Contents:
Lazarus hacking group spreads malware using a fake cryptocurrency app called BloxHolder. This made-up brand pretends to offer cryptocurrency applications, tricking users to install AppleJeus malware.
AppleJeus malware, identified in 2018, enables the threat actors to have initial access to a network and steal crypto assets. The malware shows new evolution in the infection chain and abilities in this current campaign.
Details About the BloxHolder Campaign
The BloxHolder Campaign attributed to Lazarus by Volexity researchers spreads from June 2022 until October 2022.
Hackers used a clone of the HaasOnline platform for automated cryptocurrency trading registered under the domain bloxholder[.]com to distribute crypto-stealing malware. Users downloaded what they thought was BloxHolder app but, in fact, they got infected with the AppleJeus malware and the QTBitcoinTrader app.
Initially, the campaign used a 12.7MB Windows MSI installer for the distribution of malware, but in October 2022 it got upgraded to use Microsoft Office documents instead
A 214KB document named ‘OKX Binance & Huobi VIP fee comparision.xls’ contains a macro that creates three files on the victim’s device.
“Upon installation through the MSI infection chain, AppleJeus will create a scheduled task and drop additional files in the folder “%APPDATA%\Roaming\Bloxholder\”. Next, the malware will collect the MAC address, computer name, and OS version and send it to the C2 via a POST request, likely to identify if it’s running on a virtual machine or sandbox,” according to BleepingComputer.
The Novelty of the Campaign
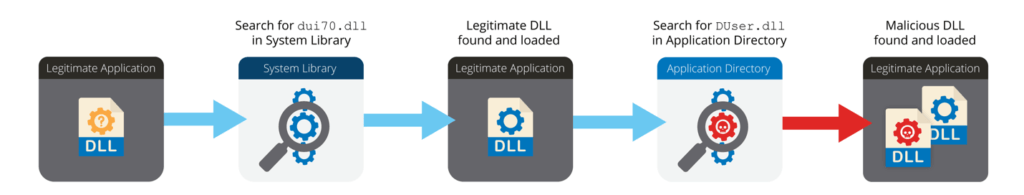
A new component of the BloxHolder campaign is the use of chained DLL sideloading for loading malware from within a legitimate process. In this way, threat actors bypass antivirus software and possibly obstruct malware investigation.
Specifically, “CameraSettingsUIHost.exe” loads the “dui70.dll” file from the “System32” directory, which then causes the loading of the malicious “DUser.dll” file from the application’s directory into the “CameraSettingsUIHost.exe” process. The “dui70.dll” file is the “Windows DirectUI Engine” and is normally installed as part of the operating system.
AppleJeus samples showed another novelty like all strings and API calls of the malware are now obscured by a specific algorithm. This practice protects them by being picked up by security software.
Find More about the Lazarus Hacking Group
The North Korean hacking group is focused on hijacking cryptocurrency, always updating its methods to reach this goal.
Lazarus is active since 2009, gaining popularity after Operation Blockbuster in which they hacked Sony Films and the WannaCry global ransomware campaign in 2017.
They also used social engineering attacks in 2021 to target security researchers, and in April 2022 they stole over $617 million worth of Ethereum and USDC tokens in an attack over Axie Infinity.
The U.S. authorities offer a reward of $5 million for any information that could help them stop the group.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









