Contents:
A few months ago I was writing about my preference for using web applications due to the fact that they allow me to move between browsers tabs swiftly. Today we’ll come back to the browser security topic and we’ll find out what is a malicious Chrome extension and how it can affect the cybersecurity of your company.
Malicious Chrome Extension – Some Definitions
What is a web browser and how does it work?
A web browser is “a software application that retrieves and displays information from a server including web pages, text, images, videos, and other content.”
How does it work? SmartBear nicely describes the process:
The browser acts as a client to contact the web server and request information. When you search something on Google and click on a link or enter a URL in the address bar, the webserver locates and sends the information you just requested to the web browser. It does this by first performing a Domain Name System (DNS) look to find the correct IP address. This basically means that every URL has an equivalent set of numbers – the IP address – and the DNS translates it into language so we can type “Google.com” instead of “74.125.134.102”. After that, it sends a Hypertext Transfer Protocol (HTTP) request to the web server, which sends a response with HTML, CSS, and other content files to the browser. The browser then communicates with the network to ask for all the documents that make up the page. Browsers can also display other more advanced material like interactivity and animations made with JavaScript with internal JavaScript interpreters.
The first browser appeared in 1990, created by W3C Director Tim Berners-Lee. It was called The WorldWideWeb, but was renamed Nexus to avoid any confusions. Nexus was a browser-editor, allowing users to also create pages, not only browse them.
In the following years, other browsers were developed: Lynx in 1992, Mosaic in 1993, Netscape Navigator in 1994, Microsoft’s Internet Explorer in 1995, Opera in 1998, Apple’s Safari in 2003, Mozilla’s Firefox in 2004, Mobile Safari in 2007, Google Chrome in 2008, Opera Mini in 2011 and Microsoft Edge in 2015.
What is a browser extension?
As their name suggests, browser extensions are pieces of software that “extend your web browser with additional features, modify web pages, and integrate your browser with the other services you use.” Evernote, Grammarly, LastPass, JoinTabs ar a few browser extension examples.
Are browser extensions safe?
Well, as the European Union Agency for Cybersecurity notes,
Browser extensions are implemented with standard web technologies, such as HTML and JavaScript. They are written by third parties; however, not all third parties have the best interest of the end-user at heart. Malicious browser extensions are being leveraged in various types of attacks, ranging from data theft, spying, and more. Forecasts of growing security problems around extensions have materialised, as cybercriminals/rogues tap into the rich data contained in Web browsers for profit/manipulation. As the number and popularity of browser extensions grow, so too does the urgency to tackle this important attack vector. Bad programming practices and vulnerabilities also play their role in extension security […].
Malicious Chrome Extension – Some Details
As StatCounter clearly shows, Google Chrome is the most commonly used browser, so let’s see how a malicious Chrome extension can affect it.
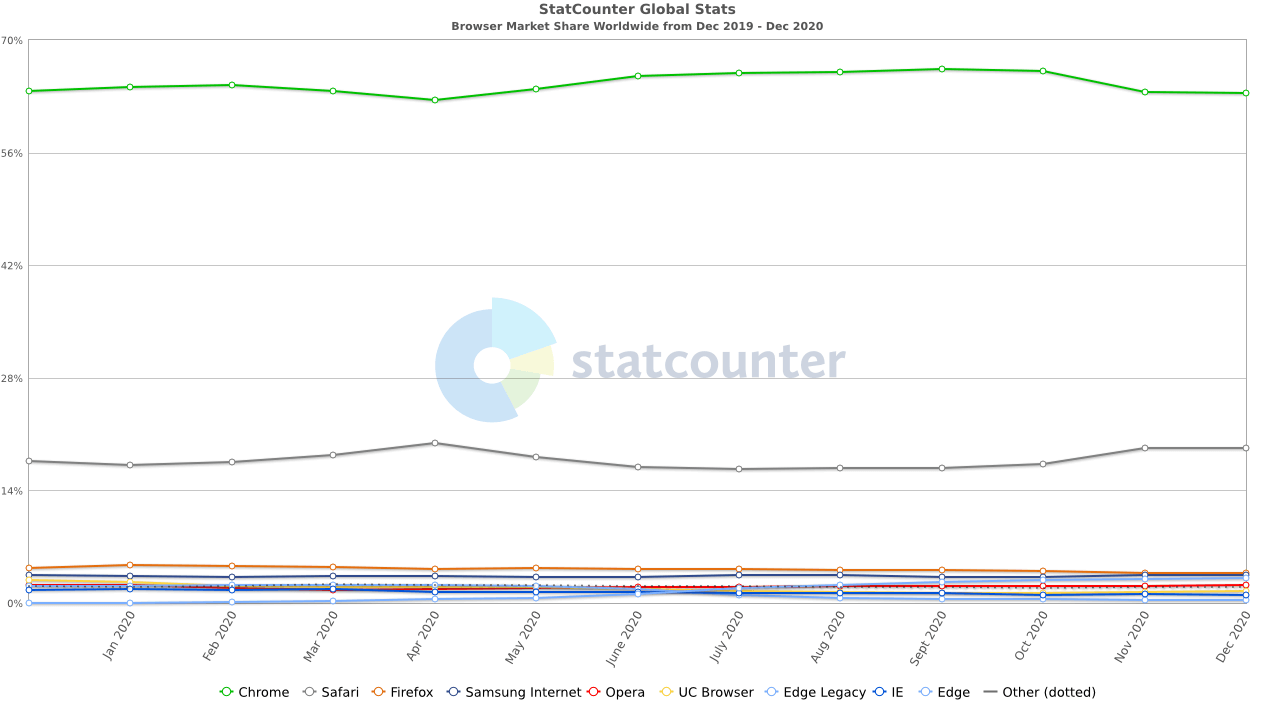
Chances are you also read this article using Chrome, so pay attention.
Nowadays, Chrome is continuously improved and runs on Windows, Linux, macOS, Android and iOS. Its extensions are “written using web technologies like HTML, JavaScript, and CSS. They are distributed through Chrome Web Store, initially known as the Google Chrome Extensions Gallery. All users with a Google Account are able to add extensions after developing them. Many Chrome extensions, once installed, have access to the user’s data. There are three levels of permissions that an app or extension may request. All extensions must have a clear and singular purpose.”
According to various investigations, a malicious Chrome extension can redirect users to ads or phishing sites, collect browsing history, collect personal data like birth dates, email addresses, active devices and even download further malware onto a device.
Malicious Chrome extensions can be created with malicious code from the start or they can be “updated” with malicious code once they gain a certain level of popularity.
Examples of a malicious Chrome extension:
The following list includes examples of Chrome extensions that proved to be malicious: “Direct Message for Instagram, DM for Instagram, Invisible mode for Instagram Direct Message, Downloader for Instagram, App Phone for Instagram, Stories for Instagram, Universal Video Downloader, Video Downloader for FaceBook™, Vimeo™ Video Downloader, Zoomer for Instagram and Facebook, VK UnBlock. Works fast., Odnoklassniki UnBlock. Works quickly, Upload photo to Instagram™, Spotify Music Downloader, The New York Times News.”
It was discovered that other Chrome extensions “contained code to bypass Google’s Chrome Web Store security scans, take screenshots, read the clipboard, harvest authentication cookies, or grab user keystrokes (such as passwords).”
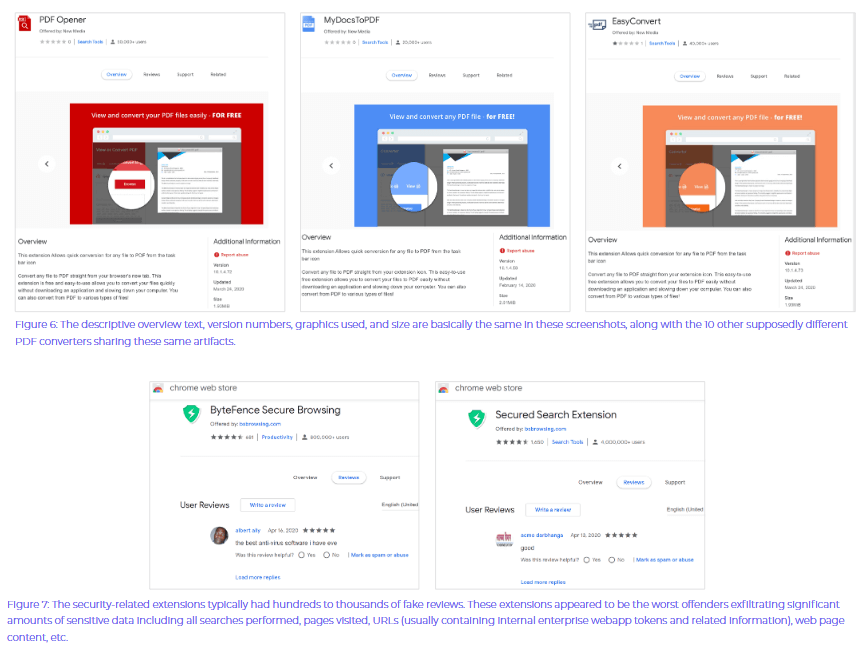
Some of these extensions, which seem to have the same codebase and graphics and probably the same creator, were discovered in the networks of companies from various domains: healthcare and pharmaceutics, oil and gas, financial services, high-tech, even higher education and government organisations.
Tom’s Guide also points out a few malicious Chrome extensions that you can check manually:
Right-click or control-click the icon of a running extension in the upper right corner of the browser, and select “Manage extensions.” A new tab will open describing the extension, and in the address bar of the tab, you’ll see something that looks like “chrome://extensions/?id=oiigbmnaadbkfbmpbfijlflahbdbdgdf.”
That long string of gibberish is a 32-character extension ID. Compare each of your extensions’ IDs to the list below, and if anything matches, remove the extension.
acmnokigkgihogfbeooklgemindnbine
apgohnlmnmkblgfplgnlmkjcpocgfomp
apjnadhmhgdobcdanndaphcpmnjbnfng
bahkljhhdeciiaodlkppoonappfnheoi
bannaglhmenocdjcmlkhkcciioaepfpj
bgffinjklipdhacmidehoncomokcmjmh
bifdhahddjbdbjmiekcnmeiffabcfjgh
bjpknhldlbknoidifkjnnkpginjgkgnm
blngdeeenccpfjbkolalandfmiinhkak
ccdfhjebekpopcelcfkpgagbehppkadi
cceejgojinihpakmciijfdgafhpchigo
cebjhmljaodmgmcaecenghhikkjdfabo
chbpnonhcgdbcpicacolalkgjlcjkbbd
cifafogcmckphmnbeipgkpfbjphmajbc
clopbiaijcfolfmjebjinippgmdkkppj
cpgoblgcfemdmaolmfhpoifikehgbjbf
dcmjopnlojhkngkmagminjbiahokmfig
deiiiklocnibjflinkfmefpofgcfhdga
dipecofobdcjnpffbkmfkdbfmjfjfgmn
dopkmmcoegcjggfanajnindneifffpck
dopmojabcdlfbnppmjeaajclohofnbol
edcepmkpdojmciieeijebkodahjfliif
ekbecnhekcpbfgdchfjcfmnocdfpcanj
elflophcopcglipligoibfejllmndhmp
eogfeijdemimhpfhlpjoifeckijeejkc
fcobokliblbalmjmahdebcdalglnieii
fgafnjobnempajahhgebbbpkpegcdlbf […]
Moreover, a malicious Chrome extension can be dangerous because it can be used as an attack vector in XSS injections. In the case of Cross-Site Scripting attacks, a malicious script is injected into otherwise benign and trusted websites.
Malicious Chrome Extension – Prevention Strategy
Having a malicious entity tracking and receiving information about your online activity is particularly dangerous for business owners and their companies. Business documents, customers details, revenue lists – employees access this kind of data and more on a daily basis. Probably online, using Office 365, Dropbox, Google Drive, and probably on Chrome. Certainly, you don’t want this data to fall in the wrong hands.
Fortunately, when Google is notified about the existence of a malicious Chrome extension, they disable it: “<<When we are alerted of extensions in the Web Store that violate our policies, we take action and use those incidents as training material to improve our automated and manual analyses>> said Scott Westover, a Google spokesperson, in a statement.”
There are also a few prevention measures you can adopt, as the European Union Agency for Cybersecurity notes:
Report suspected malicious extension behaviour to the browser store immediately.
Regularly check installed extensions, and remove those that are no longer needed. The more extensions installed, the greater the risk of malicious behaviour or a vulnerability to emerge, so keep them to a minimum.
Pay attention to the number of installs and reviews an extension has received (this information is available per extension in each browser’s store [3]). An extension with very few users (downloads), few reviews, or negative reviews, is something one should probably avoid, while an extension with a large number of users and positive reviews should be safer. Unfortunately, this isn’t always true, so always exercise caution!
Official extensions made by companies associated with a service should pose less risk, e.g. Microsoft’s or Google’s extensions are probably safer than extensions made by someone you’ve never heard of. Again this is not always true thus the user should always be cautious.
Before installing, read the information supplied with the extension, especially any permissions required, and avoid installing any extension that appears to require too many permissions or may infringe one’s privacy. Moreover, visit the developer’s website – they often provide details of the permissions.
Avoid downloading extensions outside the stores, and be extra careful if side-loading cannot be avoided.
Moreover, it’s very important to have an antivirus software with a powerful firewall installed. Our Heimdal™ Next-gen Endpoint Antivirus will help you prevent incoming attacks and isolate devices when needed.
You can find more advice on how to safely use web applications here.
Malicious Chrome Extension – Wrapping Up
Extensions can be really helpful when it comes to accomplishing our day to day tasks or just boosting our creativity, but they can also turn out to be real menaces. Always pay attention to the extensions you want to install and the permissions they request.
Also, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










