Contents:
Lampion trojan is again in action, this time launching a large phishing campaign. The unknown threat actors behind this malware abused WeTransfer, a free-of-charge file-sharing service, using it to distribute the emails carrying the infection.
How the Phishing Campaign Works
In this new campaign, Lampion sends phishing emails to WeTransfer users encouraging them to interact with a link in order to download a “Proof of Payment” document from the platform, as discovered by Cofense.
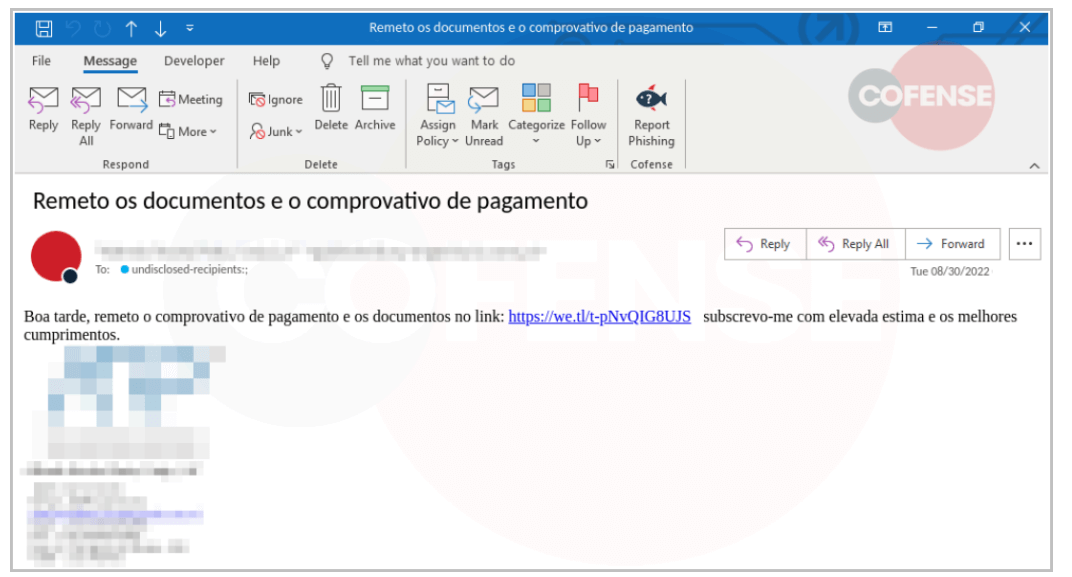
The file that is downloaded this way is a ZIP archive containing a VBS (Virtual Basic script) that once launched by the victim, will start the attack.
Upon execution, the script initiates a WScript process that creates four VBS files with random naming. The first one is empty, the second has minimal functionality, and the third’s only purpose is to launch the fourth script. Cofense analysts comment that this extra step is unclear, but modular execution approaches are typically preferred for their versatility, allowing easy file swaps.
Script number four “launches a new WScript process that connects to two hardcoded URLs to fetch two DLL files hiding inside password-protected ZIPs. The URLs point to Amazon AWS instances.”, according to BleepingComputer.
The two archives from the ZIP files contain DLL payloads and are extracted without any interaction from the user, as the passwords are already hardcoded in the script. After the DLLs are loaded into the computer’s memory, Lampion Trojan can work unknown on the infected device.
The goal of malware is to extract bank account details from the computer. Being supplied by a C2 server, the trojan mimics a login form over the original login page, so when a user enters his credentials, the fake form will send the details to the hacker.
The History of Lampion Trojan
The Lampion trojan has been first detected in 2019, when it was targeting especially Spanish-speaking entity. It was using infected servers to host its ZIPs containing the malware, and shifted to cloud services for this task in 2021. Since then it’s been abusing platforms like Google Drive and pCloud.
More recently, in March 2022, Cyware reported an uptick in the trojan’s distribution, identifying a hostname link to Bazaar and LockBit operations.
As Lampion’s creators continue to improve and extend this malware, users should be careful with every unsolicited mail they receive, even if it seems to come from a legitimate source.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







