Contents:
Threat actor Luna Moth is committed nowadays to targeting businesses with callback phishing campaigns, from which he already gained hundreds of thousands of dollars.
This type of cyberattack may require substantial resources but is, technically speaking, less sophisticated and has proven more effective than other types of phishing strategies.
How Can You Become a Victim of Callback Phishing Campaigns?
Callback phishing is a social engineering tactic that requires the victim to get in touch with the malicious actor by phone and benevolently reveal sensitive data to them.
At first, the victim receives an email that contains an invoice and claims that because of a supposed subscription to some service he/she is going to be automatically charged an amount of money. The message or the invoice also includes a telephone number, as from the „customer service” of a legitimate business.
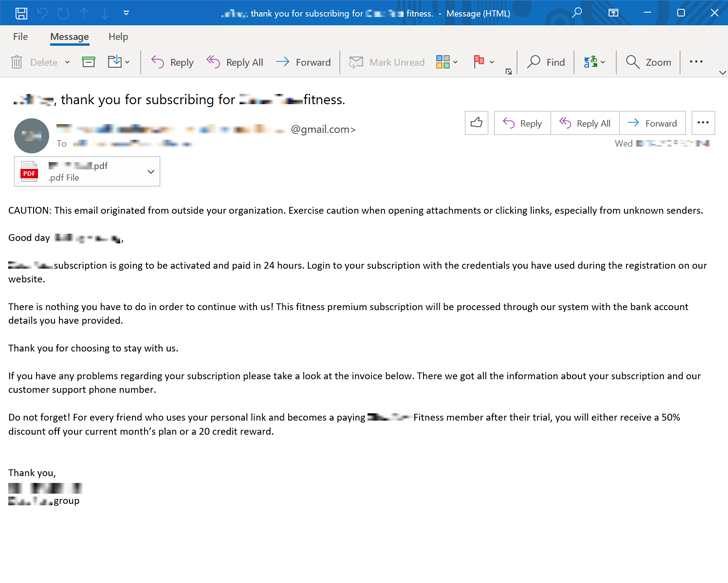
Threat actors count on the victim to call them, in order to make things clear and cancel the unwanted subscription. Further, while on the phone, the attacker in the call center tricks the victim into downloading malware or a mainstream remote access tool that would usually be harmless on their computer. From that moment on, they`re in full control of the endpoint and the data inside it.
The attacker will then seek to identify valuable information on the victim’s computer and connected file shares, and they will quietly exfiltrate it to a server they control using a file transfer tool, researcher Kristopher Russo said.
How to Recognize Callback Phishing Emails in Your Mailbox
Email messages used for callback phishing have no malicious attachment or booby-trapped link, so they seem clean enough to trick the email protection solutions. The invoice is sometimes attached as a .pdf document and at a first glance there is nothing that looks suspicious on it.
The hackers that operate callback phishing tend to avoid non-essential tools and malware – for having remote access to the victim`s endpoint they may use legitimate software – in order to mitigate the risk of detection. The unknown person on the phone insisting that you should let them install any kind of software on your device should give you a heads-up and make you think twice before you do it.
Cybersecurity awareness for employees is one of the most important security measures one could take in this case, for avoiding his business being hijacked and having his data exposed.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









