Contents:
The Dark Pink APT has been linked to a new wave of attacks using the KamiKakaBot malware against government and military entities in Southeast Asian countries.
In January, Group-IB published an in-depth study of Dark Pink, also known as Saaiwc, detailing the group’s use of custom tools like TelePowerBot and KamiKakaBot to execute arbitrary commands and exfiltrate confidential data.
The threat actor is thought to be of Asian origin and has been active since at least mid-2021, with a spike in activity in 2022.
Cybersecurity researchers from EcleticIQ revealed, in a new report published last week, that although the new attacks are similar to the previous ones, the threat actors have refined the malware’s obfuscation routine.
The latest attacks, which took place in February 2023, were almost identical to previous attacks. In January 2023, the threat actors used ISO images to deliver KamiKakaBot, which was executed using a DLL side-loading technique. The main difference in the February campaign is that the malware’s obfuscation routine has improved to better evade anti-malware measures.
ISO Attachments and Social Engineering
The attacks use social engineering techniques and email messages with malicious attachments disguised as harmless picture files (usually in ISO format).
The ISO image contains an executable (Winword.exe), a loader (MSVCR100.dll), and a bogus Microsoft Word document, the latter of which contains the KamiKakaBot payload.
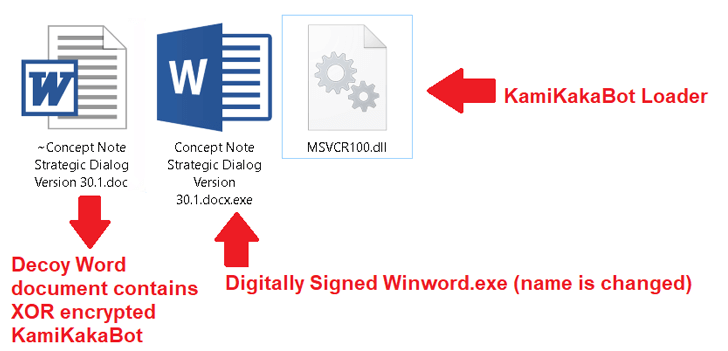
The loader is programmed to load the KamiKakaBot malware into the memory of the Winword.exe binary using the DLL side-loading method, bypassing any security measures that might otherwise be in place.
KamiKakaBot is designed primarily to steal information from infected browsers and run malicious code remotely via the Command Prompt (cmd.exe), but it also employs evasion techniques to blend in with victim environments and avoid detection.
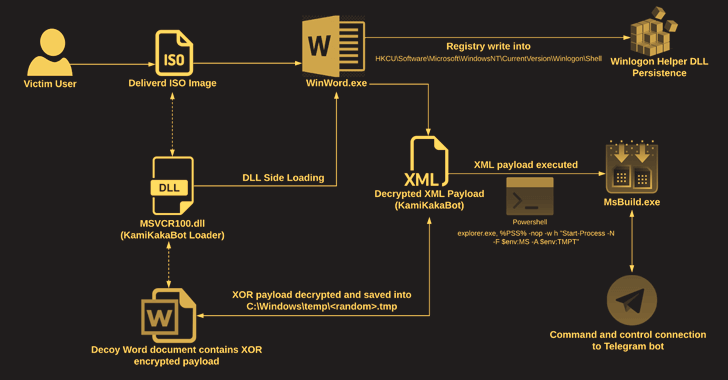
Abusing the Winlogon Helper library to alter Windows Registry keys maliciously allows the infection to remain on the vulnerable host. The information is then sent as a ZIP file to a Telegram bot, explains The Hacker News.
The use of legitimate web services as a command-and-control (C2) server, such as Telegram, remains the number one choice for different threat actors, ranging from regular cyber criminals to advanced persistent threat actors.
The researchers also note that the Dark Pink APT group is most likely a cyber espionage-motivated threat actor that “specifically exploits relations between ASEAN and European nations to create phishing lures during the February 2023 campaign”.
EclecticIQ’s full report is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










