Contents:
BrickLink.com, the official second-hand and vintage marketplace for LEGO bricks, has been declared to have two API security vulnerabilities, following the discovery made by researchers from Salt Security.
BrickLink is the largest online community of LEGO fans in the world, with over one million registered members. However, members` accounts might have been at risk due to the two API security issues. Threat actors could have accessed and stolen personal information from the platform and even gain entry to the production data, thus compromising the internal servers.
More About the Vulnerabilities
Salt Security researchers discovered the vulnerabilities while looking into the user input fields on the BrickLink website. First, they noticed a cross-site scripting (XSS) flaw in the “Find Username” dialog box of the coupon search section.
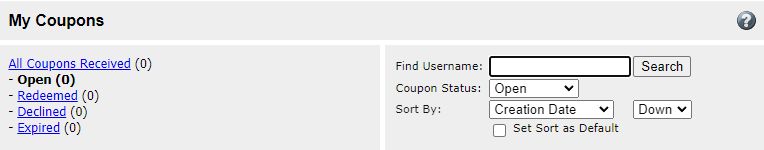
If exploited, this flaw could result in an attacker injecting and executing code on the victim`s device, by using a customized link.
Chaining the XSS vulnerability with the exposed and unprotected session ID allowed me to successfully accomplish a full account takeover.
If someone takes over a user account, they’ll be able to view all the data that has been stored on it. This includes personal information like email address, shipping address, order history, coupons, desired items and even message history.
The second flaw was located on the “Upload to Wanted List” page. Users can upload lists containing LEGO parts that they wish to find and purchase. According to the researchers, by exploiting a flaw in endpoint parsing mechanism, they were able to launch a successful XML External Entity (XXE) injection attack, adding a reference to an external entity on their file.
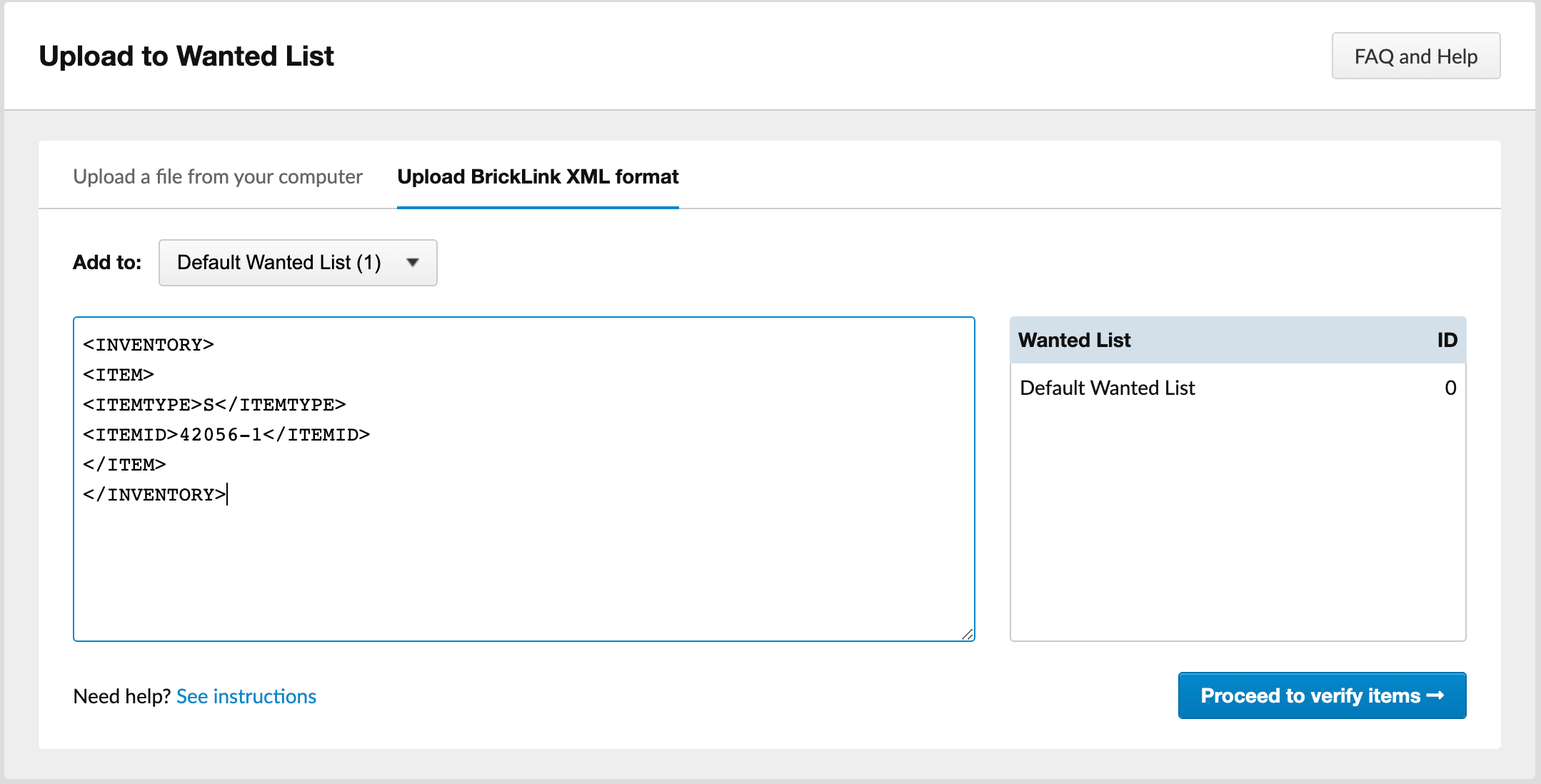
This attack enabled them to read files on the web server and execute a server-side request forgery (SSRF) attack, which could lead to exfiltrating the AWS EC2 tokens for the server.
In the report`s final notes, the research team claims they have disclosed the issue to Lego back in October 2022. Since then, the manufacturer took all the necessary steps to fix the issues.
According to BleepingComputer, cyberattacks are on the rise during the shopping season, with the retail sector being the preferred target as the focus is on the commercial aspect of the business and less on improving security.
Online shoppers should stay safe by using strong account credentials and enabling multi-factor authentication when possible. Additionally, when placing orders, a good practice would be to use guest accounts or virtual/temporary payment cards.
If you enjoyed this article, follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







