Contents:
The threat actor says that the exploited Fortinet vulnerability has been patched but, many VPN credentials remain valid.
This could be considered a serious incident as the leaked VPN credentials could allow malicious actors to access a network and perform data exfiltration, install malware, and launch ransomware attacks.
The list of credentials was leaked for free by the threat actor known as ‘Orange,’ the administrator of the newly launched RAMP hacking forum and apparently a previous member of the Babuk Ransomware operation.
Recently the threat actor had made a post on the RAMP forum that contained a link to a file that was supposed to contain thousands of Fortinet VPN accounts, as simultaneously another post appeared on Groove ransomware’s data leak site promoting as well the Fortinet VPN leak.
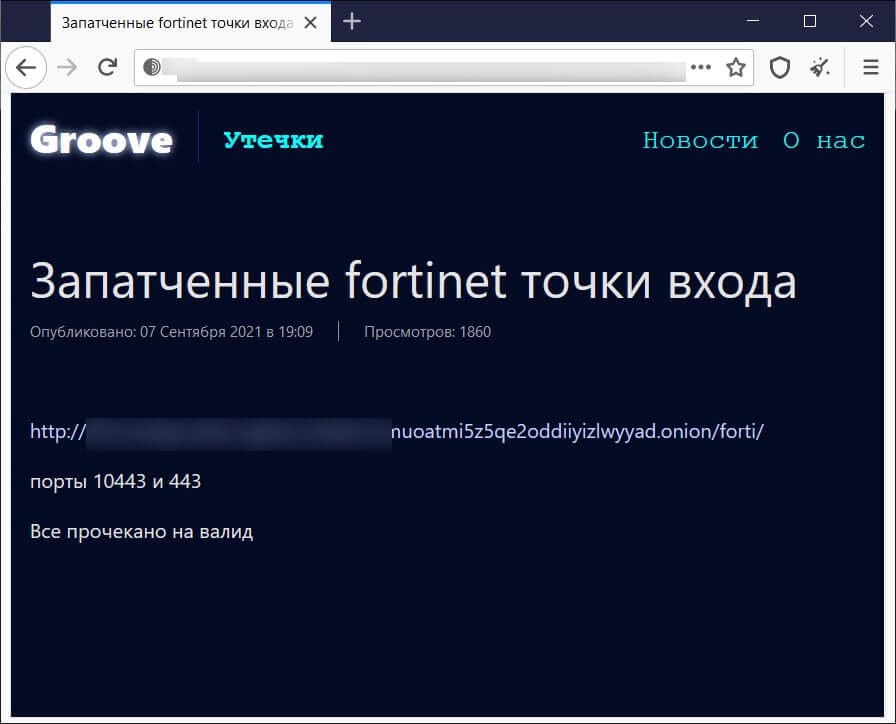
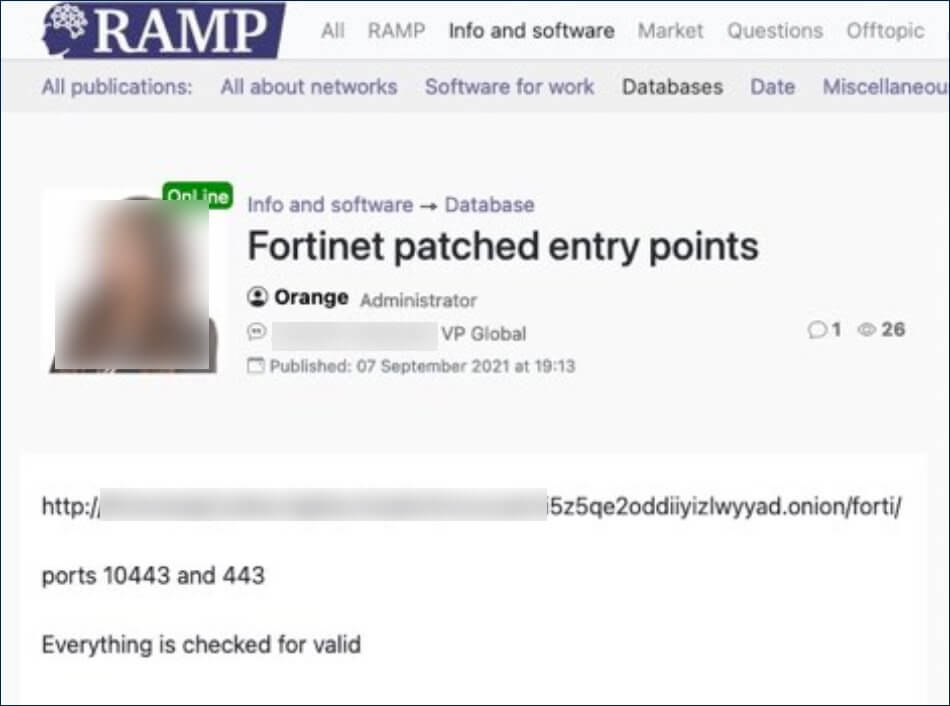
The posts lead to the same file that is hosted on a Tor storage server used by the Groove gang, which is usually used in order to host stolen files leaked in an attempt to pressure the ransomware victims to pay.
The journalists from BleepingComputer analyzed the file and discovered that it contains the VPN credentials for 498,908 users over 12,856 devices, and were able to confirm that all of the IP addresses checked were in fact Fortinet VPN servers.
It remains unclear at this time why the threat actor released the credentials rather than using them for themselves. A possible reason for this could be an attempt to promote the RAMP hacking forum and the Groove ransomware-as-a-service operation.
We believe with high confidence the VPN SSL leak was likely accomplished to promote the new RAMP ransomware forum offering a “freebie” for wannabe ransomware operators.
As Groove is a new ransomware operation with only one victim currently listed on their data leak site, they could be hoping to recruit other threat actors to their affiliate system by offering freebies.
What Can Server Admins Do?
Any Fortinet server admin should assume that many of the listed credentials are valid and take the necessary precautions and do a forced reset of all user passwords to be safe and also check the logs for possible intrusions.
Another important step that needs to be taken is to make sure they have the latest patches installed.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










