Contents:
Since at least December 2021, the NPM package manager has been the target of a pervasive software supply chain attack that used rogue modules to obtain information from forms that users filled out on websites that include them. Named IconBurst by security vendor ReversingLabs, the coordinated cyberattack involves no less than 24 NPM packages that contain obfuscated JavaScript and malicious code that is used to collect private information from forms embedded in other websites and mobile applications.
Karlo Zanki, a reverse engineer at ReversingLabs stated:
As with the recent (benign) dependency confusion attacks targeting German organizations, these clearly malicious attacks relied on typo-squatting, a technique in which attackers offer up packages via public repositories with names that are similar to — or common misspellings of — legitimate packages. Attackers impersonated high-traffic NPM modules like umbrellajs and packages published by ionic.io.
NPM Packages Still Available
The NPM modules the researchers discovered have been collectively downloaded more than 27,000 times. The attacks went undetected for months before the security company became aware of them because only a few development organizations are capable of finding malicious code within open source libraries and modules.
Although some of the named packages have been taken off of NPM, the majority are still available for download as of the time of this report.
Here is a list of the malicious NPM modules:
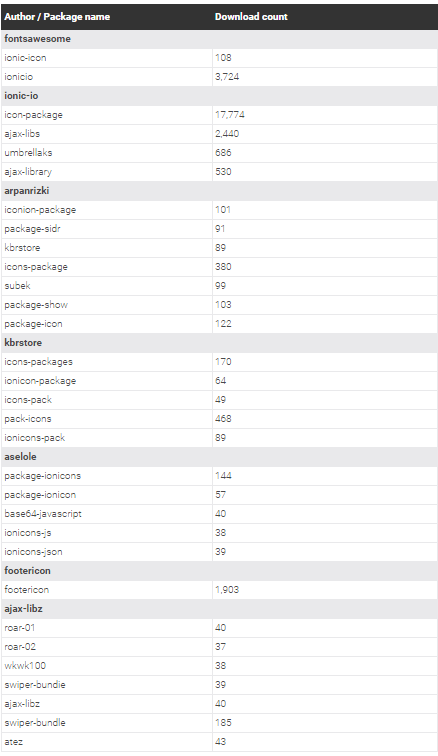
ReversingLabs once noticed that data stolen by icon-package was sent to a page with the fictitious domain name ionicio[.]com that was designed to look like the official ionic[.]io website.
In recent months, the malware developers were seen changing up their strategies to collect info from every form element on the web page, which is an indication that the operation is taking an aggressive approach to data harvesting.
Since it is impossible to estimate how much data was stolen from infected apps and websites, the complete extent of the cyberattack is still unknown. The malicious packages were allegedly used in hundreds of apps.
Looking beyond this specific incident, it is clear that software development organizations as well as their customers need new tools and processes for assessing supply chain risks like the ones posed by these malicious NPM packages.
The decentralized and modular nature of application development means that applications and services are only as strong as their least secure component. The success of this attack underscores the freewheeling nature of application development, and the low barriers to malicious or even vulnerable code entering sensitive applications and IT environments.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








