Contents:
Conti ransomware is a malicious actor known to bring extreme prejudice to its victims. This is mainly due to the speed with which encrypts data and spreads to other systems.
The cyber-crime organization is thought to be led by a Russia-based group that goes under the pseudonym of Wizard Spider.
The group is using phishing attacks in order to install the TrickBot and BazarLoader Trojans in order to obtain remote access to the infected machines.
What Happened?
Conti’s ransomware affiliate program appears to have recently revised its business model.
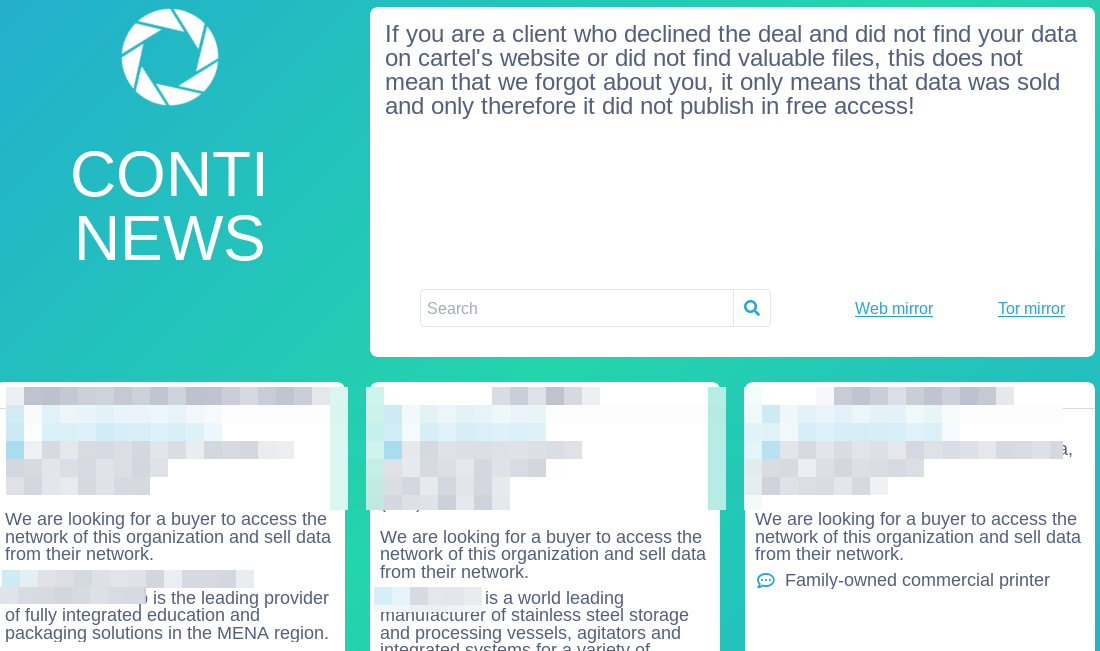
The businesses affected by Conti ransomware that refuse to pay the requested ransom have been recently listed on Conti’s victim-shaming blog. This is where confidential material collected from victims can be publicized or sold. However, the cybercriminal gang updated its victim-shaming site in the last 48 hours to reveal that it is now selling access to many of the institutions it has stolen data from.
We are looking for a buyer to access the network of this organization and sell data from their network.
At this time, it remains unclear what is the reasoning behind Conti’s action, but some researchers wonder if the ransomware operation is about to close, and is selling the data or access from an in-progress breach before they do.
The puzzling move happens as Governments in the United States and Europe work to stop some of the world’s most notorious ransomware groups. According to Reuters, the US government is behind a continuous cyber operation that has infiltrated the computer networks of REvil, a ransomware affiliate gang that is nearly as violent and brutal in dealing with victims as Conti. REvil was also one of the first ransomware gangs to start selling the data of its victims.
Conti’s apparent new orientation might be nothing more than a ruse to get victims to negotiate, as in “pay up or someone will pay for your data or you will suffer long-term suffering if you don’t.”
Could This Be a Translation Error?
Perhaps something got lost when translating from Russian to English and the ransomware group is just trying to align its activities with many other ransomware affiliate programs that have recently focused on extorting companies in exchange for a pledge not to publish or sell stolen data.
This is done by changing from the deployment of a ransomware virus to the actual sale of stolen data and access to the victim’s network.
However, it looks like the Conti ransomware subject will remain a hot topic.
There are further hypotheses out there, some including that Conti has actually spread too thin and are trying to concentrate their efforts, or that it will do a “rebranding” and come back stronger under a new name.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








