Contents:
A malware campaign distributing a malicious variant of the dnSpy app was wreaking havoc last week targeting developers and cybersec researchers. The threat actors’ goal was to perform crypto stealers, RATs, and miners’ installation.
What Happened?
Last week, a GitHub repository containing a dnSpy variant that deploys a malware cocktail was created by a threat actor. The malware range consisted of clipboard hijackers, a Quasar RAT, various payloads, and a miner. The clipboard hijackers served for cryptocurrency stealing purposes.
According to the BleepingComputer publication, MalwareHunterTeam together with 0day enthusiast discovered this malicious campaign. The researchers noticed the dnSpy project initially on https://github[.]com/carbonblackz/dnSpy/. Then it was moved to https://github[.]com/isharpdev/dnSpy.
Below there is a representation of the malicious dnSpy GitHub repository:
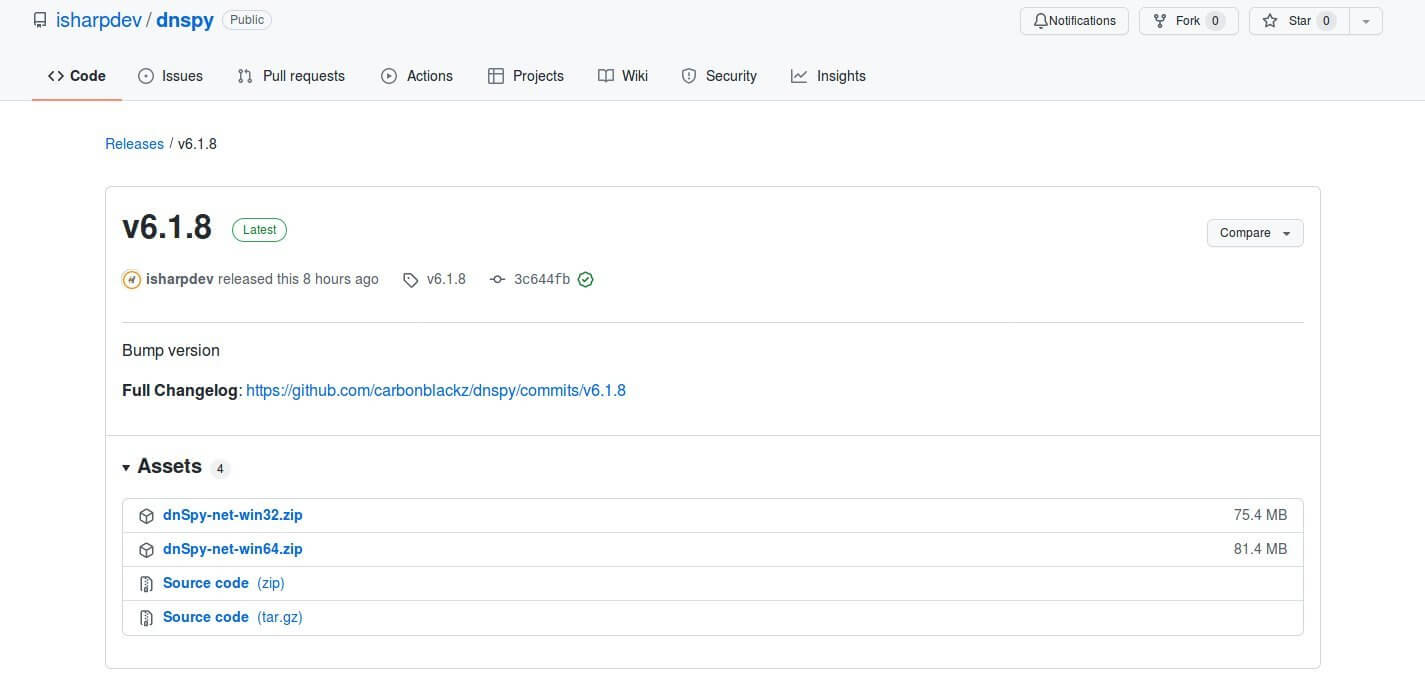
At dnSpy[.]net the hackers also built a website showing a likable design. It is reported that the site is not on anymore.
The website promotion followed steps like SEO optimization to make ednSpy[.]net rank first on Google. Other browsers like Bing, Yahoo, AOL, Yandex, and Ask.com had this domain listen on them too.
The threat actors thought of a backup plan too, as the SEO strategy was enforced with SEO ads to make the Google ranking successful.
It seems that, during the execution, the dnSpy app appears as the common application, as users are still permitted to open .NET apps, to debug them or benefit from all the usual program features.
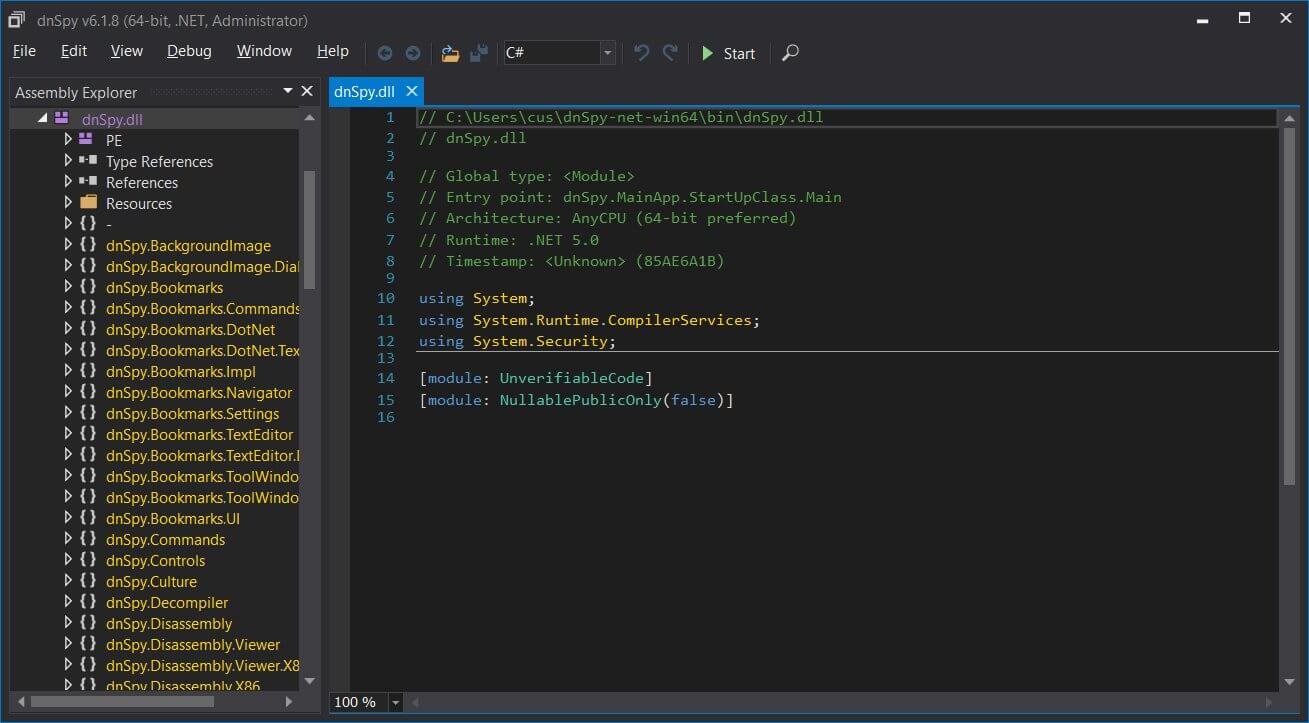
The dnSPY Executed Various Commands when Launched
Upon the launching of the dnSpy app, a series of commands are executed. These will eventually result in scheduled task creation. These tasks use elevated permission to run.
The researchers from MalwareHunterTeam shared a commands list with the same publication mentioned above that shows what types of malicious actions the malware does. Thus, it performs Microsoft Defender disablement, it downloads curl.exe to %windir%\system32\curl.exe. by means of bitsadmin.exe, then a variety of payloads are downloaded via the two previous executables in the C:\Trash folder and then they are launched. Finally, the User Account Control is disabled.
http://4api[.]net/ is the place from where those payloads were downloaded and these consist of many malware such as: %windir%\system32\curl.exe, C:\Trash\c.exe – Unknown [VirusTotal], C:\Trash\ck.exe – Unknown, C:\Trash\cbot.exe – Clipboard Hijacker [VirusTotal], C:\Trash\cbo.exe – Unknown [VirusTotal], C:\Trash\qs.exe – Quasar RAT [VirusTotal], C:\Trash\m.exe – Miner [VirusTotal], C:\Trash\d.exe, and C:\Trash\nnj.exe – Unknown.
What’s worth mentioning about clipboard hijacker (cbot.exe) is the use of cryptocurrency addresses from past cyberattacks. These are:
- Bitcoin: 175A7JNERg82zY3xwGEEMq8EyCnKn797Z4
- Ethereum: 0x4dd10a91e43bc7761e56da692471cd38c4aaa426
- Tron?: TPRNNuj6gpBQt4PLsNv7ZVeYHyRJGgJA61
- Litecoin: LQFiuJQCfRqcR9TjqYmi1ne7aANpyKdQpX
The GitHub repository and the dnSpy[.]net employed in this malicious campaign are for the moment shut down. Nevertheless, the risk of potential popular projects clones remains.
What Is dnSpy?
dnSpy stands for a well-known .NET assembly editor and debugger that serves the purpose of modifying, debugging, and decompiling .NET programs. This app is mainly used by researchers in the cybersecurity field when inspecting .NET malware.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security