Contents:
The discovery was made by malware analysts from Doctor Web. The specialists uncovered 10 of these trojan apps, of which 9 were available on Google Play. These stealer trojans were spread as harmless software and were installed over 5,856,010 times.
The applications were fully functional, which was supposed to weaken the vigilance of potential victims. With that, to access all of the apps’ functions and, allegedly, to disable in-app ads, users were prompted to log into their Facebook accounts. The advertisements inside some of the apps were indeed present, and this maneuver was intended to further encourage Android device owners to perform the required actions.
Below you can find the list of malicious apps:
- PIP Photo (over 5,000,000 installs)
- Processing Photo (over 500,000 installs)
- Rubbish Cleaner (over 100,000 installs)
- Horoscope Daily (over 100,000 installs)
- Inwell Fitness (over 100,000 installs)
- App Lock Keep (50,000 installs)
- Lockit Master (5,000 installs)
- Horoscope Pi (over 1,000 installs)
- App Lock Manager (10 installs)
According to the analysts, the apps were fully functional, which was supposed to weaken the vigilance of potential victims.
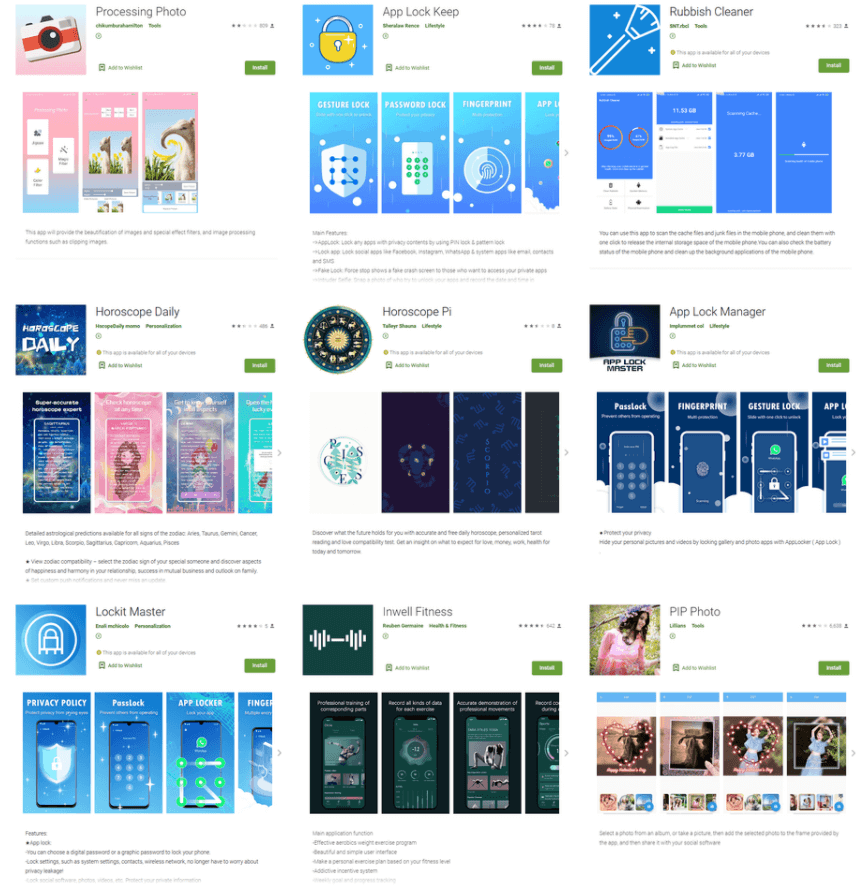
Image Source: Dr. Web
The malicious apps tricked users by hiding their malicious intent by disguising as photo-editing, optimizer, fitness, and astrology programs. After installation, they logged into their Facebook accounts and hijacked the entered credentials through a JavaScript code received from an adversary-controlled server. The trojans also stole cookies from the current authorization session which were sent to cybercriminals. The stolen data was exfiltrated to the server using the trojanized applications.
Although it seems that the campaign has set its sights on Facebook credentials, the researchers warned that this attack could be been easily expanded to any legitimate web platform.
Analysis of the malicious programs showed that they all received settings for stealing logins and passwords of Facebook accounts. However, the attackers could have easily changed the trojans’ settings and commanded them to load the web page of another legitimate service. They could have even used a completely fake login form located on a phishing site. Thus, the trojans could have been used to steal logins and passwords from any service.
The discovery comes just days after Google announced new measures for the Play Store, including 2-Step Verification (2SV) and additional identification requirements. According to the Google Play Trust and Safety team, these two requirements are a step towards strengthening account security and ensuring a safe and secure app marketplace.
Dr. Web researchers recommend users install applications only from known and trusted sources and pay attention to other reviews. Although these reviews cannot guarantee that the apps are harmless, they can still warn Android device owners about potential threats.
Additionally, users should also pay attention to when and which apps ask them to login into their account. They are advised not to proceed any further and uninstall the suspicious program if they’re not sure about the legitimacy of the app.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










