Contents:
On June 23rd, LockBit announced breaching the US Federal Reserve System, while security experts remained skeptical.
The Russian threat group claimed to exfiltrate 33 terabytes of banking information from the USA’s central bank servers. They also threatened to publish the data in the following 48 hours unless the victims would pay ransom.
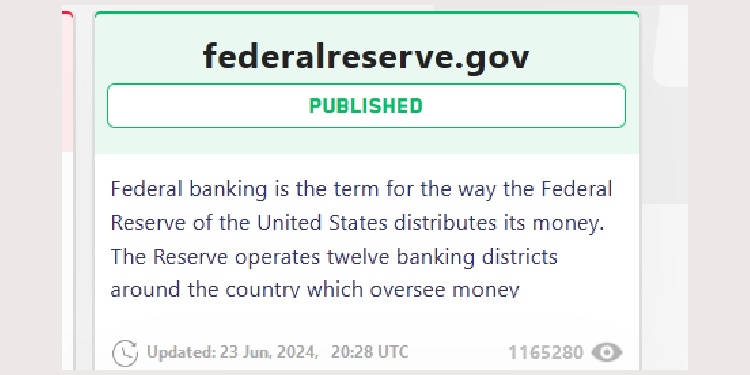
Source – Cybernews.com
After the deadline expired on June 25th, LockBit only published 21 links that held files of parent directories, torrents, and compressed archive files from Evolve Bank and Trust.
Previously this month, the US Federal Reserve had penalized Evolve Bank & Trust for
poor bank’s risk management, anti-money laundering (AML) and compliance practices
Source – Fintechfutures.com
So, for the moment, there is no proof that LockBit breached the US Federal Reserve. Consequently, the threat’s group dark web leak site is currently off.
Latest news on LockBit
In February 2024, law enforcers announced seizing LockBit’s website, infrastructure, and data.
Five days later, the threat group replicated their former website and returned to their activities.
The threat group continued their attacks and is still one of the most prolific ransomware-as-a-services. Security researchers said LockBit ransomware was linked to 28 confirmed attacks during April 2024.
At the beginning of May, the United States, United Kingdom, and Australia law enforcement revealed and sanctioned Russian Dmitry Yuryevich Khoroshev as the mastermind behind LockBit.
During the first week of June, the FBI announced distributing 7,000 decryption keys to LockBit victims.
How to prevent a LockBit attack
LockBit has faced severe blows this year, but they remain a serious threat. Enforcing endpoint security best practices and educating employees to identify phishing emails can significantly enhance a company’s security.
However, more is needed to keep LockBit hackers away.
The best way to stop them is by locking them out entirely. You can achieve this with Heimdal’s solutions.
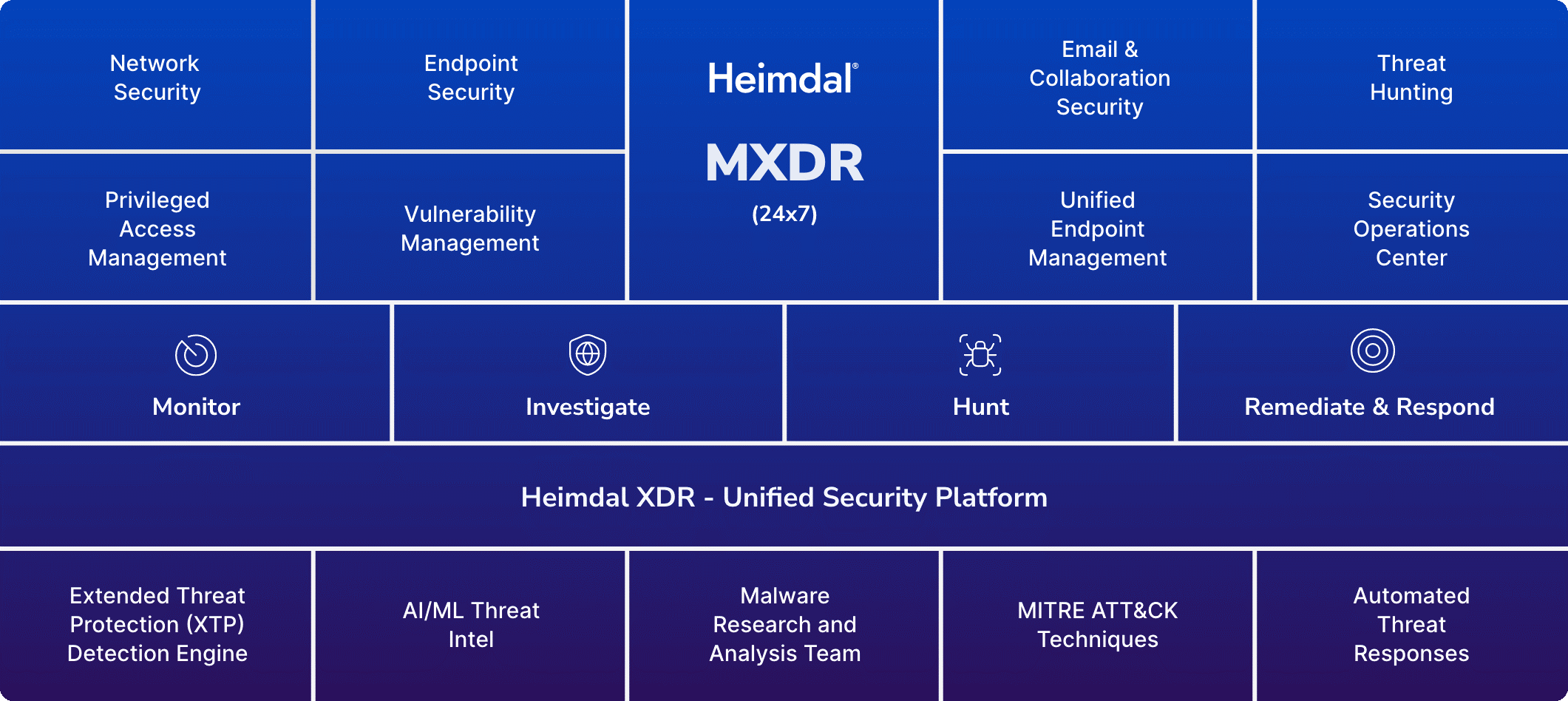
Our Extended Detection and Response (XDR) solution unifies over 11 tools into a single security platform, saving time and reducing confusion.
Here are a few examples of our standalone solutions:
- Heimdal Application Control uses Blocking Mode to stop tools like FileZilla that LockBit uses to extract data.
- Heimdal Privilege Access Management prevents admin abuses by eliminating the risk of admin compromise.
- Heimdal Patching stops LockBit from exploiting vulnerabilities.
These are just three ways we can help prevent ransomware attacks.
Many start with one to three Heimdal products and expand as they see the benefits. Tool consolidation is trending in 2024. Juggling multiple tools, reporting, and daily tasks can be challenging.
If you see value in the platform approach but lack resources to manage it, let’s talk. You could adopt Heimdal’s managed XDR service (MXDR), where our SOC team handles prevention, detection, and incident response 24/7.
Contact us for a free trial and demo.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security