advanced anti-malware protection
Most companies would install VPN solutions on machines before allowing their employees to work from home. While VPN is a great anonymizer, it doesn’t protect your data in transit. The best way to ensure that the packages arrive safely at your destination would be to employ a solution that scrambles (and obfuscates) the data, while continuously scanning the traffic at multiple levels.
Heimdal™ Threat Prevention, Heimdal™ Security’s DNS filtering solution, can keep your endpoints safe by monitoring the traffic at DNS, HTTP, and HTTPS levels. If a malicious connection is detected, our anti-malware solution will block the communication to ensure that no malware reaches the machine.
3. Prevention is always the best defense
In the end, the best way to protect your endpoint is to exercise a modicum of caution. Some commonsensical advice: don’t click on malicious links, don’t transfer funds to the company’s partners before running it with your CEO, and don’t try to bypass the firewall to access forbidden websites.
Conclusion
Heimdal™ Security continues to monitor the phenomenon. No victims reported so far, but the status quo can change at any moment. From an ‘etiological’ standpoint, the campaign appears to target only remote workers. This is an ongoing article. We will update it when and if more info becomes available.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security